𝐊𝐚𝐥𝐢 𝐋𝐢𝐧𝐮𝐱 𝐯𝐬. 𝐏𝐚𝐫𝐫𝐨𝐭 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐎𝐒 – 𝐖𝐡𝐢𝐜𝐡 𝐎𝐒 𝐏𝐨𝐰𝐞𝐫𝐬 𝐘𝐨𝐮𝐫 𝐏𝐞𝐧 𝐓𝐞𝐬𝐭?
Both 𝐊𝐚𝐥𝐢 𝐋𝐢𝐧𝐮𝐱 and 𝐏𝐚𝐫𝐫𝐨𝐭 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐎𝐒 are top-tier tools for ethical hackers and penetration testers. But which one is the best fit for your needs? Let’s compare these two powerful OSs to help you choose!
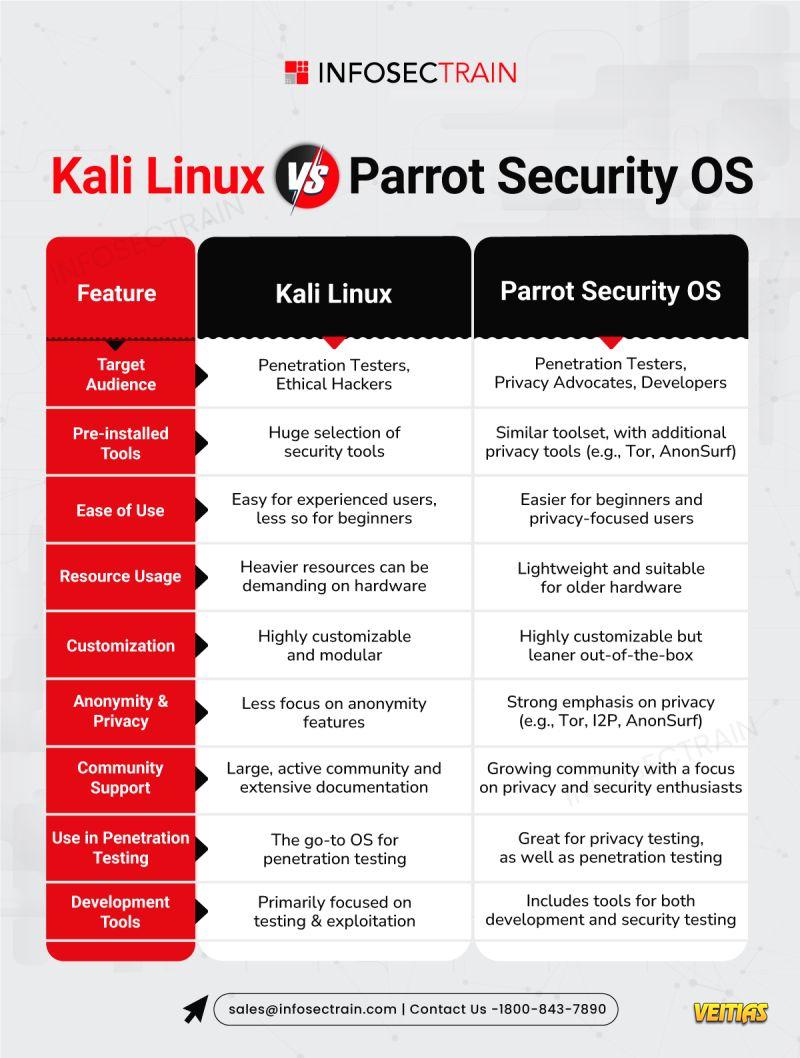
Kali Linux 🖥
Target Audience : Pen Testers, Ethical Hackers.
Pre-installed Tools : Massive toolset dedicated to penetration testing, exploitation, and forensics.
Ease of Use : Great for experienced users, less beginner-friendly.
Resource Usage : Can be demanding on hardware – better for more powerful systems.
Customization : Highly customizable, modular system for various use cases.
Anonymity & Privacy : Less focus on privacy features.
Community Support : Large, well-established community with tons of resources and tutorials.
Use in Penetration Testing : The go-to choice for professional pentesters and red teamers.
Development Tools : Focused primarily on testing, exploiting, and forensics.
Parrot Security OS
Target Audience : Pen Testers, Privacy Advocates, Developers.
Pre-installed Tools : Similar to Kali but with an added emphasis on privacy tools (e.g., Tor, AnonSurf).
Ease of Use : More beginner-friendly with a focus on privacy and security.
Resource Usage : Lightweight, great for older or less powerful hardware.
Customization : Highly customizable but comes leaner out-of-the-box.
Anonymity & Privacy : Strong emphasis on privacy with tools like hashtag#Tor , hashtag#I2P , and hashtag#AnonSurf .
Community Support : A growing, passionate community focusing on security and privacy.
Use in Penetration Testing : Excellent for both pen testing and privacy-related assessments.
Development Tools : Includes both development and security tools, offering a broader scope.
Key Takeaways:
𝐊𝐚𝐥𝐢 𝐋𝐢𝐧𝐮𝐱 is ideal for dedicated pen testers who need a robust toolset and don’t mind a steeper learning curve. It’s the industry standard for penetration testing and ethical hacking .
𝐏𝐚𝐫𝐫𝐨𝐭 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐎𝐒 is perfect for those who want a privacy-focused OS with penetration testing tools and a lighter footprint. Ideal for beginners , developers , and privacy advocates who also need security testing .
Whether you’re testing networks , breaking into systems , or simply prioritizing privacy – these OSs have you covered. Which one is your go-to?
#KaliLinux #ParrotSecurityOS #EthicalHacking #PenetrationTesting #CyberSecurity #LinuxDistros #HackingTools #InfoSec #DigitalSecurity #OpenSourceTools #CyberTools #NetworkSecurity #RedTeam #BlueTeam #CyberDefense #infosectrain🚨 𝐊𝐚𝐥𝐢 𝐋𝐢𝐧𝐮𝐱 𝐯𝐬. 𝐏𝐚𝐫𝐫𝐨𝐭 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐎𝐒 – 𝐖𝐡𝐢𝐜𝐡 𝐎𝐒 𝐏𝐨𝐰𝐞𝐫𝐬 𝐘𝐨𝐮𝐫 𝐏𝐞𝐧 𝐓𝐞𝐬𝐭? 🚨
Both 𝐊𝐚𝐥𝐢 𝐋𝐢𝐧𝐮𝐱 and 𝐏𝐚𝐫𝐫𝐨𝐭 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐎𝐒 are top-tier tools for ethical hackers and penetration testers. But which one is the best fit for your needs? Let’s compare these two powerful OSs to help you choose!
Kali Linux 🖥
➡️ Target Audience : Pen Testers, Ethical Hackers.
➡️ Pre-installed Tools : Massive toolset dedicated to penetration testing, exploitation, and forensics.
➡️ Ease of Use : Great for experienced users, less beginner-friendly.
➡️ Resource Usage : Can be demanding on hardware – better for more powerful systems.
➡️ Customization : Highly customizable, modular system for various use cases.
➡️ Anonymity & Privacy : Less focus on privacy features.
➡️ Community Support : Large, well-established community with tons of resources and tutorials.
➡️ Use in Penetration Testing : The go-to choice for professional pentesters and red teamers.
➡️ Development Tools : Focused primarily on testing, exploiting, and forensics.
Parrot Security OS 🔒
➡️ Target Audience : Pen Testers, Privacy Advocates, Developers.
➡️ Pre-installed Tools : Similar to Kali but with an added emphasis on privacy tools (e.g., Tor, AnonSurf).
➡️ Ease of Use : More beginner-friendly with a focus on privacy and security.
➡️ Resource Usage : Lightweight, great for older or less powerful hardware.
➡️ Customization : Highly customizable but comes leaner out-of-the-box.
➡️ Anonymity & Privacy : Strong emphasis on privacy with tools like hashtag#Tor , hashtag#I2P , and hashtag#AnonSurf .
➡️ Community Support : A growing, passionate community focusing on security and privacy.
➡️ Use in Penetration Testing : Excellent for both pen testing and privacy-related assessments.
➡️ Development Tools : Includes both development and security tools, offering a broader scope.
🔑 Key Takeaways:
𝐊𝐚𝐥𝐢 𝐋𝐢𝐧𝐮𝐱 is ideal for dedicated pen testers who need a robust toolset and don’t mind a steeper learning curve. It’s the industry standard for penetration testing and ethical hacking .
𝐏𝐚𝐫𝐫𝐨𝐭 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐎𝐒 is perfect for those who want a privacy-focused OS with penetration testing tools and a lighter footprint. Ideal for beginners , developers , and privacy advocates who also need security testing .
🔐 Whether you’re testing networks , breaking into systems , or simply prioritizing privacy – these OSs have you covered. Which one is your go-to? 🧐
#KaliLinux #ParrotSecurityOS #EthicalHacking #PenetrationTesting #CyberSecurity #LinuxDistros #HackingTools #InfoSec #DigitalSecurity #OpenSourceTools #CyberTools #NetworkSecurity #RedTeam #BlueTeam #CyberDefense #infosectrain