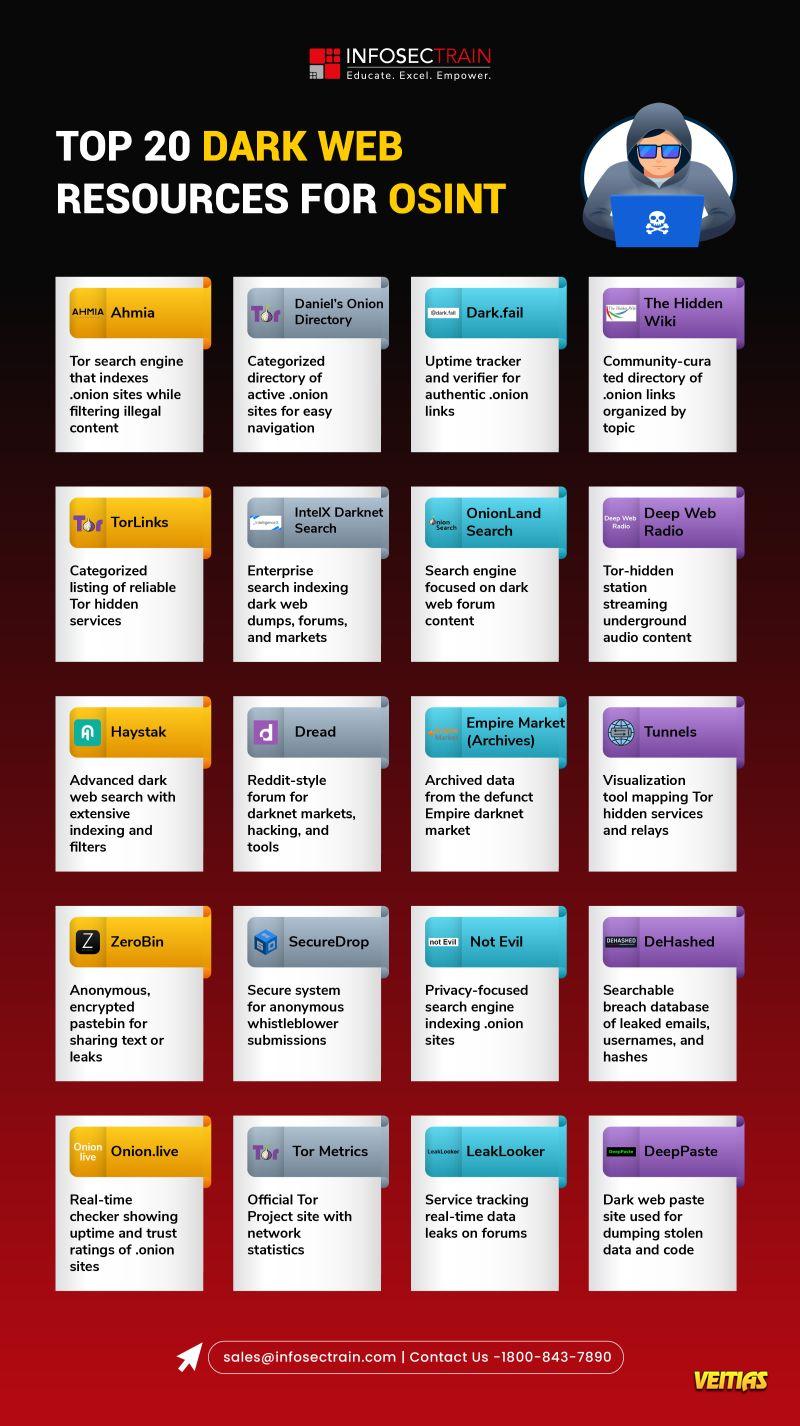
The dark web hosts a wide range of hidden resources that are valuable for Open-Source Intelligence (OSINT) investigations. From underground forums, leak sites, and marketplaces to specialized search engines and databases, these resources provide insights into cybercriminal activities, data breaches, and threat actors. Exploring the Top 20 Dark Web Resources for OSINT helps security professionals, researchers, and investigators gather actionable intelligence, strengthen threat detection, and improve overall cybersecurity strategies.
The dark web hosts a wide range of hidden resources that are valuable for Open-Source Intelligence (OSINT) investigations. From underground forums, leak sites, and marketplaces to specialized search engines and databases, these resources provide insights into cybercriminal activities, data breaches, and threat actors. Exploring the Top 20 Dark Web Resources for OSINT helps security professionals, researchers, and investigators gather actionable intelligence, strengthen threat detection, and improve overall cybersecurity strategies.
0 Commentarios
0 Acciones
1651 Views
0 Vista previa