InfosecTrain is an online training & certification course provider. Learn Ethical Hacking, Penetration Testing, Application Security, Cloud Security, Network Security, and many more.
- 344 المنشورات
- 149 الصور
- 1 الفيديوهات
- يعيش في Noida, Uttar Pradesh, India
- Male
- 01/01/2000
- متابَع بواسطة 4 أشخاص
التحديثات الأخيرة
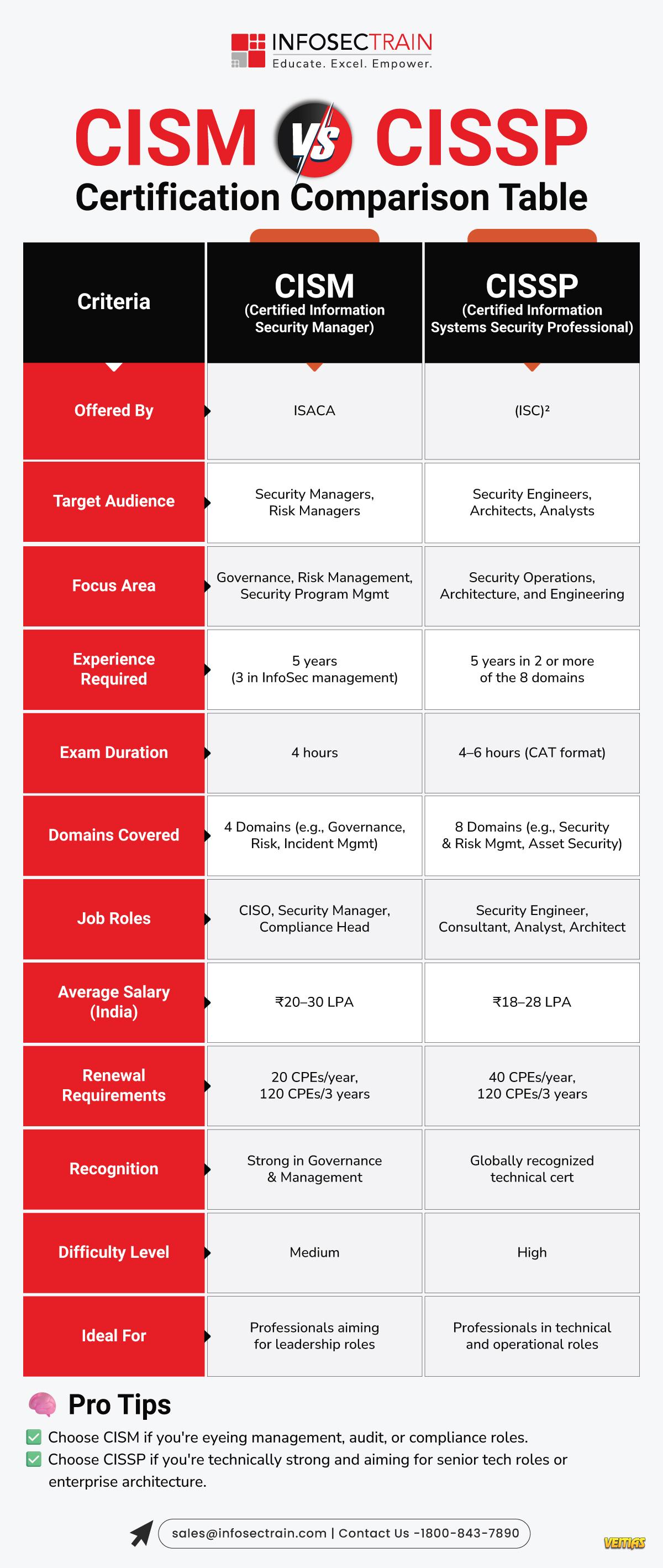
- CISM vs CISSP: Certification Comparison Table
This guide highlights differences in focus areas, exam structure, domains, experience requirements, and ideal job roles. Whether you aim to excel in security management (CISM) or master a broad spectrum of security practices (CISSP), this infographic simplifies decision-making. InfosecTrain’s expert-led training programs prepare learners with real-world insights, hands-on practice, and exam-ready resources to boost success. Explore the infographic to choose your perfect cybersecurity path with confidence.
Full Guide For CISM vs CISSP - https://www.infosectrain.com/blog/cism-vs-cissp-where-to-start/
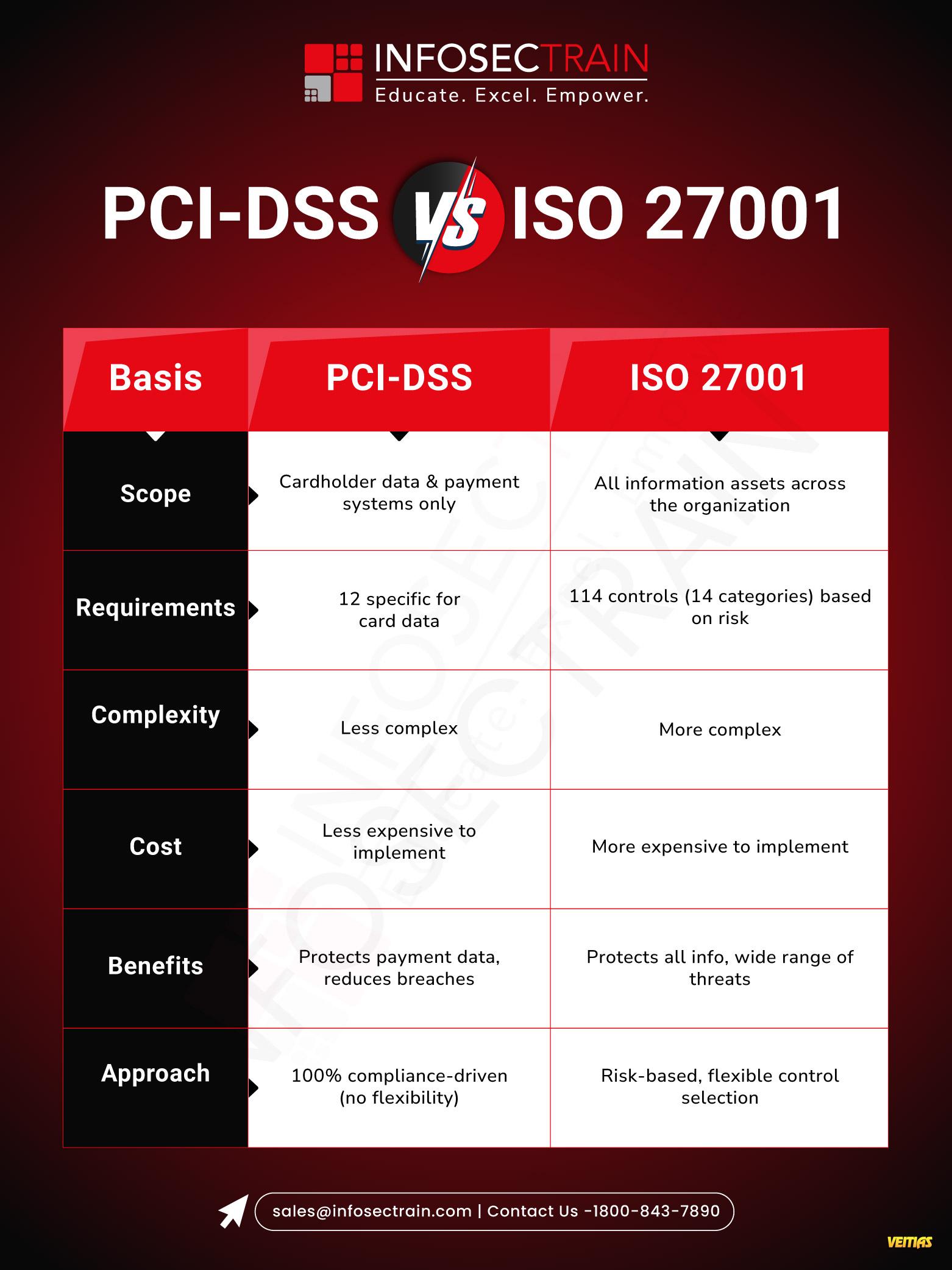
#CISM #CISSP #CyberSecurityCertifications #InfoSec #CyberSecurity #InformationSecurity #ISACA #ISC2 #CyberSecurity Training #ITSecurity #CyberSecurityCareers #CyberSecurityProfessionals #Data Protection #Risk Management #Security Management #Governance #Compliance #CyberAwareness #CyberEducation #InfosecTrain #Upskilling #CyberLearning #TechTraining #learntoriseCISM vs CISSP: Certification Comparison Table This guide highlights differences in focus areas, exam structure, domains, experience requirements, and ideal job roles. Whether you aim to excel in security management (CISM) or master a broad spectrum of security practices (CISSP), this infographic simplifies decision-making. InfosecTrain’s expert-led training programs prepare learners with real-world insights, hands-on practice, and exam-ready resources to boost success. Explore the infographic to choose your perfect cybersecurity path with confidence. Full Guide For CISM vs CISSP - https://www.infosectrain.com/blog/cism-vs-cissp-where-to-start/ #CISM #CISSP #CyberSecurityCertifications #InfoSec #CyberSecurity #InformationSecurity #ISACA #ISC2 #CyberSecurity Training #ITSecurity #CyberSecurityCareers #CyberSecurityProfessionals #Data Protection #Risk Management #Security Management #Governance #Compliance #CyberAwareness #CyberEducation #InfosecTrain #Upskilling #CyberLearning #TechTraining #learntorise0 التعليقات 0 المشاركات 3024 مشاهدة 0 معاينةالرجاء تسجيل الدخول , للأعجاب والمشاركة والتعليق على هذا! - InfosecTrain’s latest infographic explores PCI-DSS vs. ISO 27001, highlighting the key differences between these two critical security standards. Understand how PCI-DSS focuses on safeguarding payment card data, while ISO 27001 provides a broader framework for managing overall information security across organizations.
More Info Visit - https://www.infosectrain.com/
#PCIDSSvsISO27001 #InformationSecurityStandards #CyberCompliance #DataProtectionStandards #SecurityFrameworkComparison #infosectrain #SecurityShowdown #BattleOfStandards #PCIDSSvsISO27001 #learntoriseInfosecTrain’s latest infographic explores PCI-DSS vs. ISO 27001, highlighting the key differences between these two critical security standards. Understand how PCI-DSS focuses on safeguarding payment card data, while ISO 27001 provides a broader framework for managing overall information security across organizations. More Info Visit - https://www.infosectrain.com/ #PCIDSSvsISO27001 #InformationSecurityStandards #CyberCompliance #DataProtectionStandards #SecurityFrameworkComparison #infosectrain #SecurityShowdown #BattleOfStandards #PCIDSSvsISO27001 #learntorise0 التعليقات 0 المشاركات 2840 مشاهدة 0 معاينة - The AI Arms Race in Cybersecurity is Real - and It's Defining 2025.
As we mark Cybersecurity Awareness Month 2025, it's clear: Al is transforming both attack and defense.
From automated ransomware to ML-powered detection, the future of cyber resilience depends on how we use Al - responsibly and strategically.
Learn More With AI-Powered Cybersecurity Training Course Online - https://www.infosectrain.com/courses/artificial-intelligence-ai-for-cyber-security-professionals-training/
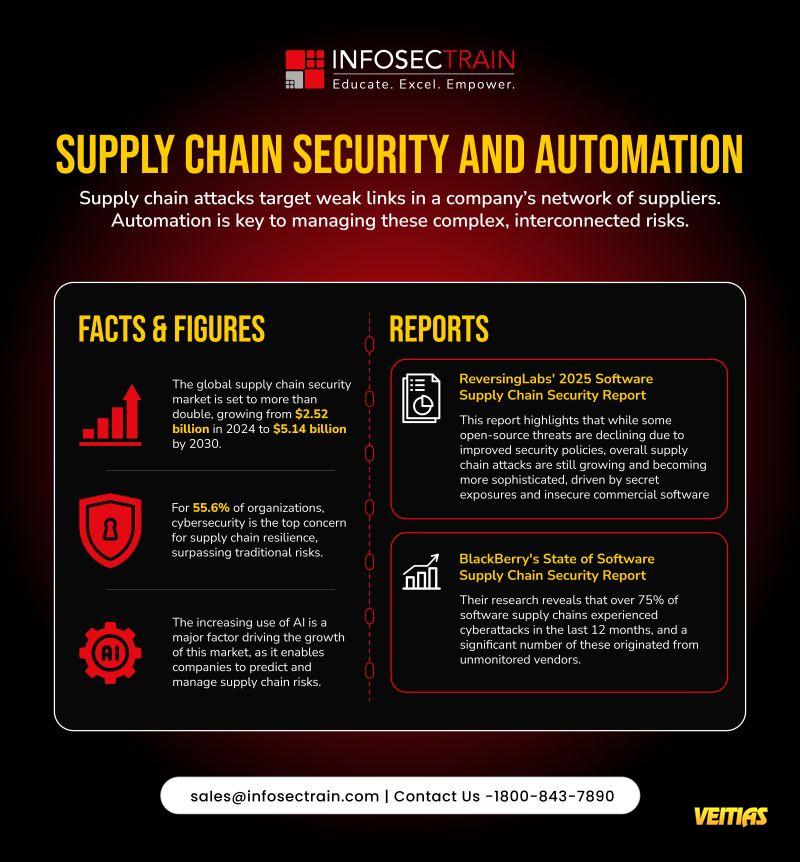
#CyberSecurityAwarenessMonth #CyberSecurity #AI #MachineLearning #DataProtection #AlTech #Infosec #infosectrain #learntoriseThe AI Arms Race in Cybersecurity is Real - and It's Defining 2025. As we mark Cybersecurity Awareness Month 2025, it's clear: Al is transforming both attack and defense. From automated ransomware to ML-powered detection, the future of cyber resilience depends on how we use Al - responsibly and strategically. Learn More With AI-Powered Cybersecurity Training Course Online - https://www.infosectrain.com/courses/artificial-intelligence-ai-for-cyber-security-professionals-training/ #CyberSecurityAwarenessMonth #CyberSecurity #AI #MachineLearning #DataProtection #AlTech #Infosec #infosectrain #learntorise0 التعليقات 0 المشاركات 3275 مشاهدة 0 معاينة - Supply Chain Security & Automation in 2025
As global supply chains grow more interconnected, cyber threats are targeting the weakest links, often through unmonitored or unsecured vendors.
Visit Our Site - https://www.infosectrain.com/
Build resilience. Automate defenses. Stay vigilant.
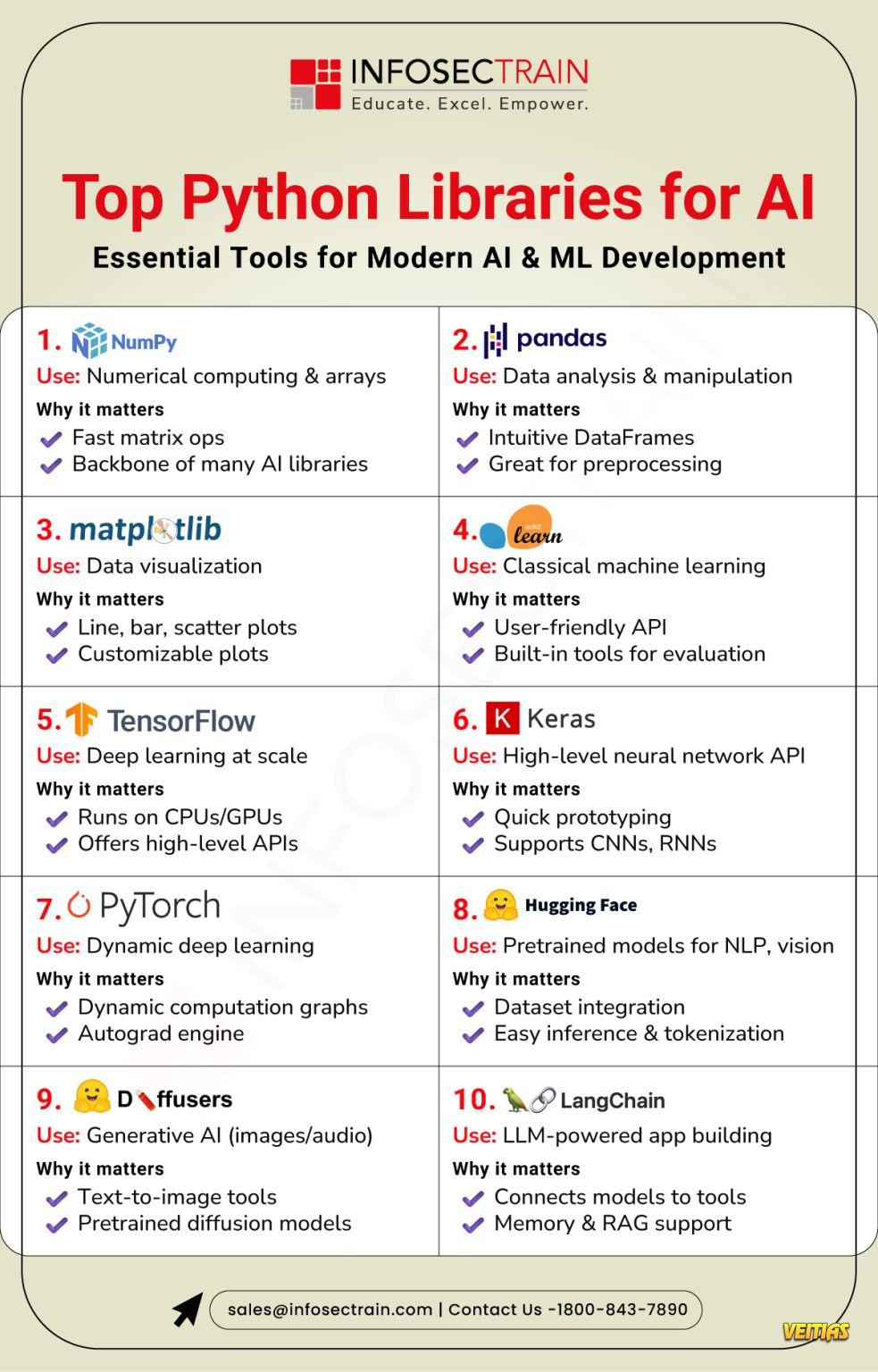
#SupplyChainSecurity #CyberResilience #Automation #AlinSecurity #ThreatIntelligence #CyberAwareness #DigitalTrust #VendorRiskManagement #infosectrain #learntoriseSupply Chain Security & Automation in 2025 As global supply chains grow more interconnected, cyber threats are targeting the weakest links, often through unmonitored or unsecured vendors. Visit Our Site - https://www.infosectrain.com/ Build resilience. Automate defenses. Stay vigilant. #SupplyChainSecurity #CyberResilience #Automation #AlinSecurity #ThreatIntelligence #CyberAwareness #DigitalTrust #VendorRiskManagement #infosectrain #learntorise0 التعليقات 0 المشاركات 3796 مشاهدة 0 معاينة - Top Python Libraries for Al
InfosecTrain’s latest infographic showcases the most powerful Python libraries driving Artificial Intelligence innovations. From machine learning to deep learning and data processing, this visual guide highlights the essential tools that every AI practitioner should know to build smarter, scalable, and more efficient AI solutions.
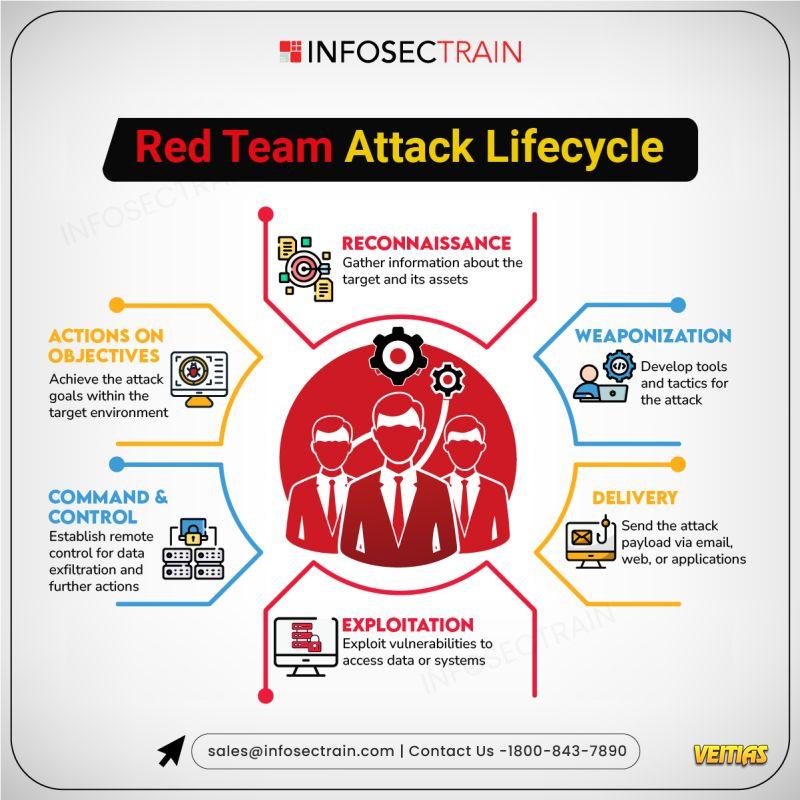
#Python #Al #Artificiallntelligence #MachineLearning #DeepLearning #PythonLibraries #PythonForAI #AIML #DataScience #AlTools #LearnPython #TechTrends #AICommunity #MLDevelopers #CodeWithPython #infosectrain #learntoriseTop Python Libraries for Al InfosecTrain’s latest infographic showcases the most powerful Python libraries driving Artificial Intelligence innovations. From machine learning to deep learning and data processing, this visual guide highlights the essential tools that every AI practitioner should know to build smarter, scalable, and more efficient AI solutions. #Python #Al #Artificiallntelligence #MachineLearning #DeepLearning #PythonLibraries #PythonForAI #AIML #DataScience #AlTools #LearnPython #TechTrends #AICommunity #MLDevelopers #CodeWithPython #infosectrain #learntorise0 التعليقات 0 المشاركات 5406 مشاهدة 0 معاينة - Red Team Attack Lifecycle
InfosecTrain’s latest infographic explores the Red Team Attack Lifecycle, showcasing how adversaries plan, execute, and escalate cyberattacks to test an organization’s defenses. It visually explains each stage of the process, helping security teams strengthen detection, response, and resilience against real-world attack simulations.
Interview Questions for Red Team Expert - https://www.infosectrain.com/blog/interview-questions-for-red-team-expert/
#RedTeam #CyberSecurity #AttackLifecycle #InfoSec #ThreatSimulation #PenTesting #AdversaryEmulation #InfosecTrain #CyberDefense #ITSecurityRed Team Attack Lifecycle InfosecTrain’s latest infographic explores the Red Team Attack Lifecycle, showcasing how adversaries plan, execute, and escalate cyberattacks to test an organization’s defenses. It visually explains each stage of the process, helping security teams strengthen detection, response, and resilience against real-world attack simulations. Interview Questions for Red Team Expert - https://www.infosectrain.com/blog/interview-questions-for-red-team-expert/ #RedTeam #CyberSecurity #AttackLifecycle #InfoSec #ThreatSimulation #PenTesting #AdversaryEmulation #InfosecTrain #CyberDefense #ITSecurity0 التعليقات 0 المشاركات 2849 مشاهدة 0 معاينة - How to Clear the CISA Exam in 2025?
InfosecTrain’s latest infographic provides a strategic roadmap for passing the Certified Information Systems Auditor (CISA) exam in 2025. It covers smart preparation tips, updated domains, study resources, and expert insights to help aspirants boost confidence, manage time, and succeed in one of the top IT audit certifications.
Commonly Asked CISA Exam Questions with Answers: https://www.infosectrain.com/blog/commonly-asked-cisa-exam-questions-with-answers/
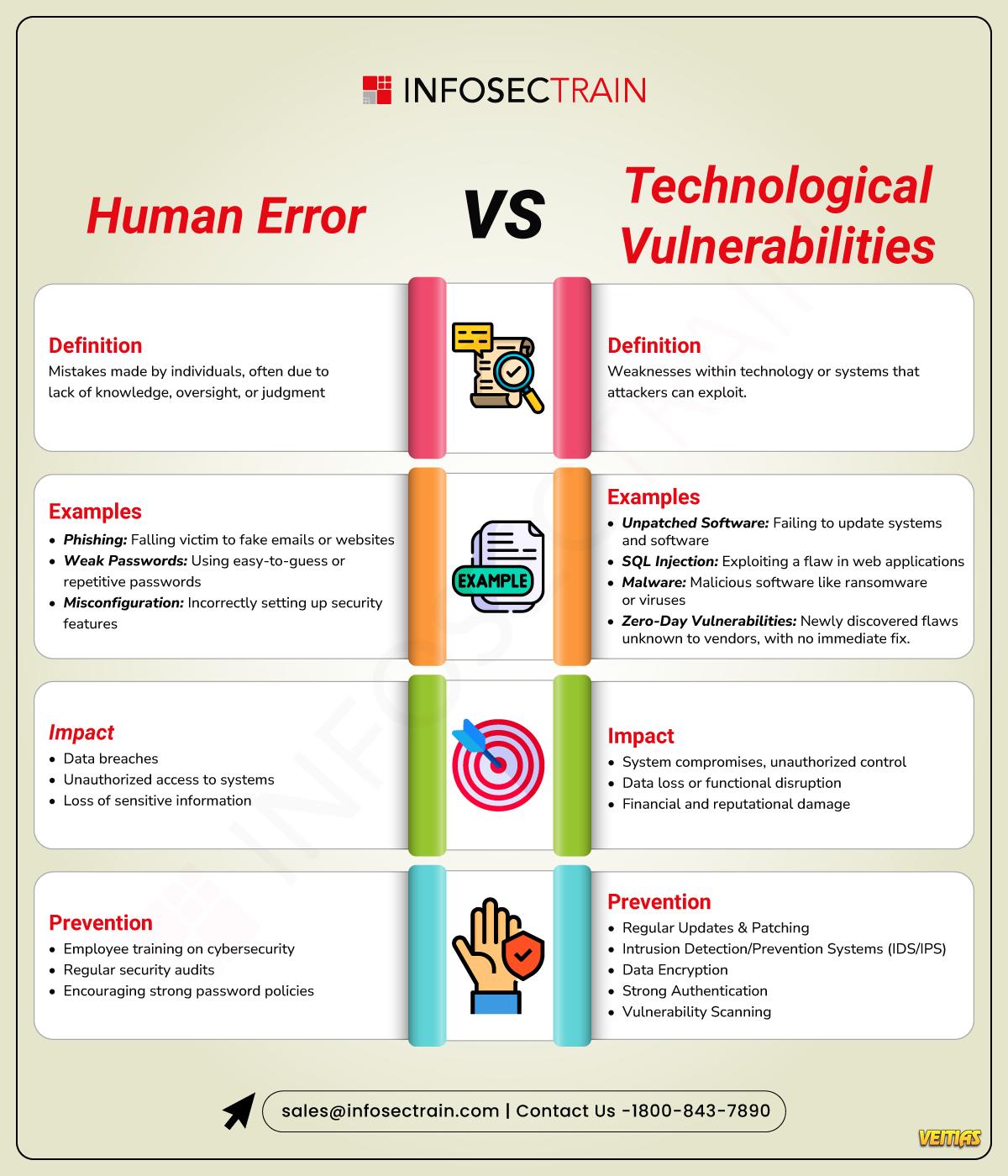
#cisa #CISA2025 #PassTheCISA #ISACAExamTips #infosec #ClearCISA #CISAStudy2025 #CyberCertPrep #infosectrain #learntoriseHow to Clear the CISA Exam in 2025? InfosecTrain’s latest infographic provides a strategic roadmap for passing the Certified Information Systems Auditor (CISA) exam in 2025. It covers smart preparation tips, updated domains, study resources, and expert insights to help aspirants boost confidence, manage time, and succeed in one of the top IT audit certifications. Commonly Asked CISA Exam Questions with Answers: https://www.infosectrain.com/blog/commonly-asked-cisa-exam-questions-with-answers/ #cisa #CISA2025 #PassTheCISA #ISACAExamTips #infosec #ClearCISA #CISAStudy2025 #CyberCertPrep #infosectrain #learntorise0 التعليقات 0 المشاركات 3946 مشاهدة 0 معاينة - Human Error vs Technological Vulnerabilities
InfosecTrain’s latest infographic draws a clear comparison between human error and technological vulnerabilities—two major causes of security breaches. It explains their definitions, real-world examples, impacts, and prevention strategies, helping professionals better understand where risks originate and how to reduce them effectively.
How to Prevent the Most Common Cyber Attacks: https://www.infosectrain.com/blog/how-to-prevent-the-most-common-cyber-attacks/
#CyberSecurity #HumanError #Vulnerabilities #InfoSec #SecurityAwareness #CyberThreats #RiskManagement #DataProtection #SecurityTraining #InfosecTrainHuman Error vs Technological Vulnerabilities InfosecTrain’s latest infographic draws a clear comparison between human error and technological vulnerabilities—two major causes of security breaches. It explains their definitions, real-world examples, impacts, and prevention strategies, helping professionals better understand where risks originate and how to reduce them effectively. How to Prevent the Most Common Cyber Attacks: https://www.infosectrain.com/blog/how-to-prevent-the-most-common-cyber-attacks/ #CyberSecurity #HumanError #Vulnerabilities #InfoSec #SecurityAwareness #CyberThreats #RiskManagement #DataProtection #SecurityTraining #InfosecTrain0 التعليقات 0 المشاركات 3260 مشاهدة 0 معاينة - DevSecOps Toolbox – Key Tools by Category
InfosecTrain’s latest infographic showcases essential tools across categories that power a strong DevSecOps pipeline. It helps teams integrate security seamlessly into development workflows, ensuring faster, safer software delivery while building a culture of shared responsibility for security from code to deployment.
Emerging Trends in DevSecOps Tools in 2025: https://www.infosectrain.com/blog/emerging-trends-in-devsecops-tools/
#DevSecOps #CyberSecurity #AppSec #InfoSec #SecureDevOps #SoftwareSecurity #SecurityTools #CI_CD #DevOpsSecurity #InfosecTrain #Automation #ShiftLeft #CodeSecurity #ITSecurityDevSecOps Toolbox – Key Tools by Category InfosecTrain’s latest infographic showcases essential tools across categories that power a strong DevSecOps pipeline. It helps teams integrate security seamlessly into development workflows, ensuring faster, safer software delivery while building a culture of shared responsibility for security from code to deployment. Emerging Trends in DevSecOps Tools in 2025: https://www.infosectrain.com/blog/emerging-trends-in-devsecops-tools/ #DevSecOps #CyberSecurity #AppSec #InfoSec #SecureDevOps #SoftwareSecurity #SecurityTools #CI_CD #DevOpsSecurity #InfosecTrain #Automation #ShiftLeft #CodeSecurity #ITSecurity0 التعليقات 0 المشاركات 4126 مشاهدة 0 معاينة - Cloud Security Audit Masterclass : For Auditors Who Lead in the Cloud Era
Date: 1st – 3rd July, 2025
Time: 8 PM – 10 PM (IST)
Speaker: Krish
Free Register Now: https://www.infosectrain.com/pages/lp/cloud-audit-masterclass/
Agenda for the Masterclass
DAY 1 - Cloud & AWS Fundamentals for Auditors
• Cloud Fundamentals for Auditors
• AWS Essentials for Auditors
DAY 2 - Cloud Auditing Methodologies & Techniques
• End-to-End Cloud Audit Process & Planning
• Auditing Core Cloud Security Domains
DAY 3 - Auditing AWS Cloud - Practical Scenarios
• Practical AWS Audit Scenarios
• AWS Audit Tools & Next-Gen Auditing
Key Takeaways
• Earn 6 CPE credits in just 6 hours
• Sharpen your Cloud Auditing Skills
• Get expert career guidance on cloud career pathwaysCloud Security Audit Masterclass : For Auditors Who Lead in the Cloud Era Date: 1st – 3rd July, 2025 Time: 8 PM – 10 PM (IST) Speaker: Krish Free Register Now: https://www.infosectrain.com/pages/lp/cloud-audit-masterclass/ Agenda for the Masterclass DAY 1 - Cloud & AWS Fundamentals for Auditors • Cloud Fundamentals for Auditors • AWS Essentials for Auditors DAY 2 - Cloud Auditing Methodologies & Techniques • End-to-End Cloud Audit Process & Planning • Auditing Core Cloud Security Domains DAY 3 - Auditing AWS Cloud - Practical Scenarios • Practical AWS Audit Scenarios • AWS Audit Tools & Next-Gen Auditing Key Takeaways • Earn 6 CPE credits in just 6 hours • Sharpen your Cloud Auditing Skills • Get expert career guidance on cloud career pathways0 التعليقات 0 المشاركات 3393 مشاهدة 0 معاينة
المزيد من المنشورات