Recent Updates
All Countries
All Countries
Saint Kitts and Nevis
Palau
Pakistan
Oman
Norway
Northern Mariana Islands
Norfolk Island
Niue
Nigeria
Niger
Nicaragua
New Zealand
New Caledonia
Netherlands Antilles
Palestine
Panama
Rwanda
Russian Federation
Romania
Reunion
Qatar
Puerto Rico
Portugal
Poland
Pitcairn
Philippines
Peru
Paraguay
Papua New Guinea
Netherlands
Nepal
Nauru
Marshall Islands
Malta
Mali
Maldives
Malaysia
Malawi
Madagascar
Macedonia
Macau
Luxembourg
Lithuania
Liechtenstein
Libyan Arab Jamahiriya
Martinique
Mauritania
Namibia
Myanmar
Mozambique
Morocco
Montserrat
Montenegro
Mongolia
Monaco
Moldova, Republic of
Micronesia, Federated States of
Mexico
Mayotte
Mauritius
Liberia
Zimbabwe
United Kingdom
United Arab Emirates
Ukraine
Uganda
Tuvalu
Turks and Caicos Islands
Turkmenistan
Turkey
Tunisia
Trinidad and Tobago
Tonga
Tokelau
Togo
United States
United States minor outlying islands
Zambia
Zaire
Yemen
Western Sahara
Wallis and Futuna Islands
Virgin Islands (U.S.)
Virgin Islands (British)
Vietnam
Venezuela
Vatican City State
Vanuatu
Uzbekistan
Uruguay
Thailand
Tanzania, United Republic of
Tajikistan
Solomon Islands
Slovenia
Slovakia
Singapore
Sierra Leone
Seychelles
Serbia
Senegal
Saudi Arabia
Sao Tome and Principe
San Marino
Samoa
Saint Vincent and the Grenadines
Somalia
South Africa
Taiwan
Syrian Arab Republic
Switzerland
Sweden
Swaziland
Svalbard and Jan Mayen Islands
Suriname
Sudan
St. Pierre and Miquelon
St. Helena
Sri Lanka
Spain
South Georgia South Sandwich Islands
Saint Lucia
Lesotho
Ecuador
Christmas Island
China
Chile
Chad
Central African Republic
Cayman Islands
Cape Verde
Canada
Cameroon
Cambodia
Burundi
Burkina Faso
Bulgaria
Cocos (Keeling) Islands
Colombia
East Timor
Dominican Republic
Dominica
Djibouti
Denmark
Czech Republic
Cyprus
Cuba
Croatia (Hrvatska)
Costa Rica
Cook Islands
Congo
Comoros
Brunei Darussalam
British Indian Ocean Territory
Brazil
Austria
Australia
Aruba
Armenia
Argentina
Antigua and Barbuda
Antarctica
Anguilla
Angola
Andorra
American Samoa
Algeria
Albania
Azerbaijan
Bahamas
Bouvet Island
Botswana
Bosnia and Herzegovina
Bolivia
Bhutan
Bermuda
Benin
Belize
Belgium
Belarus
Barbados
Bangladesh
Bahrain
Afghanistan
Lebanon
Italy
Israel
Ireland
Iraq
Iran (Islamic Republic of)
Indonesia
Isle of Man
India
Iceland
Hungary
Hong Kong
Honduras
Heard and Mc Donald Islands
Ivory Coast
Jersey
Latvia
Lao People's Democratic Republic
Kyrgyzstan
Kuwait
Kosovo
Korea, Republic of
Korea, Democratic People's Republic of
Kiribati
Kenya
Kazakhstan
Jordan
Japan
Jamaica
Haiti
Guyana
Guinea-Bissau
French Polynesia
French Guiana
France, Metropolitan
France
Finland
Fiji
Faroe Islands
Falkland Islands (Malvinas)
Ethiopia
Estonia
Eritrea
Equatorial Guinea
El Salvador
French Southern Territories
Gabon
Guinea
Guatemala
Guam
Guadeloupe
Grenada
Greenland
Greece
Guernsey
Gibraltar
Ghana
Germany
Georgia
Gambia
Egypt
- 𝐙𝐞𝐫𝐨 𝐓𝐫𝐮𝐬𝐭 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 — “𝐍𝐞𝐯𝐞𝐫 𝐓𝐫𝐮𝐬𝐭, 𝐀𝐥𝐰𝐚𝐲𝐬 𝐕𝐞𝐫𝐢𝐟𝐲.”
Perimeter defenses are no longer enough. Zero Trust protects every layer — 𝐮𝐬𝐞𝐫𝐬, 𝐝𝐞𝐯𝐢𝐜𝐞𝐬, 𝐝𝐚𝐭𝐚, 𝐚𝐧𝐝 𝐚𝐩𝐩𝐬 — through continuous verification and least privilege access.
𝐄𝐧𝐝𝐩𝐨𝐢𝐧𝐭𝐬: Patch, monitor, defend with EDR & MDM
𝐍𝐞𝐭𝐰𝐨𝐫𝐤: Micro-segment & encrypt traffic
𝐃𝐚𝐭𝐚: Encrypt, back up, and apply DLP
𝐂𝐥𝐨𝐮𝐝: Control access with IAM & CASB
𝐀𝐩𝐩𝐬 & 𝐀𝐏𝐈𝐬: Secure code, test, and validate every call
Assume breach. Verify everything. Trust nothing.
#ZeroTrust #CyberSecurity #InfoSec #NetworkSecurity #LeastPrivilege #IdentitySecurity #SecurityArchitecture #ZeroTrustModel #CyberDefense #DataProtection #InfosecTrain🔐 𝐙𝐞𝐫𝐨 𝐓𝐫𝐮𝐬𝐭 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 — “𝐍𝐞𝐯𝐞𝐫 𝐓𝐫𝐮𝐬𝐭, 𝐀𝐥𝐰𝐚𝐲𝐬 𝐕𝐞𝐫𝐢𝐟𝐲.” Perimeter defenses are no longer enough. Zero Trust protects every layer — 𝐮𝐬𝐞𝐫𝐬, 𝐝𝐞𝐯𝐢𝐜𝐞𝐬, 𝐝𝐚𝐭𝐚, 𝐚𝐧𝐝 𝐚𝐩𝐩𝐬 — through continuous verification and least privilege access. 💻 𝐄𝐧𝐝𝐩𝐨𝐢𝐧𝐭𝐬: Patch, monitor, defend with EDR & MDM 🌐 𝐍𝐞𝐭𝐰𝐨𝐫𝐤: Micro-segment & encrypt traffic 🧩 𝐃𝐚𝐭𝐚: Encrypt, back up, and apply DLP ☁️ 𝐂𝐥𝐨𝐮𝐝: Control access with IAM & CASB 🧱 𝐀𝐩𝐩𝐬 & 𝐀𝐏𝐈𝐬: Secure code, test, and validate every call Assume breach. Verify everything. Trust nothing. #ZeroTrust #CyberSecurity #InfoSec #NetworkSecurity #LeastPrivilege #IdentitySecurity #SecurityArchitecture #ZeroTrustModel #CyberDefense #DataProtection #InfosecTrain0 Comments 0 Shares 171 Views 0 ReviewsPlease log in to like, share and comment! - 𝐎𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐑𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐜𝐞 𝐯𝐬. 𝐁𝐮𝐬𝐢𝐧𝐞𝐬𝐬 𝐂𝐨𝐧𝐭𝐢𝐧𝐮𝐢𝐭𝐲
Why they're not the same, and why your organization needs a mix of both to get through today's disruptions. vs. Business Continuity
𝐖𝐡𝐲 𝐓𝐡𝐞𝐲’𝐫𝐞 𝐍𝐨𝐭 𝐈𝐧𝐭𝐞𝐫𝐜𝐡𝐚𝐧𝐠𝐞𝐚𝐛𝐥𝐞
Daily Operational Resilience is running operations.
Business Continuity brings them back.
Today’s organizations need both layers, to survive and to scale.
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/operational-resilience-vs-business-continuity/
Become proficient in each approach with 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧’𝐬 𝐆𝐑𝐂 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 Programs. Build, audit, and deploy new age of resilience + continuity frameworks in operational environments.
#OperationalResilience #BusinessContinuity #CyberSecurity #GRC #RiskManagement #ResilienceStrategy #ContinuityPlanning#Compliance #InfosecTrain #Leadership #BusinessResilience𝐎𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐚𝐥 𝐑𝐞𝐬𝐢𝐥𝐢𝐞𝐧𝐜𝐞 𝐯𝐬. 𝐁𝐮𝐬𝐢𝐧𝐞𝐬𝐬 𝐂𝐨𝐧𝐭𝐢𝐧𝐮𝐢𝐭𝐲 Why they're not the same, and why your organization needs a mix of both to get through today's disruptions. vs. Business Continuity ✅ 𝐖𝐡𝐲 𝐓𝐡𝐞𝐲’𝐫𝐞 𝐍𝐨𝐭 𝐈𝐧𝐭𝐞𝐫𝐜𝐡𝐚𝐧𝐠𝐞𝐚𝐛𝐥𝐞 🔹 Daily Operational Resilience is running operations. 🔹Business Continuity brings them back. 🔹 Today’s organizations need both layers, to survive and to scale. 👉 𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/operational-resilience-vs-business-continuity/ Become proficient in each approach with 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧’𝐬 𝐆𝐑𝐂 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 Programs. Build, audit, and deploy new age of resilience + continuity frameworks in operational environments. #OperationalResilience #BusinessContinuity #CyberSecurity #GRC #RiskManagement #ResilienceStrategy #ContinuityPlanning#Compliance #InfosecTrain #Leadership #BusinessResilienceWWW.INFOSECTRAIN.COMOperational Resilience vs. Business ContinuityIt often comes down to the difference between operational resilience and business continuity. Many assume these terms mean the same thing, but they don’t.0 Comments 0 Shares 208 Views 0 Reviews - Think Your Internal Network Is Safe? Think Again. LLMNR Might Be Your Silent Weak Spot!
Most teams overlook it… but LLMNR (Link-Local Multicast Name Resolution) is one of the easiest ways attackers steal credentials inside internal networks.
In this video, we break down:
What LLMNR is & why it exists
How attackers abuse it for credential harvesting
Real-world techniques like MitM + spoofing
How SOC teams and defenders can detect & prevent LLMNR attacks
Watch Here: https://youtu.be/tw0Q_oIt0kg?si=Np1tX65Q7gL2daEG
#LLMNR #NetworkSecurity #InfosecTrain #EthicalHacking #ResponderTool #ManInTheMiddleAttack #CredentialHarvesting #CyberSecurityTraining #RedTeam #BlueTeamThink Your Internal Network Is Safe? Think Again. LLMNR Might Be Your Silent Weak Spot! Most teams overlook it… but LLMNR (Link-Local Multicast Name Resolution) is one of the easiest ways attackers steal credentials inside internal networks. In this video, we break down: 🔹 What LLMNR is & why it exists 🔹 How attackers abuse it for credential harvesting 🔹 Real-world techniques like MitM + spoofing 🔹 How SOC teams and defenders can detect & prevent LLMNR attacks Watch Here: https://youtu.be/tw0Q_oIt0kg?si=Np1tX65Q7gL2daEG #LLMNR #NetworkSecurity #InfosecTrain #EthicalHacking #ResponderTool #ManInTheMiddleAttack #CredentialHarvesting #CyberSecurityTraining #RedTeam #BlueTeam 0 Comments 0 Shares 501 Views 0 Reviews
0 Comments 0 Shares 501 Views 0 Reviews - Splunk Clustering and Indexing
Why It Matters for Security Teams?
– Detect threats faster
– Ensure uninterrupted investigations
– Improve visibility across distributed environments
– Handle massive log volumes with ease
Read Here: https://infosec-train.blogspot.com/2025/11/splunk-clustering-and-indexing.html
#Splunk #SIEM #CyberSecurity #ThreatDetection #SOC #SplunkTraining #Indexing #Clustering #SecurityAnalytics #BigData #InfoSec #InfosecTrain #TechSkills #DataEngineeringSplunk Clustering and Indexing 💡 Why It Matters for Security Teams? – Detect threats faster – Ensure uninterrupted investigations – Improve visibility across distributed environments – Handle massive log volumes with ease Read Here: https://infosec-train.blogspot.com/2025/11/splunk-clustering-and-indexing.html #Splunk #SIEM #CyberSecurity #ThreatDetection #SOC #SplunkTraining #Indexing #Clustering #SecurityAnalytics #BigData #InfoSec #InfosecTrain #TechSkills #DataEngineeringINFOSEC-TRAIN.BLOGSPOT.COMSplunk Clustering and IndexingLet’s be real—data is the backbone of your business. But with cyber threats, hardware failures, and unexpected disasters lurking around ever...0 Comments 0 Shares 418 Views 0 Reviews - Cybersecurity & Data Protection in the Age of AI
Perfect for: CISOs tired of checkbox compliance | Legal teams drowning in AI jargon | Tech leaders balancing innovation with risk | Anyone who knows "we'll figure it out later" isn't a strategy
Watch Here: https://youtu.be/JKv6vHDn4Js?si=CGWnbwUClNE-uIj8
#CybersecurityAwarenessMonth #CyberTalks #InfosecTrain #AIRegulation #DataProtection #CyberSecurity #AICompliance #InfoSec #TechTalks #AIEthics #ZeroTrust #CISO #DataPrivacy #cyberthreatsCybersecurity & Data Protection in the Age of AI Perfect for: CISOs tired of checkbox compliance | Legal teams drowning in AI jargon | Tech leaders balancing innovation with risk | Anyone who knows "we'll figure it out later" isn't a strategy Watch Here: https://youtu.be/JKv6vHDn4Js?si=CGWnbwUClNE-uIj8 #CybersecurityAwarenessMonth #CyberTalks #InfosecTrain #AIRegulation #DataProtection #CyberSecurity #AICompliance #InfoSec #TechTalks #AIEthics #ZeroTrust #CISO #DataPrivacy #cyberthreats 0 Comments 0 Shares 2017 Views 0 Reviews
0 Comments 0 Shares 2017 Views 0 Reviews - 𝐁𝐢𝐠 𝐂𝐡𝐚𝐧𝐠𝐞𝐬 𝐀𝐫𝐞 𝐂𝐨𝐦𝐢𝐧𝐠 𝐭𝐨 𝐭𝐡𝐞 𝐂𝐈𝐏𝐏/𝐄 𝐄𝐱𝐚𝐦 𝐄𝐟𝐟𝐞𝐜𝐭𝐢𝐯𝐞 𝐒𝐞𝐩𝐭 𝟏, 𝟐𝟎𝟐𝟓!
If you want to take the 𝐂𝐈𝐏𝐏/𝐄, here’s your heads up: the new exam edition is now more focused on real-world privacy issues than ever before.
Here's all you need to know as a privacy pro:
𝟑 𝐃𝐨𝐦𝐚𝐢𝐧𝐬 → 𝟓 𝐃𝐨𝐦𝐚𝐢𝐧𝐬
The test now reflects the real-life processes of privacy teams:
✔ Rights & Principles
✔ Legal Grounds for Processing
✔ Responsibilities of the Controller & Processor
✔ Cross-Border Transfers
✔ Incorporation of GDPR in your organization
This change reflects the way organizations are increasingly working with privacy today.
Read more here: https://www.infosectrain.com/blog/whats-new-in-cipp-e-in-2025/
Concerned about the new domains?
Infosec Train 𝐂𝐈𝐏𝐏/𝐄 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 Now with Updates for 2025 covers 2025 updates, new regulations, practical scenarios & exam strategies to keep you ahead of the curve.
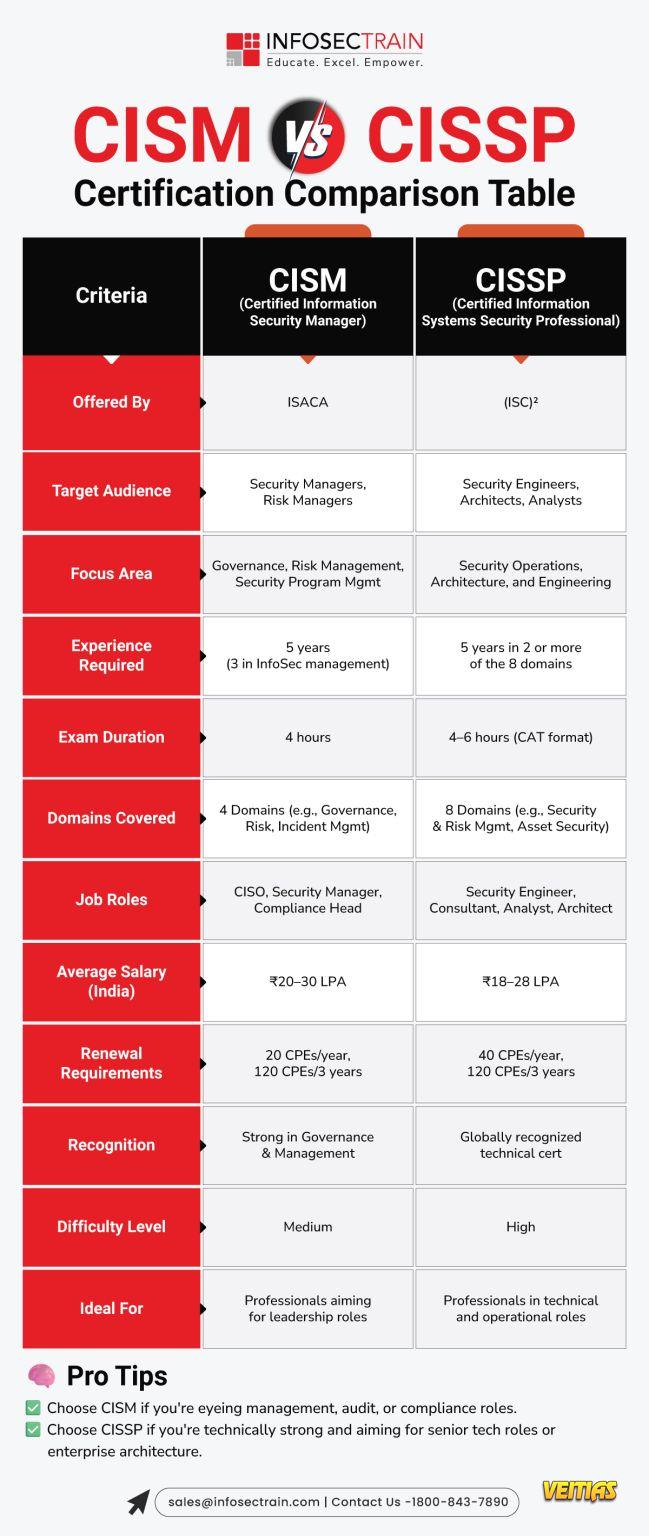
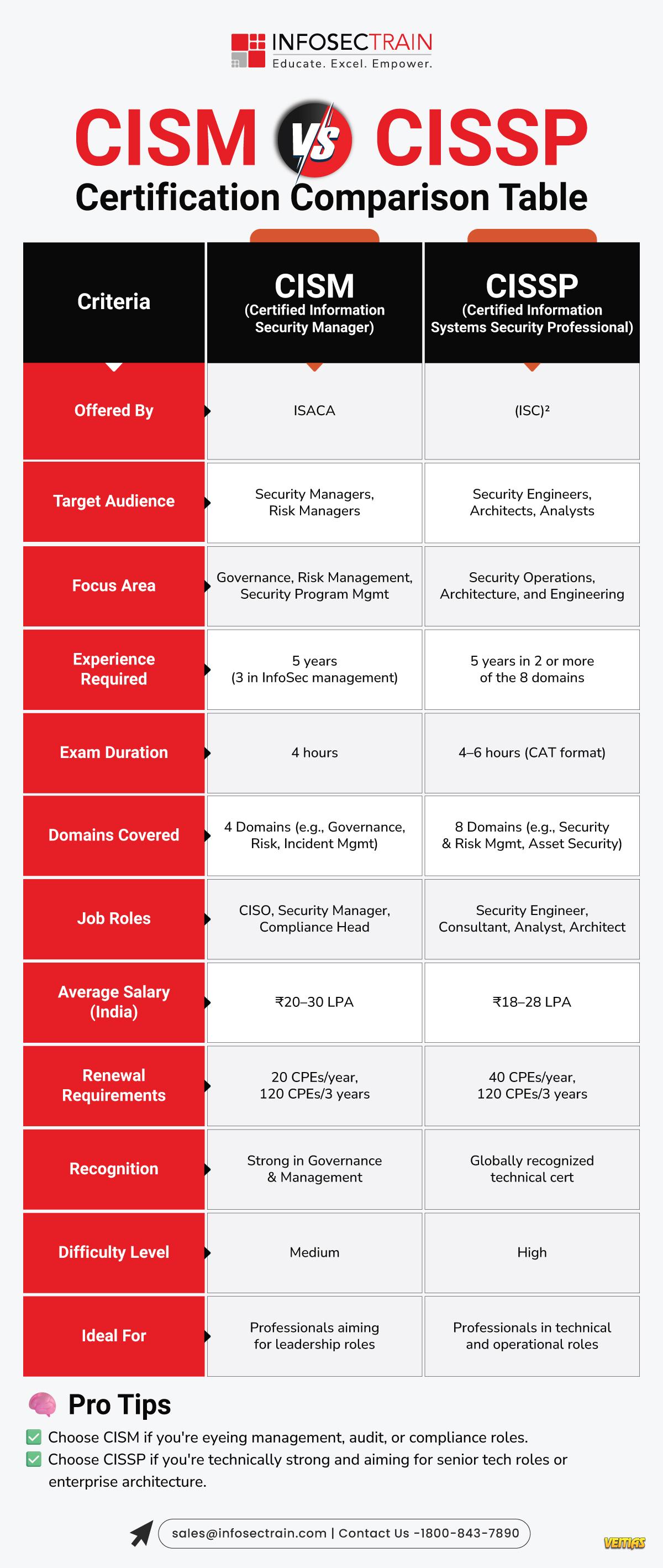
#CIPPE #IAPP #PrivacyLaw #GDPRCompliance #AIAct #EUDataAct #DataProtection #Cybersecurity #PrivacyProfessionals #InfosecTrain #CertificationPrep #EDPB #PrivacyUpdates #ExamPrep𝐁𝐢𝐠 𝐂𝐡𝐚𝐧𝐠𝐞𝐬 𝐀𝐫𝐞 𝐂𝐨𝐦𝐢𝐧𝐠 𝐭𝐨 𝐭𝐡𝐞 𝐂𝐈𝐏𝐏/𝐄 𝐄𝐱𝐚𝐦 👉 𝐄𝐟𝐟𝐞𝐜𝐭𝐢𝐯𝐞 𝐒𝐞𝐩𝐭 𝟏, 𝟐𝟎𝟐𝟓! If you want to take the 𝐂𝐈𝐏𝐏/𝐄, here’s your heads up: the new exam edition is now more focused on real-world privacy issues than ever before. Here's all you need to know as a privacy pro: ➡️ 𝟑 𝐃𝐨𝐦𝐚𝐢𝐧𝐬 → 𝟓 𝐃𝐨𝐦𝐚𝐢𝐧𝐬 ✅ The test now reflects the real-life processes of privacy teams: ✔ Rights & Principles ✔ Legal Grounds for Processing ✔ Responsibilities of the Controller & Processor ✔ Cross-Border Transfers ✔ Incorporation of GDPR in your organization ➡️This change reflects the way organizations are increasingly working with privacy today. 👉 Read more here: https://www.infosectrain.com/blog/whats-new-in-cipp-e-in-2025/ 🎓 Concerned about the new domains? ✅ Infosec Train 𝐂𝐈𝐏𝐏/𝐄 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 Now with Updates for 2025 covers 2025 updates, new regulations, practical scenarios & exam strategies to keep you ahead of the curve. #CIPPE #IAPP #PrivacyLaw #GDPRCompliance #AIAct #EUDataAct #DataProtection #Cybersecurity #PrivacyProfessionals #InfosecTrain #CertificationPrep #EDPB #PrivacyUpdates #ExamPrepWWW.INFOSECTRAIN.COMWhat's new in CIPP/E in 2025?This wave of regulation signals that privacy professionals must navigate not only traditional data-protection law but also an emerging intersection with AI governance and digital ethics.0 Comments 0 Shares 2081 Views 0 Reviews - CISM vs CISSP is a common comparison for cybersecurity professionals choosing between management-focused and technical-focused career paths. CISM is designed for those who want to lead security programs, manage risk, and build enterprise-level strategies. CISSP, on the other hand, is broader and more technical, covering security engineering, architecture, operations, and more. A comparison table helps you clearly understand differences in exam structure, domains, job roles, difficulty level, and salary potential, so you can pick the certification that aligns best with your career goals.CISM vs CISSP is a common comparison for cybersecurity professionals choosing between management-focused and technical-focused career paths. CISM is designed for those who want to lead security programs, manage risk, and build enterprise-level strategies. CISSP, on the other hand, is broader and more technical, covering security engineering, architecture, operations, and more. A comparison table helps you clearly understand differences in exam structure, domains, job roles, difficulty level, and salary potential, so you can pick the certification that aligns best with your career goals.0 Comments 0 Shares 1524 Views 0 Reviews
- CISM vs CISSP: Certification Comparison Table
This guide highlights differences in focus areas, exam structure, domains, experience requirements, and ideal job roles. Whether you aim to excel in security management (CISM) or master a broad spectrum of security practices (CISSP), this infographic simplifies decision-making. InfosecTrain’s expert-led training programs prepare learners with real-world insights, hands-on practice, and exam-ready resources to boost success. Explore the infographic to choose your perfect cybersecurity path with confidence.
Full Guide For CISM vs CISSP - https://www.infosectrain.com/blog/cism-vs-cissp-where-to-start/
#CISM #CISSP #CyberSecurityCertifications #InfoSec #CyberSecurity #InformationSecurity #ISACA #ISC2 #CyberSecurity Training #ITSecurity #CyberSecurityCareers #CyberSecurityProfessionals #Data Protection #Risk Management #Security Management #Governance #Compliance #CyberAwareness #CyberEducation #InfosecTrain #Upskilling #CyberLearning #TechTraining #learntoriseCISM vs CISSP: Certification Comparison Table This guide highlights differences in focus areas, exam structure, domains, experience requirements, and ideal job roles. Whether you aim to excel in security management (CISM) or master a broad spectrum of security practices (CISSP), this infographic simplifies decision-making. InfosecTrain’s expert-led training programs prepare learners with real-world insights, hands-on practice, and exam-ready resources to boost success. Explore the infographic to choose your perfect cybersecurity path with confidence. Full Guide For CISM vs CISSP - https://www.infosectrain.com/blog/cism-vs-cissp-where-to-start/ #CISM #CISSP #CyberSecurityCertifications #InfoSec #CyberSecurity #InformationSecurity #ISACA #ISC2 #CyberSecurity Training #ITSecurity #CyberSecurityCareers #CyberSecurityProfessionals #Data Protection #Risk Management #Security Management #Governance #Compliance #CyberAwareness #CyberEducation #InfosecTrain #Upskilling #CyberLearning #TechTraining #learntorise0 Comments 0 Shares 2421 Views 0 Reviews - Get hands-on, real-world audit experience in just 2 power-packed days!
Introducing the Hands-On IT Audit Bootcamp: Practical Skills to Lead & Scale
29–30 November 2025 | 7 PM – 11 PM (IST)
🖥 Live Online Training
Register Now: https://www.infosectrain.com/pages/lp/it-audit-masterclass/
Expert Instructor: Aarti
CISA | CSX | CIA (Part 1) | Cloud Compliance Specialist
17+ Years of Experience | Risk & Audit Leader
Why This Bootcamp Matters
IT auditors today aren’t just expected to “check controls”—they’re expected to strategize, lead, and drive audit maturity.
This bootcamp gives you the skills audit leaders use every day:
Real scenarios. Real testing. Real documentation. Real communication.
Bootcamp Agenda Snapshot
Day 1: Build the Foundation
✔ IT Audit fundamentals & frameworks
✔ Risk assessment (case study)
✔ ITGC audit planning (hands-on)
✔ IAM control testing (group activity)
Day 2: Scale Your Audit Game
✔ Audit evidence & documentation (exercise)
✔ Issue management & communication (simulation)
✔ TPRM testing (ISO 27001, NIST 2.0, FCA/PRA)
✔ Knowledge assessment + final takeaways
You’ll Walk Away With:
Real-world audit practice
ITGC, IAM & TPRM mastery
Leadership-ready audit skills
8 CPE Credits
Career Recognition Certificate
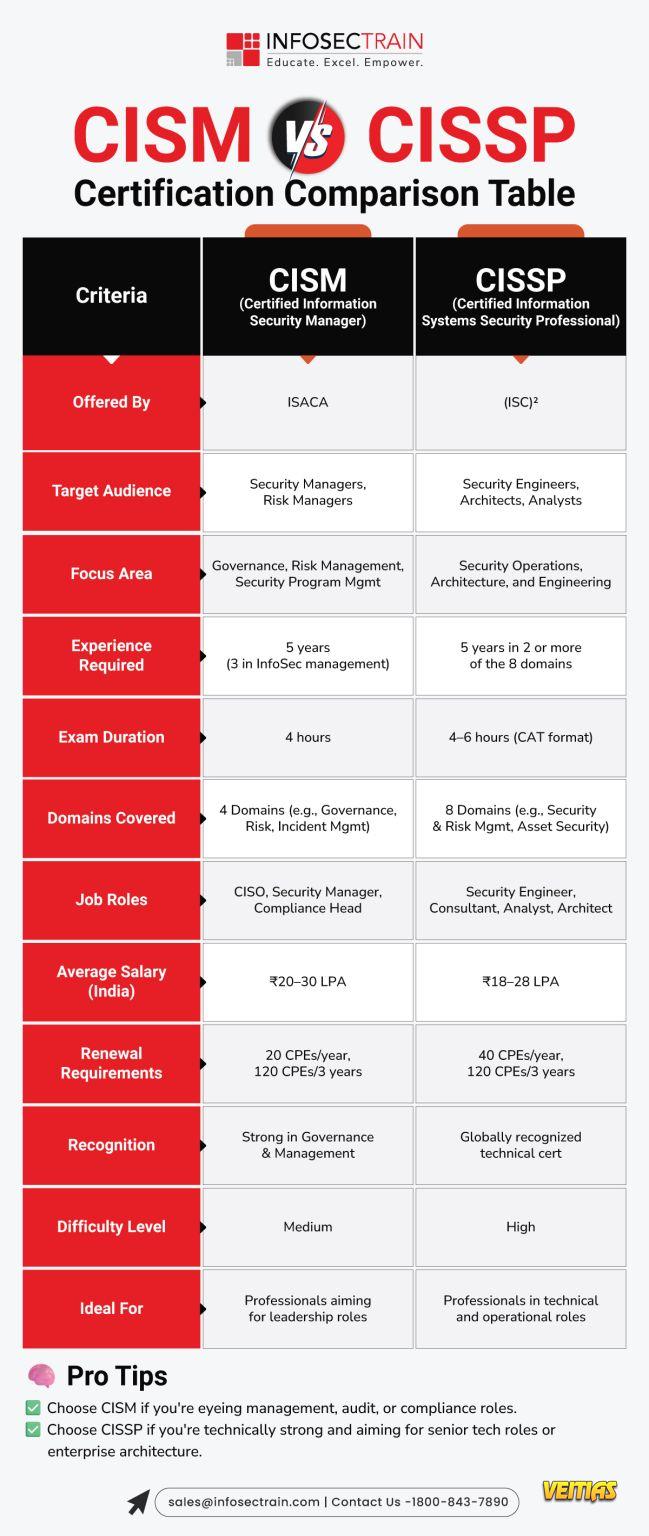
#ITAudit #AuditBootcamp #InfosecTrain #ITGCAudit #RiskManagement #TPRM #ComplianceTraining #ISORisk #CyberSecurityTraining #AuditLeadership #GovernanceRiskCompliance #ITAuditSkills #CISA #AuditorLife #ProfessionalDevelopmentGet hands-on, real-world audit experience in just 2 power-packed days! Introducing the Hands-On IT Audit Bootcamp: Practical Skills to Lead & Scale 📅 29–30 November 2025 | ⏰ 7 PM – 11 PM (IST) 🖥 Live Online Training 🔗 Register Now: https://www.infosectrain.com/pages/lp/it-audit-masterclass/ 👩🏫 Expert Instructor: Aarti CISA | CSX | CIA (Part 1) | Cloud Compliance Specialist 17+ Years of Experience | Risk & Audit Leader 🌟 Why This Bootcamp Matters IT auditors today aren’t just expected to “check controls”—they’re expected to strategize, lead, and drive audit maturity. This bootcamp gives you the skills audit leaders use every day: Real scenarios. Real testing. Real documentation. Real communication. 📘 Bootcamp Agenda Snapshot Day 1: Build the Foundation ✔ IT Audit fundamentals & frameworks ✔ Risk assessment (case study) ✔ ITGC audit planning (hands-on) ✔ IAM control testing (group activity) Day 2: Scale Your Audit Game ✔ Audit evidence & documentation (exercise) ✔ Issue management & communication (simulation) ✔ TPRM testing (ISO 27001, NIST 2.0, FCA/PRA) ✔ Knowledge assessment + final takeaways 🏆 You’ll Walk Away With: ✨ Real-world audit practice ✨ ITGC, IAM & TPRM mastery ✨ Leadership-ready audit skills ✨ 8 CPE Credits ✨ Career Recognition Certificate #ITAudit #AuditBootcamp #InfosecTrain #ITGCAudit #RiskManagement #TPRM #ComplianceTraining #ISORisk #CyberSecurityTraining #AuditLeadership #GovernanceRiskCompliance #ITAuditSkills #CISA #AuditorLife #ProfessionalDevelopment0 Comments 0 Shares 2361 Views 0 Reviews - CISM vs CISSP: Which Cybersecurity Certification Should You Choose?
Choosing between CISM and CISSP can feel like decoding a security puzzle — both are powerful, both are respected, and both open doors to high-impact cybersecurity roles.
To make it easier, here’s a clear comparison table breaking down what truly matters:
✔ Focus Areas
✔ Target Audience
✔ Exam Structure
✔ Job Roles
✔ Who Should Choose What
visit InfosecTrain to explore training options.
#CISM #CISSP #CyberSecurityCareers #InfoSecTrain #CybersecurityTraining #ITSecurity #CyberRisk #SecurityLeadership #ISACA #ISC2 #CareerGrowth #SecurityCertifications🔐 CISM vs CISSP: Which Cybersecurity Certification Should You Choose? Choosing between CISM and CISSP can feel like decoding a security puzzle — both are powerful, both are respected, and both open doors to high-impact cybersecurity roles. To make it easier, here’s a clear comparison table breaking down what truly matters: ✔ Focus Areas ✔ Target Audience ✔ Exam Structure ✔ Job Roles ✔ Who Should Choose What 👉visit InfosecTrain to explore training options. #CISM #CISSP #CyberSecurityCareers #InfoSecTrain #CybersecurityTraining #ITSecurity #CyberRisk #SecurityLeadership #ISACA #ISC2 #CareerGrowth #SecurityCertifications0 Comments 0 Shares 1918 Views 0 Reviews
More Stories
Trending
Security Cameras