How DHCP Works ?
Ever wondered how your devices instantly connect to the internet without you manually setting up IP addresses?
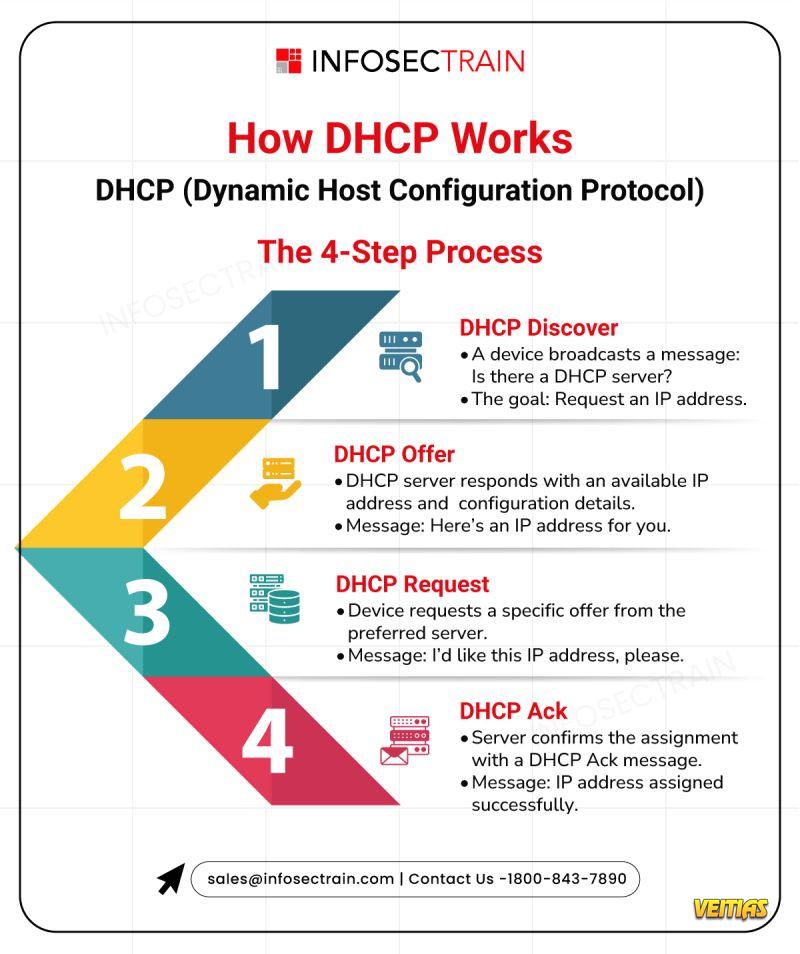
It's a seamless DHCP 4-step process that happens behind the scenes every time you connect. Our infographic breaks it down:
1⃣ Discover: "Hey, is there a DHCP server around?"
2⃣ Offer: "Yep! Here's an IP address for you."
3⃣ Request: "Awesome, I'll take that one, please!"
4⃣ ACK: "Confirmed! IP address assigned successfully."
Check out our visual guide to see exactly How DHCP Works!
Don't miss out on vital insights! Read our latest posts: https://www.infosectrain.com/blog/
#DHCP #Networking #IPAddress #TechExplained #ITBasics #NetworkProtocols #Cybersecurity #InfosecTrain #HowItWorks
Ever wondered how your devices instantly connect to the internet without you manually setting up IP addresses?
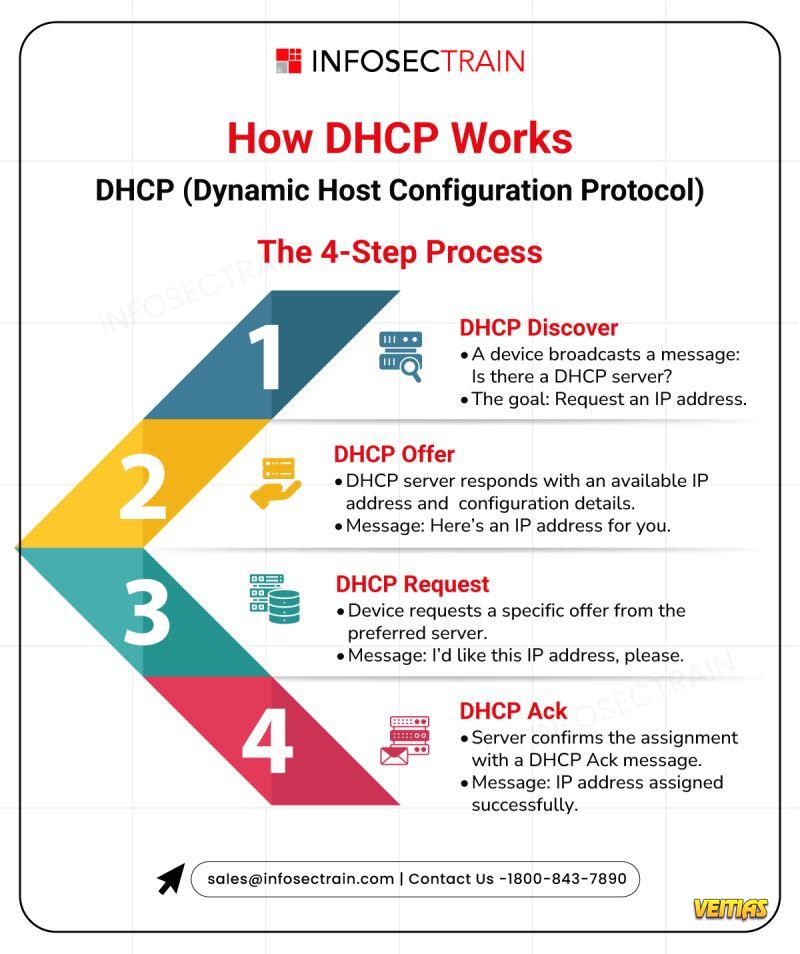
It's a seamless DHCP 4-step process that happens behind the scenes every time you connect. Our infographic breaks it down:
1⃣ Discover: "Hey, is there a DHCP server around?"
2⃣ Offer: "Yep! Here's an IP address for you."
3⃣ Request: "Awesome, I'll take that one, please!"
4⃣ ACK: "Confirmed! IP address assigned successfully."
Check out our visual guide to see exactly How DHCP Works!
Don't miss out on vital insights! Read our latest posts: https://www.infosectrain.com/blog/
#DHCP #Networking #IPAddress #TechExplained #ITBasics #NetworkProtocols #Cybersecurity #InfosecTrain #HowItWorks
How DHCP Works ?
Ever wondered how your devices instantly connect to the internet without you manually setting up IP addresses?
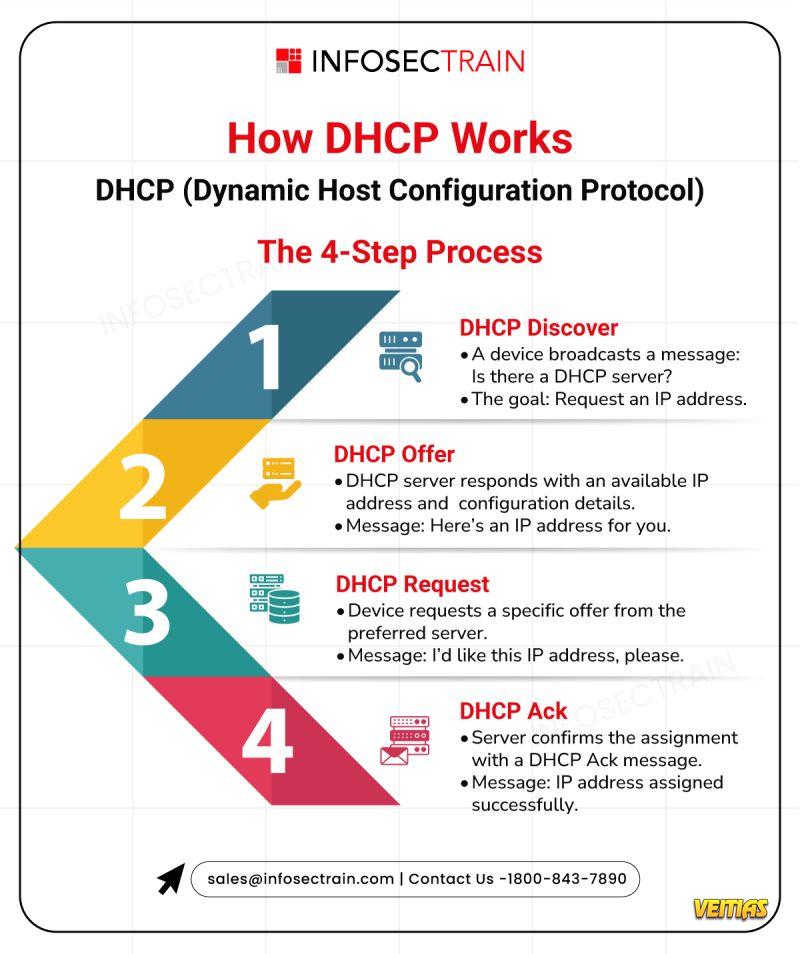
It's a seamless DHCP 4-step process that happens behind the scenes every time you connect. Our infographic breaks it down:
1⃣ Discover: "Hey, is there a DHCP server around?"
2⃣ Offer: "Yep! Here's an IP address for you."
3⃣ Request: "Awesome, I'll take that one, please!"
4⃣ ACK: "Confirmed! IP address assigned successfully."
Check out our visual guide to see exactly How DHCP Works!
Don't miss out on vital insights! Read our latest posts: https://www.infosectrain.com/blog/
#DHCP #Networking #IPAddress #TechExplained #ITBasics #NetworkProtocols #Cybersecurity #InfosecTrain #HowItWorks
0 Kommentare
0 Anteile
4389 Ansichten
0 Vorschau