Supply Chain Security & Automation in 2025
As global supply chains become increasingly interconnected, cyber attackers are exploiting the weakest links — often through unsecured or unmonitored vendors.
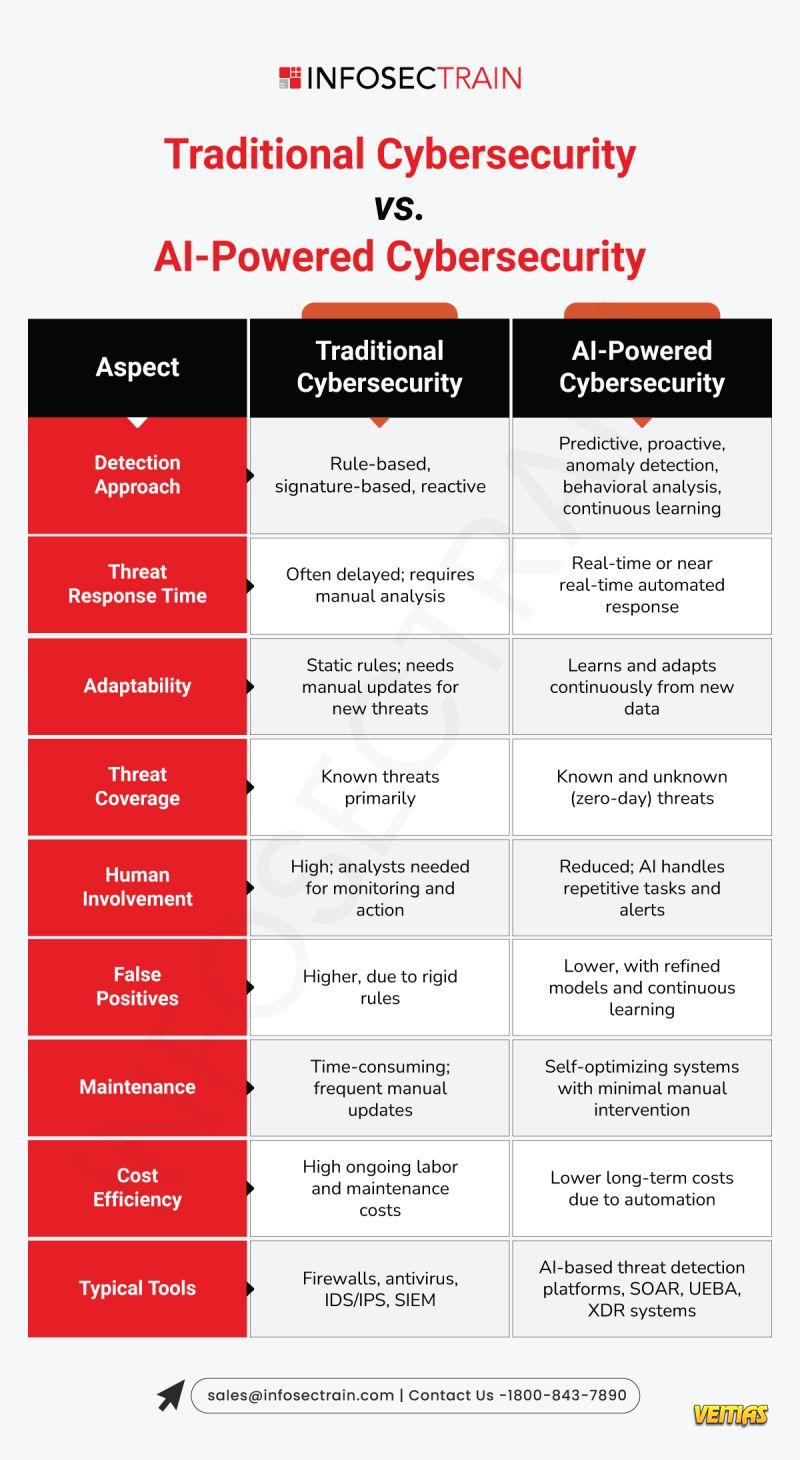
Automation and AI are no longer optional — they’re essential to managing complex, evolving risks across supplier networks.
Key Insights:
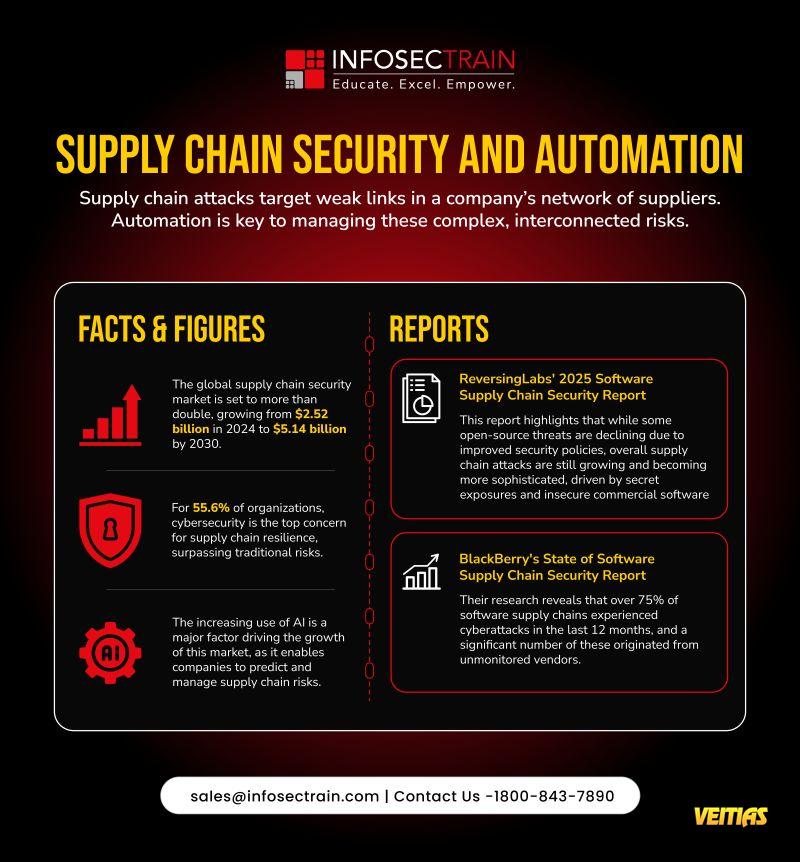
• The supply chain security market is projected to grow from $2.52B (2024) to $5.14B (2030).
• 55.6% of organizations now rank cybersecurity as their top concern for supply chain resilience.
• AI adoption is transforming risk prediction and response.
Recent Reports:
Reversing Labs 2025 Report: Supply chain attacks are growing more sophisticated despite improved open-source security.
BlackBerry Report: Over 75% of software supply chains faced cyberattacks in the past year — many from unmonitored vendors.
This #CybersecurityAwarenessMonth2025, remember — a chain is only as strong as its most secure link.
Check out: https://www.infosectrain.com/events/
#CyberSecurity #SupplyChainSecurity #Automation #AI #InfoSecTrain #DataProtection #ThreatIntelligence #RiskManagement #CyberDefense
As global supply chains become increasingly interconnected, cyber attackers are exploiting the weakest links — often through unsecured or unmonitored vendors.
Automation and AI are no longer optional — they’re essential to managing complex, evolving risks across supplier networks.
Key Insights:
• The supply chain security market is projected to grow from $2.52B (2024) to $5.14B (2030).
• 55.6% of organizations now rank cybersecurity as their top concern for supply chain resilience.
• AI adoption is transforming risk prediction and response.
Recent Reports:
Reversing Labs 2025 Report: Supply chain attacks are growing more sophisticated despite improved open-source security.
BlackBerry Report: Over 75% of software supply chains faced cyberattacks in the past year — many from unmonitored vendors.
This #CybersecurityAwarenessMonth2025, remember — a chain is only as strong as its most secure link.
Check out: https://www.infosectrain.com/events/
#CyberSecurity #SupplyChainSecurity #Automation #AI #InfoSecTrain #DataProtection #ThreatIntelligence #RiskManagement #CyberDefense
🔒 Supply Chain Security & Automation in 2025
As global supply chains become increasingly interconnected, cyber attackers are exploiting the weakest links — often through unsecured or unmonitored vendors.
💡 Automation and AI are no longer optional — they’re essential to managing complex, evolving risks across supplier networks.
📊 Key Insights:
• The supply chain security market is projected to grow from $2.52B (2024) to $5.14B (2030).
• 55.6% of organizations now rank cybersecurity as their top concern for supply chain resilience.
• AI adoption is transforming risk prediction and response.
📘 Recent Reports:
Reversing Labs 2025 Report: Supply chain attacks are growing more sophisticated despite improved open-source security.
BlackBerry Report: Over 75% of software supply chains faced cyberattacks in the past year — many from unmonitored vendors.
🔗 This #CybersecurityAwarenessMonth2025, remember — a chain is only as strong as its most secure link.
Check out: https://www.infosectrain.com/events/
#CyberSecurity #SupplyChainSecurity #Automation #AI #InfoSecTrain #DataProtection #ThreatIntelligence #RiskManagement #CyberDefense
0 التعليقات
0 المشاركات
2882 مشاهدة
0 معاينة