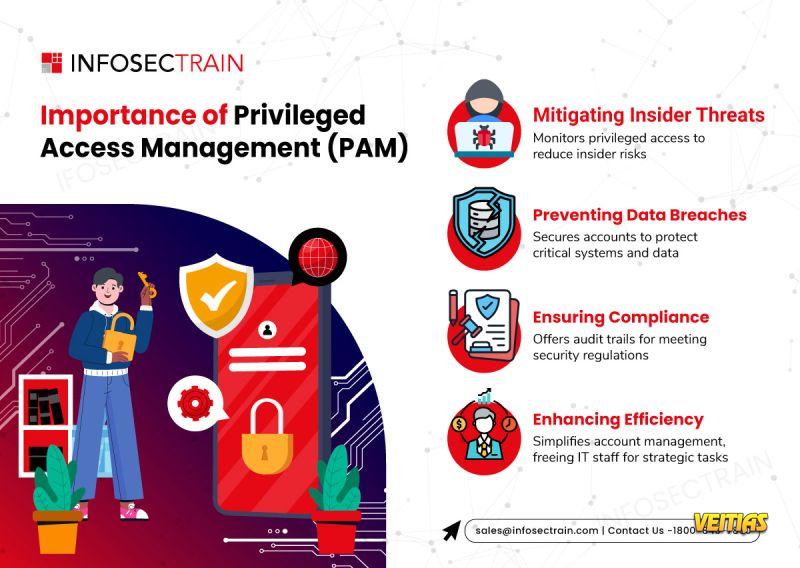
ISC2 ISSAP Domain 4.4.3: Architect Identity Authorization
If your security strategy depends on “trusted users,” you’re already exposed.
Modern breaches don’t break in they log in.
𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐢𝐬 𝐭𝐡𝐞 𝐧𝐞𝐰 𝐩𝐞𝐫𝐢𝐦𝐞𝐭𝐞𝐫, 𝐚𝐧𝐝 𝐚𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐚𝐭𝐢𝐨𝐧 𝐢𝐬 𝐭𝐡𝐞 𝐰𝐞𝐚𝐤𝐞𝐬𝐭 𝐥𝐢𝐧𝐤 𝐢𝐧 𝐦𝐨𝐬𝐭 𝐞𝐧𝐯𝐢𝐫𝐨𝐧𝐦𝐞𝐧𝐭𝐬.
𝐓𝐨𝐨 𝐦𝐚𝐧𝐲 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐬 𝐬𝐭𝐢𝐥𝐥 𝐛𝐞𝐥𝐢𝐞𝐯𝐞:
Compliance = Security
Certifications = Readiness
Admin access = Productivity
A real Security Architect knows better.
𝐒𝐭𝐫𝐨𝐧𝐠 𝐚𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐚𝐭𝐢𝐨𝐧 𝐦𝐞𝐚𝐧𝐬:
✔ Least Privilege everywhere
✔ No single person controls an entire process
✔ Service accounts treated as first-class risks
✔ PAM with Just-in-Time access, not permanent power
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐟𝐮𝐥𝐥 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/isc2-issap-domain-4-4-3-architect-identity-authorization
#CyberSecurity #ISSAP #IAM #ZeroTrust #SecurityLeadership #PrivilegedAccessManagement #InfosecTrain
If your security strategy depends on “trusted users,” you’re already exposed.
Modern breaches don’t break in they log in.
𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐢𝐬 𝐭𝐡𝐞 𝐧𝐞𝐰 𝐩𝐞𝐫𝐢𝐦𝐞𝐭𝐞𝐫, 𝐚𝐧𝐝 𝐚𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐚𝐭𝐢𝐨𝐧 𝐢𝐬 𝐭𝐡𝐞 𝐰𝐞𝐚𝐤𝐞𝐬𝐭 𝐥𝐢𝐧𝐤 𝐢𝐧 𝐦𝐨𝐬𝐭 𝐞𝐧𝐯𝐢𝐫𝐨𝐧𝐦𝐞𝐧𝐭𝐬.
𝐓𝐨𝐨 𝐦𝐚𝐧𝐲 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐬 𝐬𝐭𝐢𝐥𝐥 𝐛𝐞𝐥𝐢𝐞𝐯𝐞:
Compliance = Security
Certifications = Readiness
Admin access = Productivity
A real Security Architect knows better.
𝐒𝐭𝐫𝐨𝐧𝐠 𝐚𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐚𝐭𝐢𝐨𝐧 𝐦𝐞𝐚𝐧𝐬:
✔ Least Privilege everywhere
✔ No single person controls an entire process
✔ Service accounts treated as first-class risks
✔ PAM with Just-in-Time access, not permanent power
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐟𝐮𝐥𝐥 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/isc2-issap-domain-4-4-3-architect-identity-authorization
#CyberSecurity #ISSAP #IAM #ZeroTrust #SecurityLeadership #PrivilegedAccessManagement #InfosecTrain
ISC2 ISSAP Domain 4.4.3: Architect Identity Authorization
If your security strategy depends on “trusted users,” you’re already exposed.
Modern breaches don’t break in ➡️they log in.
✅ 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐢𝐬 𝐭𝐡𝐞 𝐧𝐞𝐰 𝐩𝐞𝐫𝐢𝐦𝐞𝐭𝐞𝐫, 𝐚𝐧𝐝 𝐚𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐚𝐭𝐢𝐨𝐧 𝐢𝐬 𝐭𝐡𝐞 𝐰𝐞𝐚𝐤𝐞𝐬𝐭 𝐥𝐢𝐧𝐤 𝐢𝐧 𝐦𝐨𝐬𝐭 𝐞𝐧𝐯𝐢𝐫𝐨𝐧𝐦𝐞𝐧𝐭𝐬.
𝐓𝐨𝐨 𝐦𝐚𝐧𝐲 𝐨𝐫𝐠𝐚𝐧𝐢𝐳𝐚𝐭𝐢𝐨𝐧𝐬 𝐬𝐭𝐢𝐥𝐥 𝐛𝐞𝐥𝐢𝐞𝐯𝐞:
❌ Compliance = Security
❌ Certifications = Readiness
❌ Admin access = Productivity
✅ A real Security Architect knows better.
𝐒𝐭𝐫𝐨𝐧𝐠 𝐚𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐚𝐭𝐢𝐨𝐧 𝐦𝐞𝐚𝐧𝐬:
✔ Least Privilege everywhere
✔ No single person controls an entire process
✔ Service accounts treated as first-class risks
✔ PAM with Just-in-Time access, not permanent power
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐟𝐮𝐥𝐥 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/isc2-issap-domain-4-4-3-architect-identity-authorization
#CyberSecurity #ISSAP #IAM #ZeroTrust #SecurityLeadership #PrivilegedAccessManagement #InfosecTrain
0 Kommentare
0 Anteile
1866 Ansichten
0 Vorschau