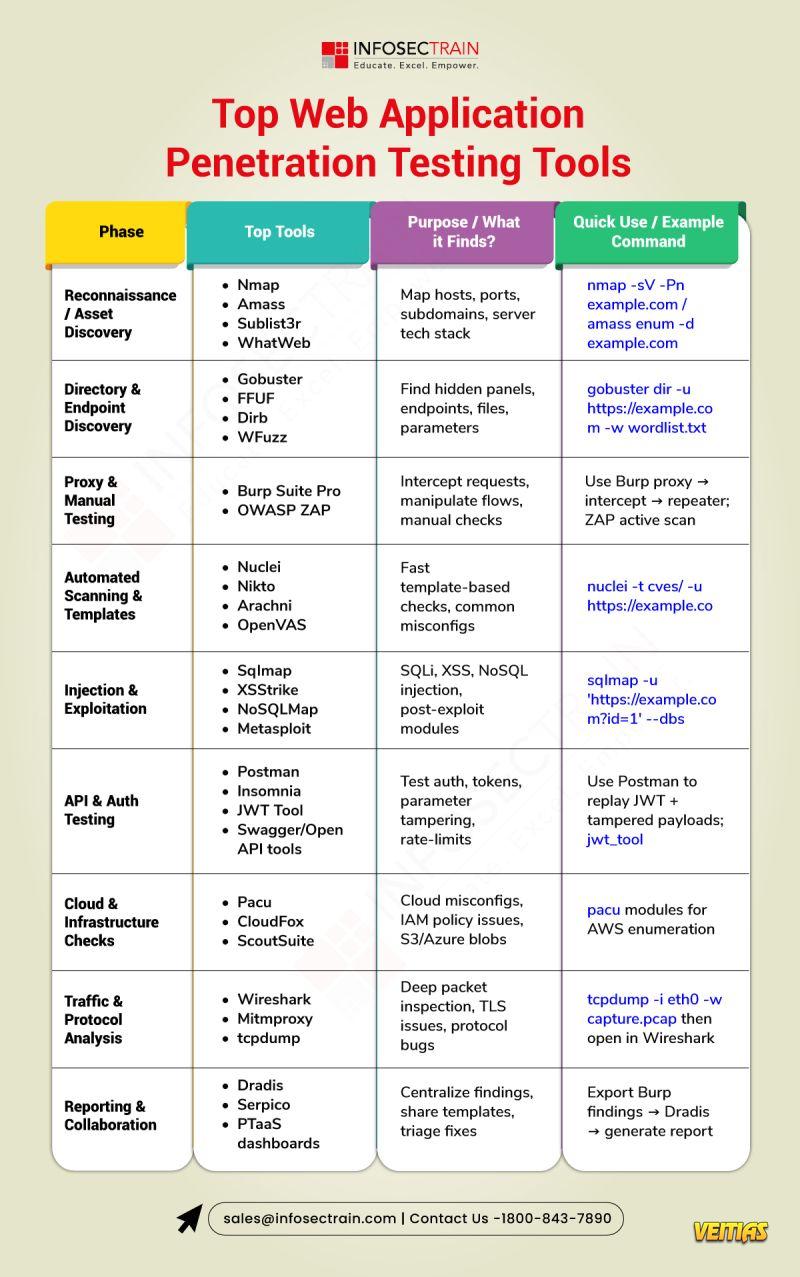
Top web application penetration testing tools help security pros find and exploit vulnerabilities quickly and reliably. Tools like Burp Suite, OWASP ZAP, sqlmap, Nmap, Metasploit, Nikto, and ffuf automate scanning, fuzzing, SQL injection discovery, and reconnaissance while providing manual testing support and powerful workflows for exploitation and verification. Using a mix of these tools—alongside careful manual analysis—lets testers simulate real attacks, prioritize findings, and provide actionable remediation for developers.
Top web application penetration testing tools help security pros find and exploit vulnerabilities quickly and reliably. Tools like Burp Suite, OWASP ZAP, sqlmap, Nmap, Metasploit, Nikto, and ffuf automate scanning, fuzzing, SQL injection discovery, and reconnaissance while providing manual testing support and powerful workflows for exploitation and verification. Using a mix of these tools—alongside careful manual analysis—lets testers simulate real attacks, prioritize findings, and provide actionable remediation for developers.
0 Commenti
0 condivisioni
2406 Views
0 Anteprima