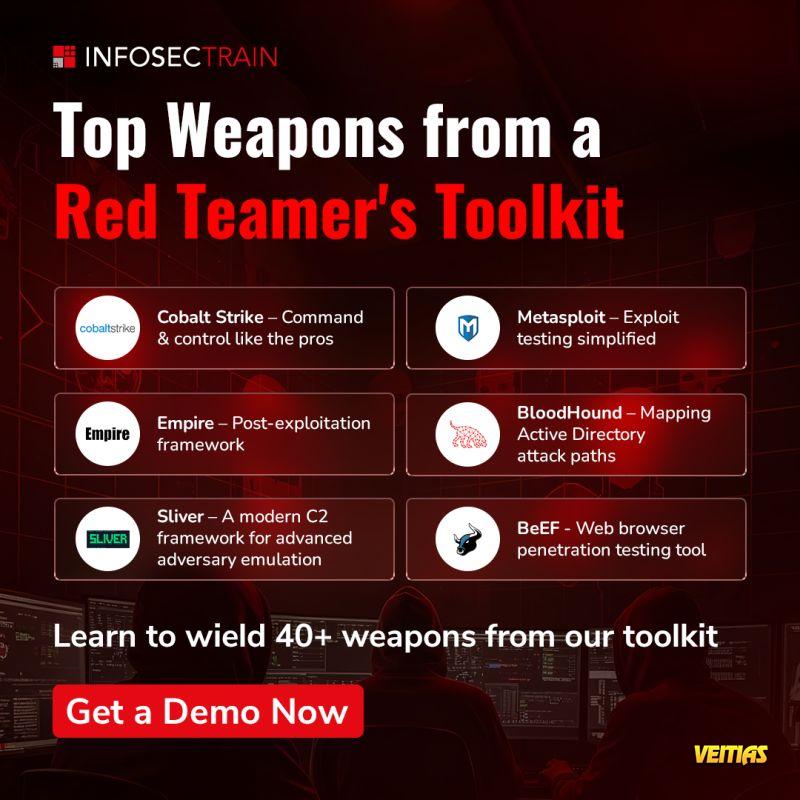
Top Weapons from a Red Teamer's Toolkit
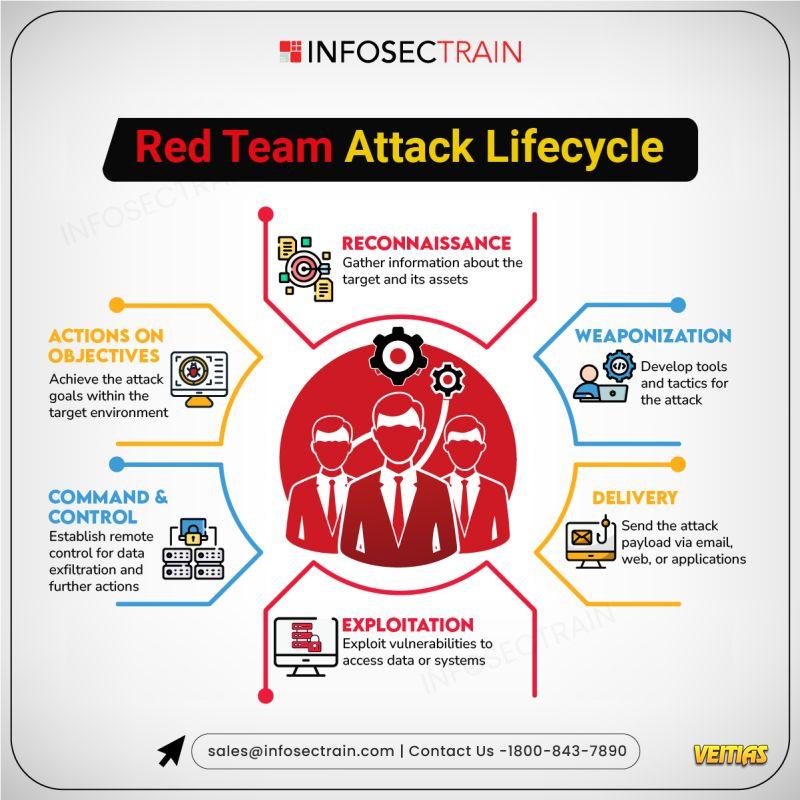
Ever wondered how ethical hackers test the strength of your defenses? Red Teamers use a variety of tools to simulate real-world attacks and identify vulnerabilities before the bad guys do. Mastering these tools helps organizations identify weaknesses before attackers do.
Enroll Here: https://www.infosectrain.com/courses/advanced-penetration-testing-online-training-course/
#RedTeam #CyberSecurity #EthicalHacking #PenTesting #InfosecTrain #Metasploit #Nmap #CobaltStrike #BurpSuite #Wireshark #CyberDefense #InfoSec #HackerMindset #ThreatSimulation
Ever wondered how ethical hackers test the strength of your defenses? Red Teamers use a variety of tools to simulate real-world attacks and identify vulnerabilities before the bad guys do. Mastering these tools helps organizations identify weaknesses before attackers do.
Enroll Here: https://www.infosectrain.com/courses/advanced-penetration-testing-online-training-course/
#RedTeam #CyberSecurity #EthicalHacking #PenTesting #InfosecTrain #Metasploit #Nmap #CobaltStrike #BurpSuite #Wireshark #CyberDefense #InfoSec #HackerMindset #ThreatSimulation
Top Weapons from a Red Teamer's Toolkit
Ever wondered how ethical hackers test the strength of your defenses? Red Teamers use a variety of tools to simulate real-world attacks and identify vulnerabilities before the bad guys do. Mastering these tools helps organizations identify weaknesses before attackers do.
Enroll Here: https://www.infosectrain.com/courses/advanced-penetration-testing-online-training-course/
#RedTeam #CyberSecurity #EthicalHacking #PenTesting #InfosecTrain #Metasploit #Nmap #CobaltStrike #BurpSuite #Wireshark #CyberDefense #InfoSec #HackerMindset #ThreatSimulation
0 Σχόλια
0 Μοιράστηκε
3232 Views
0 Προεπισκόπηση