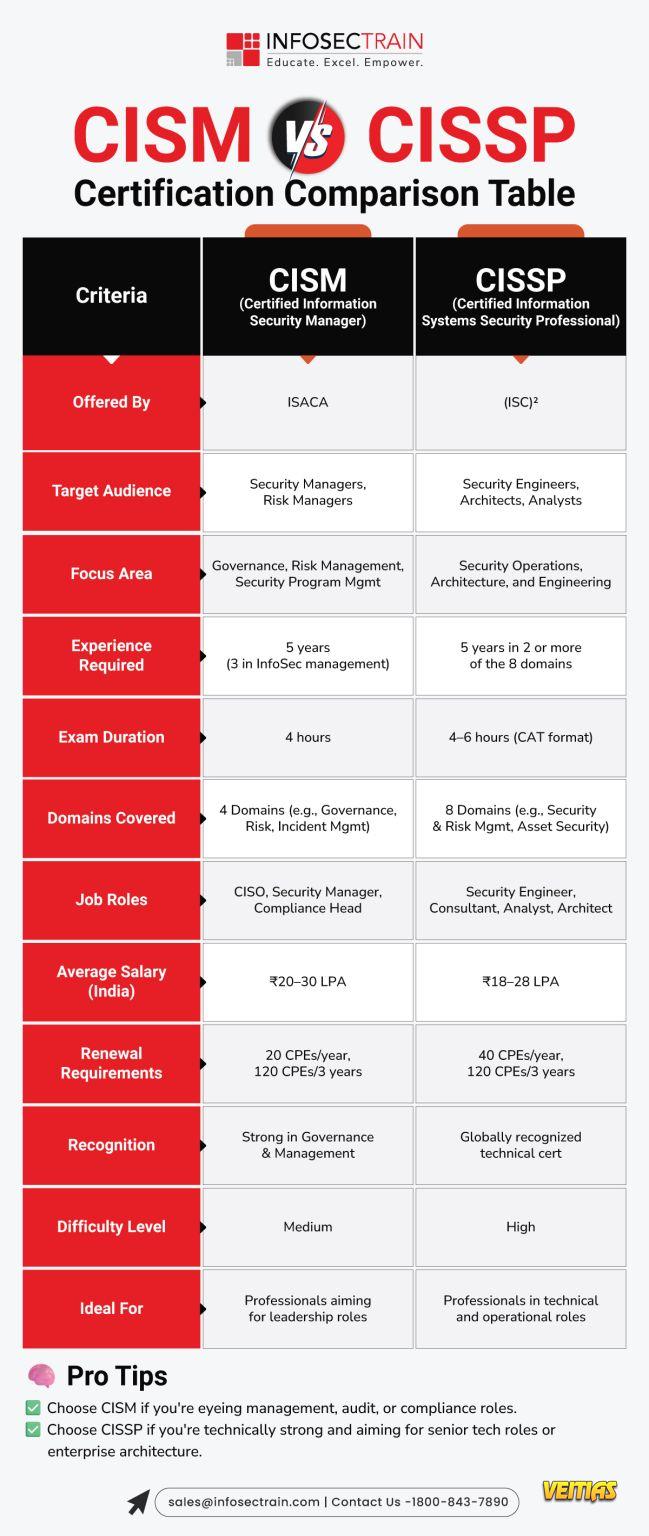
CISM vs CISSP: Which Cybersecurity Certification Should You Choose?
Choosing between CISM and CISSP can feel like decoding a security puzzle — both are powerful, both are respected, and both open doors to high-impact cybersecurity roles.
To make it easier, here’s a clear comparison table breaking down what truly matters:
✔ Focus Areas
✔ Target Audience
✔ Exam Structure
✔ Job Roles
✔ Who Should Choose What
visit InfosecTrain to explore training options.
#CISM #CISSP #CyberSecurityCareers #InfoSecTrain #CybersecurityTraining #ITSecurity #CyberRisk #SecurityLeadership #ISACA #ISC2 #CareerGrowth #SecurityCertifications
Choosing between CISM and CISSP can feel like decoding a security puzzle — both are powerful, both are respected, and both open doors to high-impact cybersecurity roles.
To make it easier, here’s a clear comparison table breaking down what truly matters:
✔ Focus Areas
✔ Target Audience
✔ Exam Structure
✔ Job Roles
✔ Who Should Choose What
visit InfosecTrain to explore training options.
#CISM #CISSP #CyberSecurityCareers #InfoSecTrain #CybersecurityTraining #ITSecurity #CyberRisk #SecurityLeadership #ISACA #ISC2 #CareerGrowth #SecurityCertifications
🔐 CISM vs CISSP: Which Cybersecurity Certification Should You Choose?
Choosing between CISM and CISSP can feel like decoding a security puzzle — both are powerful, both are respected, and both open doors to high-impact cybersecurity roles.
To make it easier, here’s a clear comparison table breaking down what truly matters:
✔ Focus Areas
✔ Target Audience
✔ Exam Structure
✔ Job Roles
✔ Who Should Choose What
👉visit InfosecTrain to explore training options.
#CISM #CISSP #CyberSecurityCareers #InfoSecTrain #CybersecurityTraining #ITSecurity #CyberRisk #SecurityLeadership #ISACA #ISC2 #CareerGrowth #SecurityCertifications
0 Commentarii
0 Distribuiri
1384 Views
0 previzualizare