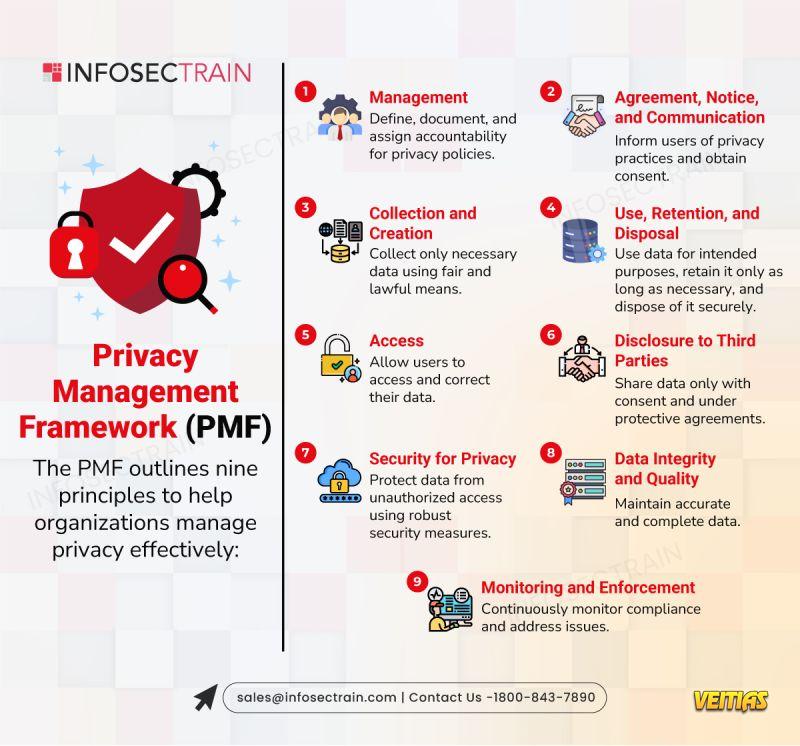
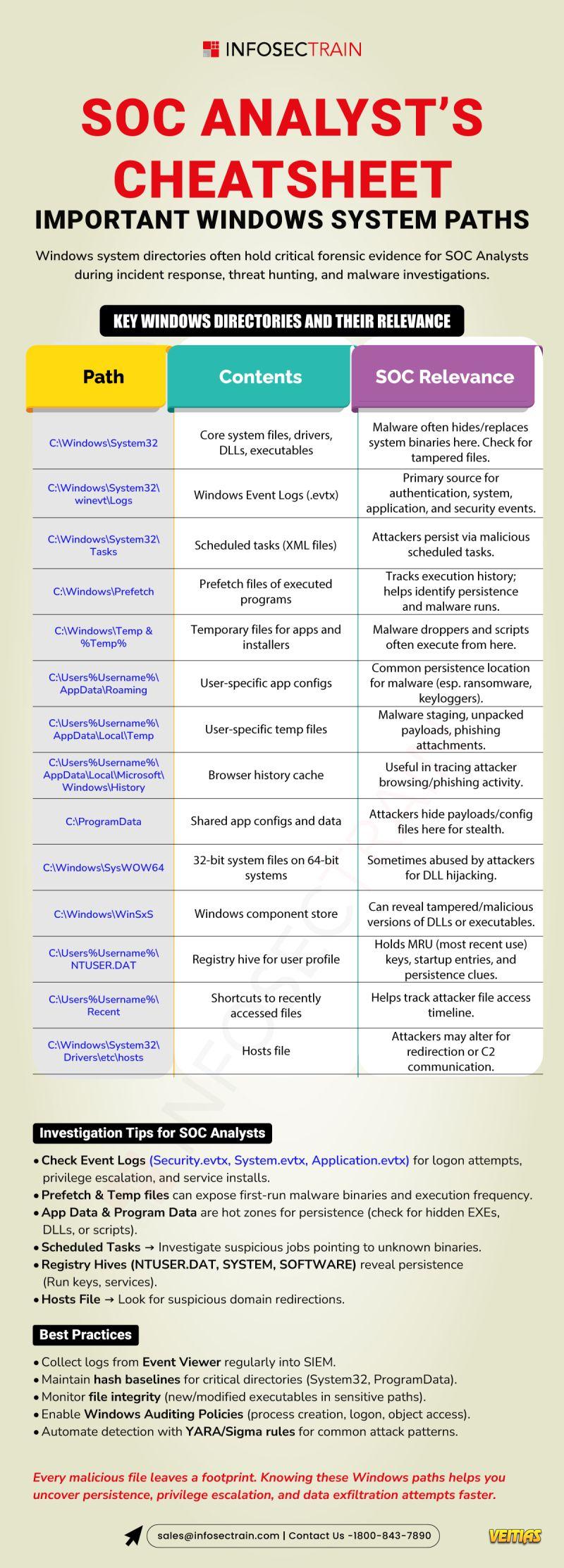
ChatGPT 5.1 FREE Masterclass: Mastering GPT-5.1 to 10X Your Productivity!
AI isn’t the future anymore — it’s the present, and those who learn how to leverage it will lead tomorrow.
Join us for a power-packed masterclass designed to help you transform ChatGPT 5.1 into your ultimate productivity partner!
Date: 10 Dec 2025 (Wed)
Time: 8 – 9 PM (IST)
Speaker: Anas Hamid
Free Register Now: https://www.infosectrain.com/events/chatgpt-masterclass-from-first-prompt-to-ai-power-user/
What You’ll Learn
The Basics: What is ChatGPT? Who should use it?
Under the Hood: GPT-4o’s multimodal intelligence – text, voice & vision
Prompting Mastery using the C.R.E.A.T.E. framework
Slash Commands & Hidden Productivity Hacks
Build Custom GPTs for automation & personalization
Workflow Superpowers: Plugins + Advanced Data Analysis
Manage data usage & privacy confidently
Gain skills in creative writing, coding basics & AI-powered project execution
Why Attend?
✔ Get a CPE Certificate
✔ Free Career Guidance & Mentorship
✔ Learn directly from AI experts
✔ Enhance efficiency & stay ahead in the AI-driven workforce
#ChatGPT5_1 #GenerativeAI #AIProductivity #AITraining #ChatGPTMasterclass #ArtificialIntelligence #FutureSkills #ProductivityHacks #TechInnovation #InfosecTrain #CareerGrowth
AI isn’t the future anymore — it’s the present, and those who learn how to leverage it will lead tomorrow.
Join us for a power-packed masterclass designed to help you transform ChatGPT 5.1 into your ultimate productivity partner!
Date: 10 Dec 2025 (Wed)
Time: 8 – 9 PM (IST)
Speaker: Anas Hamid
Free Register Now: https://www.infosectrain.com/events/chatgpt-masterclass-from-first-prompt-to-ai-power-user/
What You’ll Learn
The Basics: What is ChatGPT? Who should use it?
Under the Hood: GPT-4o’s multimodal intelligence – text, voice & vision
Prompting Mastery using the C.R.E.A.T.E. framework
Slash Commands & Hidden Productivity Hacks
Build Custom GPTs for automation & personalization
Workflow Superpowers: Plugins + Advanced Data Analysis
Manage data usage & privacy confidently
Gain skills in creative writing, coding basics & AI-powered project execution
Why Attend?
✔ Get a CPE Certificate
✔ Free Career Guidance & Mentorship
✔ Learn directly from AI experts
✔ Enhance efficiency & stay ahead in the AI-driven workforce
#ChatGPT5_1 #GenerativeAI #AIProductivity #AITraining #ChatGPTMasterclass #ArtificialIntelligence #FutureSkills #ProductivityHacks #TechInnovation #InfosecTrain #CareerGrowth
ChatGPT 5.1 FREE Masterclass: Mastering GPT-5.1 to 10X Your Productivity!
AI isn’t the future anymore — it’s the present, and those who learn how to leverage it will lead tomorrow.
Join us for a power-packed masterclass designed to help you transform ChatGPT 5.1 into your ultimate productivity partner!
📅 Date: 10 Dec 2025 (Wed)
⌚ Time: 8 – 9 PM (IST)
🎤 Speaker: Anas Hamid
🔗 Free Register Now: https://www.infosectrain.com/events/chatgpt-masterclass-from-first-prompt-to-ai-power-user/
📘 What You’ll Learn
✨ The Basics: What is ChatGPT? Who should use it?
✨ Under the Hood: GPT-4o’s multimodal intelligence – text, voice & vision
✨ Prompting Mastery using the C.R.E.A.T.E. framework
✨ Slash Commands & Hidden Productivity Hacks
✨ Build Custom GPTs for automation & personalization
✨ Workflow Superpowers: Plugins + Advanced Data Analysis
✨ Manage data usage & privacy confidently
✨ Gain skills in creative writing, coding basics & AI-powered project execution
🎯 Why Attend?
✔ Get a CPE Certificate
✔ Free Career Guidance & Mentorship
✔ Learn directly from AI experts
✔ Enhance efficiency & stay ahead in the AI-driven workforce
#ChatGPT5_1 #GenerativeAI #AIProductivity #AITraining #ChatGPTMasterclass #ArtificialIntelligence #FutureSkills #ProductivityHacks #TechInnovation #InfosecTrain #CareerGrowth
0 Reacties
0 aandelen
1786 Views
0 voorbeeld