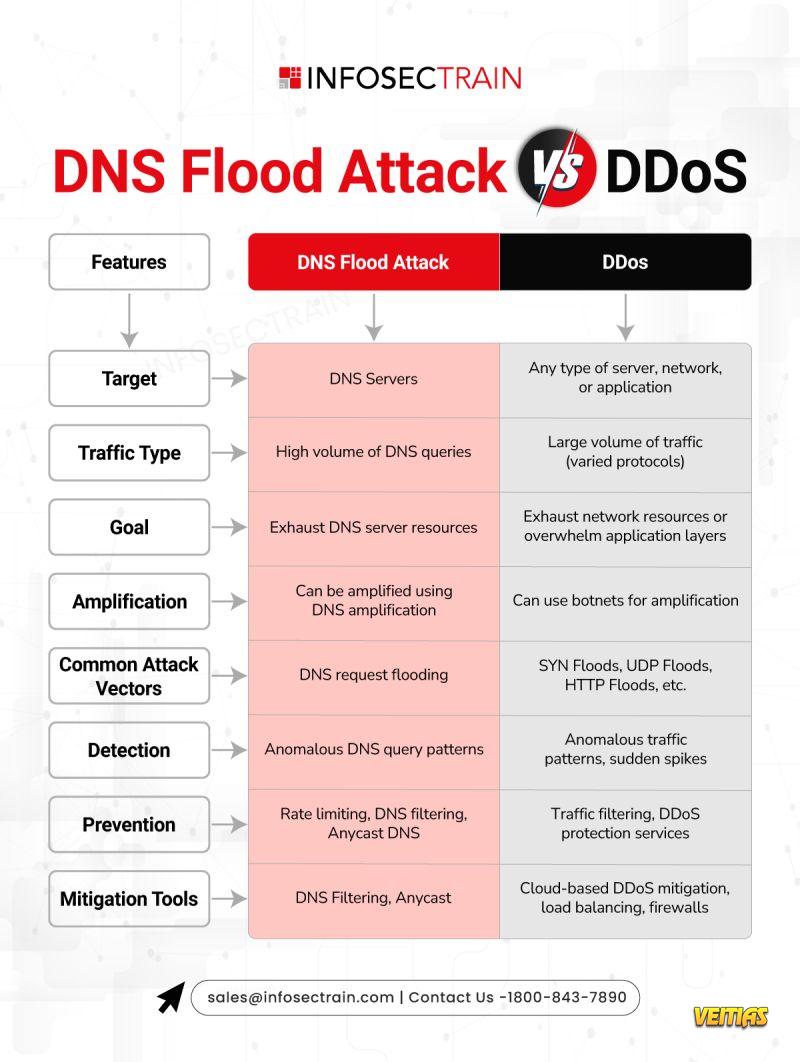
DNS Flood Attack vs. DDoS
Both are powerful cyber threats designed to crash your services—but what sets them apart?
DNS Flood Attack: A focused denial-of-service attack targeting DNS servers with bogus traffic, causing domain resolution failures.
DDoS (Distributed Denial of Service): A large-scale assault using multiple devices to overload and shut down networks or services.
Key Distinctions
DNS Flood = DNS-targeted disruption
DDoS = Massive, multi-layered assault
Both = Serious threats needing immediate action!
#DNSFlood #DDoSAttack #CyberSecurity #NetworkProtection #DNSDefense #InfosecInsights #TechSecurity #ITDefense #CyberThreats #OnlineProtection #StayCyberSafe #CyberAware #DigitalDefense #ThreatPrevention #SecureYourNetwork #infosectrain
Both are powerful cyber threats designed to crash your services—but what sets them apart?
DNS Flood Attack: A focused denial-of-service attack targeting DNS servers with bogus traffic, causing domain resolution failures.
DDoS (Distributed Denial of Service): A large-scale assault using multiple devices to overload and shut down networks or services.
Key Distinctions
DNS Flood = DNS-targeted disruption
DDoS = Massive, multi-layered assault
Both = Serious threats needing immediate action!
#DNSFlood #DDoSAttack #CyberSecurity #NetworkProtection #DNSDefense #InfosecInsights #TechSecurity #ITDefense #CyberThreats #OnlineProtection #StayCyberSafe #CyberAware #DigitalDefense #ThreatPrevention #SecureYourNetwork #infosectrain
DNS Flood Attack vs. DDoS
Both are powerful cyber threats designed to crash your services—but what sets them apart?
✅ DNS Flood Attack: A focused denial-of-service attack targeting DNS servers with bogus traffic, causing domain resolution failures.
✅ DDoS (Distributed Denial of Service): A large-scale assault using multiple devices to overload and shut down networks or services.
🎯 Key Distinctions
✅ DNS Flood = DNS-targeted disruption
✅ DDoS = Massive, multi-layered assault
✅ Both = Serious threats needing immediate action!
#DNSFlood #DDoSAttack #CyberSecurity #NetworkProtection #DNSDefense #InfosecInsights #TechSecurity #ITDefense #CyberThreats #OnlineProtection #StayCyberSafe #CyberAware #DigitalDefense #ThreatPrevention #SecureYourNetwork #infosectrain
0 Comentários
0 Compartilhamentos
16326 Visualizações
0 Anterior