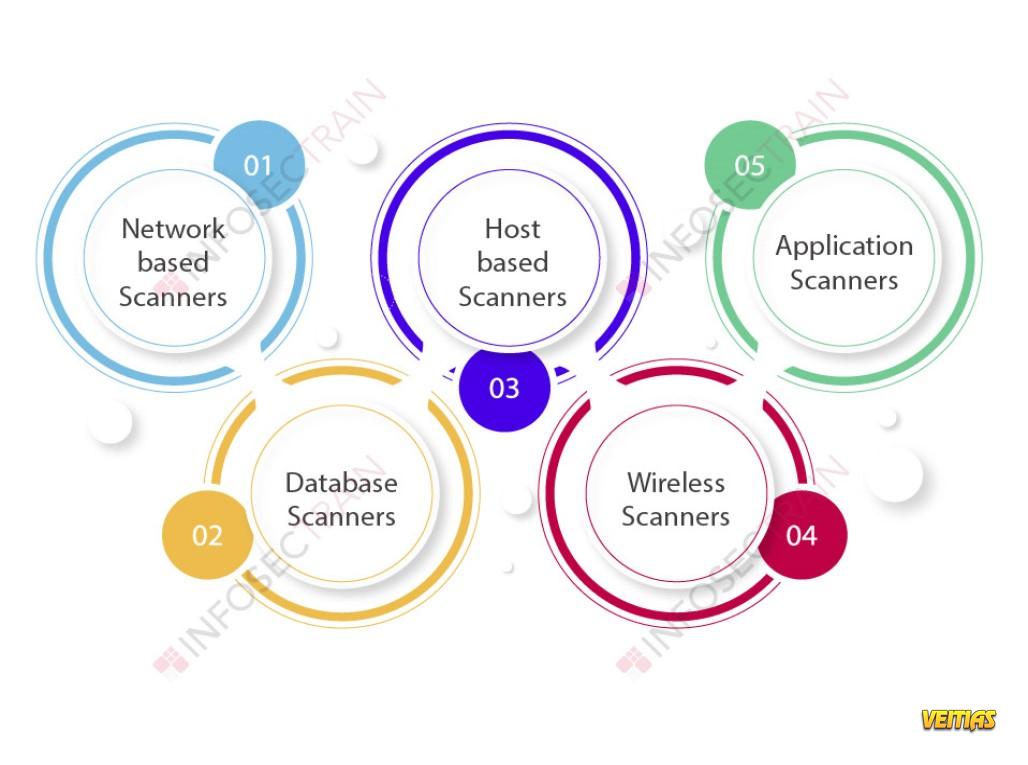
What are the Benefits of Threat Modeling?
Discover how threat modeling can help identify and eliminate vulnerabilities within your IT environment. By pinpointing backdoors and unnecessary endpoints, organizations can significantly reduce their attack surface and enhance overall security.
Read Here: https://infosec-train.blogspot.com/2024/07/what-are-benefits-of-threat-modeling.html
#ThreatModeling #CyberSecurity #RiskManagement #InfoSec #ThreatAnalysis #CyberDefense #SecurityPlanning #ITSecurity #VulnerabilityManagement #SecurityArchitecture #CyberRisk #ApplicationSecurity #SecurityBestPractices #ProactiveSecurity #RiskMitigation #infosectrain
Discover how threat modeling can help identify and eliminate vulnerabilities within your IT environment. By pinpointing backdoors and unnecessary endpoints, organizations can significantly reduce their attack surface and enhance overall security.
Read Here: https://infosec-train.blogspot.com/2024/07/what-are-benefits-of-threat-modeling.html
#ThreatModeling #CyberSecurity #RiskManagement #InfoSec #ThreatAnalysis #CyberDefense #SecurityPlanning #ITSecurity #VulnerabilityManagement #SecurityArchitecture #CyberRisk #ApplicationSecurity #SecurityBestPractices #ProactiveSecurity #RiskMitigation #infosectrain
What are the Benefits of Threat Modeling?
Discover how threat modeling can help identify and eliminate vulnerabilities within your IT environment. By pinpointing backdoors and unnecessary endpoints, organizations can significantly reduce their attack surface and enhance overall security.
Read Here: https://infosec-train.blogspot.com/2024/07/what-are-benefits-of-threat-modeling.html
#ThreatModeling #CyberSecurity #RiskManagement #InfoSec #ThreatAnalysis #CyberDefense #SecurityPlanning #ITSecurity #VulnerabilityManagement #SecurityArchitecture #CyberRisk #ApplicationSecurity #SecurityBestPractices #ProactiveSecurity #RiskMitigation #infosectrain
0 Yorumlar
0 hisse senetleri
11927 Views
0 önizleme