OSI vs TCP/IP Model
Networking isn’t just about cables and connections – it’s about models that define how data travels from one point to another. Understanding these models is the first step to mastering networking and cybersecurity fundamentals.
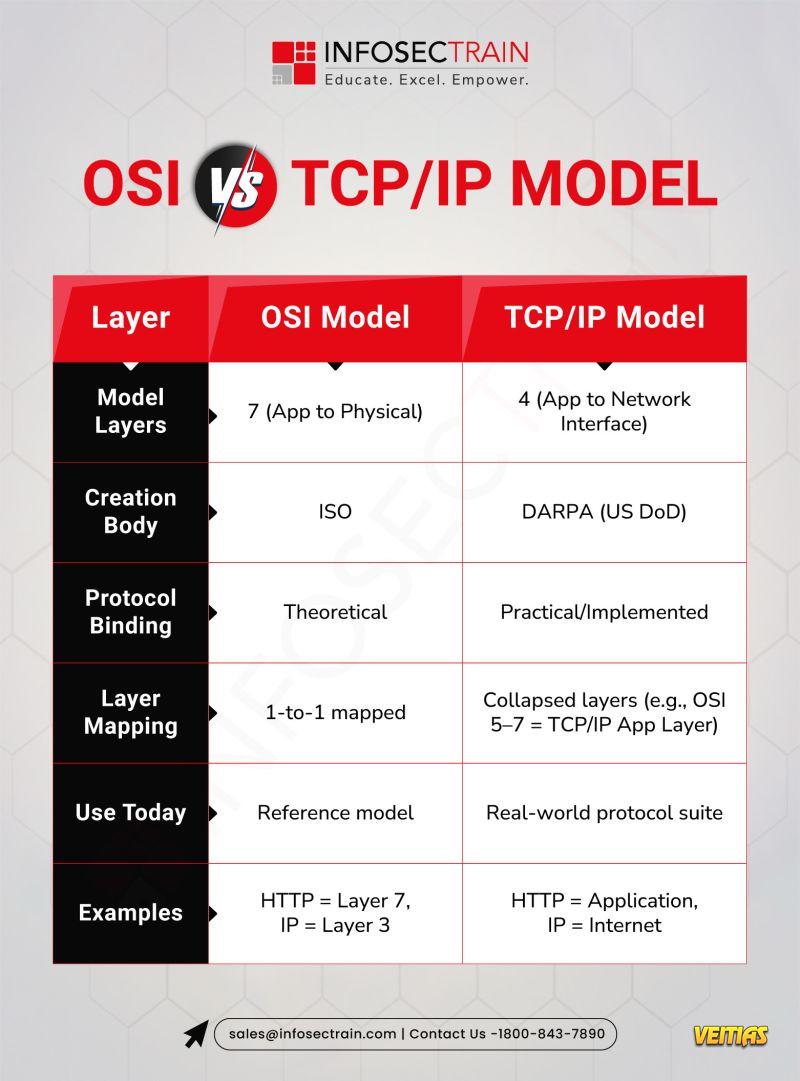
Key Difference: OSI = Reference | TCP/IP = Implementation
To Know More, Check This Out: https://www.infosectrain.com/blog/osi-model-vs-tcp-ip-model/
#Networking #OSIModel #TCPIPModel #CyberSecurity #TechSimplified #NetworkingBasics #InfoSecTrain #CyberAwareness #TechKnowledge #ProtocolStack #Internet #NetworkingTips #ITTraining #NetworkingFundamentals
Networking isn’t just about cables and connections – it’s about models that define how data travels from one point to another. Understanding these models is the first step to mastering networking and cybersecurity fundamentals.
Key Difference: OSI = Reference | TCP/IP = Implementation
To Know More, Check This Out: https://www.infosectrain.com/blog/osi-model-vs-tcp-ip-model/
#Networking #OSIModel #TCPIPModel #CyberSecurity #TechSimplified #NetworkingBasics #InfoSecTrain #CyberAwareness #TechKnowledge #ProtocolStack #Internet #NetworkingTips #ITTraining #NetworkingFundamentals
OSI vs TCP/IP Model
Networking isn’t just about cables and connections – it’s about models that define how data travels from one point to another. Understanding these models is the first step to mastering networking and cybersecurity fundamentals.
👉 Key Difference: OSI = Reference | TCP/IP = Implementation
To Know More, Check This Out: https://www.infosectrain.com/blog/osi-model-vs-tcp-ip-model/
#Networking #OSIModel #TCPIPModel #CyberSecurity #TechSimplified #NetworkingBasics #InfoSecTrain #CyberAwareness #TechKnowledge #ProtocolStack #Internet #NetworkingTips #ITTraining #NetworkingFundamentals
0 Comentários
0 Compartilhamentos
5092 Visualizações
0 Anterior