𝐀𝐫𝐭𝐢𝐟𝐢𝐜𝐢𝐚𝐥 𝐈𝐧𝐭𝐞𝐥𝐥𝐢𝐠𝐞𝐧𝐜𝐞: 𝐈𝐧𝐧𝐨𝐯𝐚𝐭𝐢𝐨𝐧 𝐨𝐫 𝐑𝐢𝐬𝐤?
AI is changing the way we work, make things, and connect with the world surrounding us but with these changes come additional challenges we have to address and be responsible for.
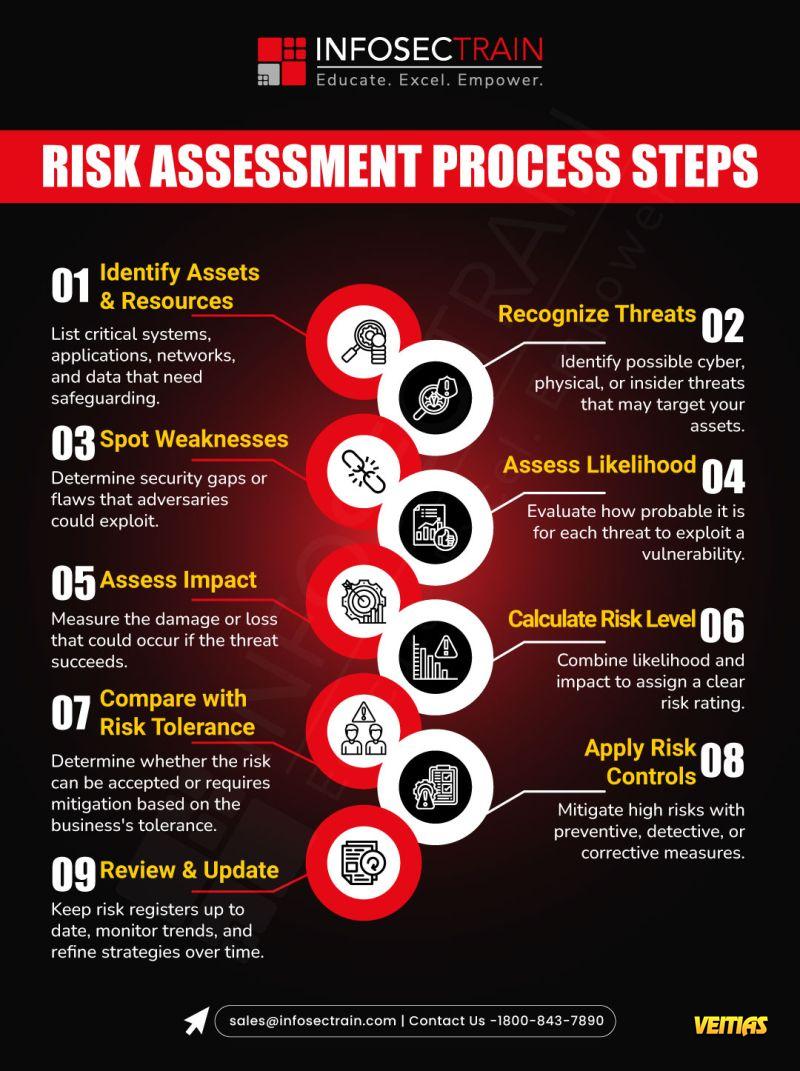
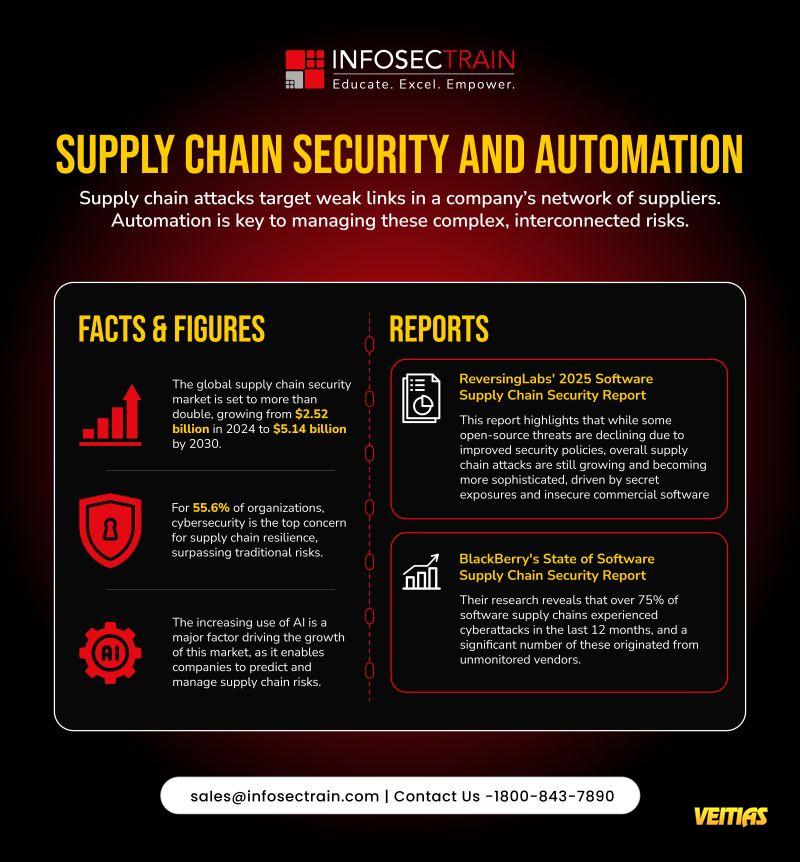
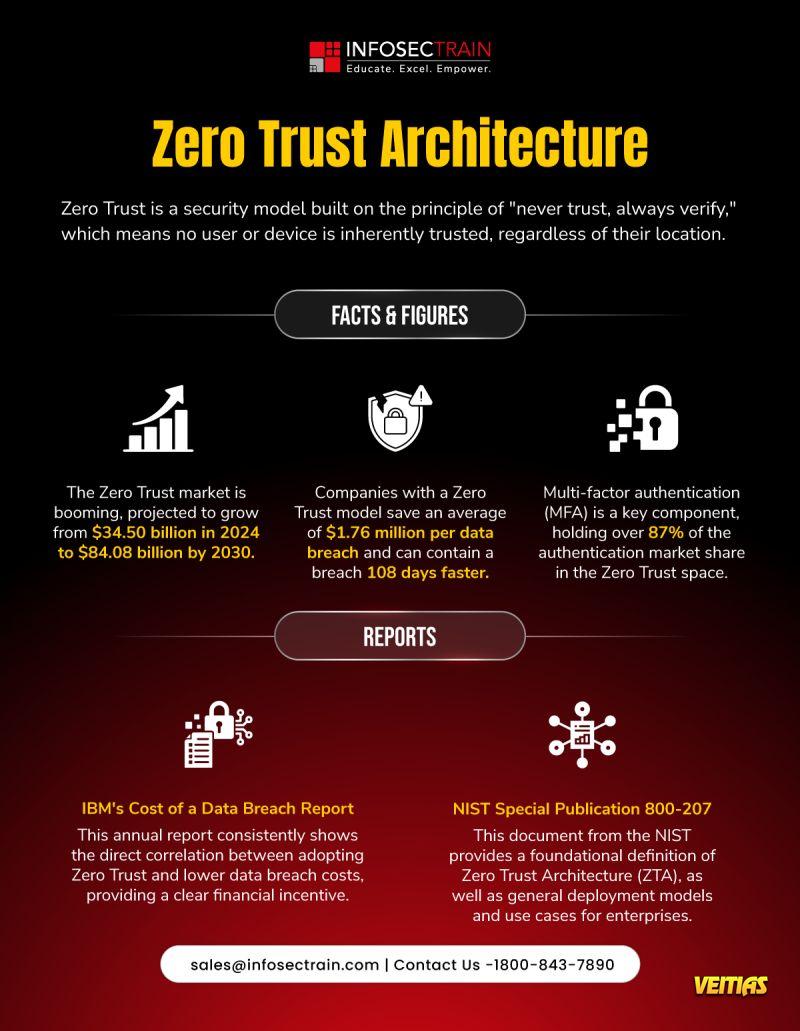
This is what we are up against
Model Bias
Biased results by poorly trained models.
Privacy Breaches
Data from users is gathered and abused without their consent.
Cyber Threats Controlled by AI
Attacks on autopilot that are more intelligent than traditional defenses.
Oppague
“Black box” systems with limited accountability.
Energy Consumption: Significant energy required for AI computation.
Misinformation & Deepfakes
fabricate content that influence our opinions and politics.
Ethical Abuse
The misuse of technology even if it is cutting ethical boundaries.
𝐑𝐞𝐚𝐥-𝐰𝐨𝐫𝐥𝐝 𝐬𝐜𝐞𝐧𝐚𝐫𝐢𝐨𝐬
𝐢𝐧𝐜𝐥𝐮𝐝𝐢𝐧𝐠 𝐀𝐈-𝐩𝐨𝐰𝐞𝐫𝐞𝐝 𝐡𝐢𝐫𝐢𝐧𝐠 𝐝𝐢𝐬𝐜𝐫𝐢𝐦𝐢𝐧𝐚𝐭𝐢𝐨𝐧 𝐭𝐨 𝐝𝐞𝐞𝐩𝐟𝐚𝐤𝐞 𝐩𝐨𝐥𝐢𝐭𝐢𝐜𝐚𝐥 𝐜𝐚𝐦𝐩𝐚𝐢𝐠𝐧𝐬
𝐬𝐞𝐫𝐯𝐞 𝐚𝐬 𝐚 𝐫𝐞𝐦𝐢𝐧𝐝𝐞𝐫 𝐭𝐡𝐚𝐭 𝐡𝐮𝐦𝐚𝐧 𝐨𝐯𝐞𝐫𝐬𝐢𝐠𝐡𝐭 𝐚𝐧𝐝 𝐫𝐞𝐠𝐮𝐥𝐚𝐭𝐢𝐨𝐧 𝐚𝐫𝐞 𝐧𝐨 𝐥𝐨𝐧𝐠𝐞𝐫 𝐨𝐩𝐭𝐢𝐨𝐧𝐚𝐥; 𝐭𝐡𝐞𝐲 𝐚𝐫𝐞 𝐞𝐬𝐬𝐞𝐧𝐭𝐢𝐚𝐥.
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞:
https://www.infosectrain.com/blog/ai-associated-risks-and-how-to-mitigate-them/ Infosec Train AI and Cybersecurity Course empowers individuals to better comprehend the threats, develop ethical AI guidelines, and combat emerging digital threats leading to a safe and responsible AI-empowered future.
#ArtificialIntelligence #CyberSecurity #ResponsibleAI #AIethics #AIrisks #DataPrivacy #Deepfakes #TechResponsibility #EthicalAI #AIawareness #DigitalSafety #RiskManagement #Governance #AItraining #InfoSecTrain
𝐀𝐫𝐭𝐢𝐟𝐢𝐜𝐢𝐚𝐥 𝐈𝐧𝐭𝐞𝐥𝐥𝐢𝐠𝐞𝐧𝐜𝐞: 𝐈𝐧𝐧𝐨𝐯𝐚𝐭𝐢𝐨𝐧 𝐨𝐫 𝐑𝐢𝐬𝐤?
AI is changing the way we work, make things, and connect with the world surrounding us but with these changes come additional challenges we have to address and be responsible for.
☑️ This is what we are up against 👇
🔸 Model Bias➡️Biased results by poorly trained models.
🔸Privacy Breaches➡️Data from users is gathered and abused without their consent.
🔸Cyber Threats Controlled by AI➡️Attacks on autopilot that are more intelligent than traditional defenses.
🔸Oppague➡️ “Black box” systems with limited accountability.
🔸Energy Consumption: Significant energy required for AI computation.
🔸Misinformation & Deepfakes➡️fabricate content that influence our opinions and politics.
🔸Ethical Abuse ➡️ The misuse of technology even if it is cutting ethical boundaries.
☑️ 𝐑𝐞𝐚𝐥-𝐰𝐨𝐫𝐥𝐝 𝐬𝐜𝐞𝐧𝐚𝐫𝐢𝐨𝐬 ➡️𝐢𝐧𝐜𝐥𝐮𝐝𝐢𝐧𝐠 𝐀𝐈-𝐩𝐨𝐰𝐞𝐫𝐞𝐝 𝐡𝐢𝐫𝐢𝐧𝐠 𝐝𝐢𝐬𝐜𝐫𝐢𝐦𝐢𝐧𝐚𝐭𝐢𝐨𝐧 𝐭𝐨 𝐝𝐞𝐞𝐩𝐟𝐚𝐤𝐞 𝐩𝐨𝐥𝐢𝐭𝐢𝐜𝐚𝐥 𝐜𝐚𝐦𝐩𝐚𝐢𝐠𝐧𝐬 ➡️𝐬𝐞𝐫𝐯𝐞 𝐚𝐬 𝐚 𝐫𝐞𝐦𝐢𝐧𝐝𝐞𝐫 𝐭𝐡𝐚𝐭 𝐡𝐮𝐦𝐚𝐧 𝐨𝐯𝐞𝐫𝐬𝐢𝐠𝐡𝐭 𝐚𝐧𝐝 𝐫𝐞𝐠𝐮𝐥𝐚𝐭𝐢𝐨𝐧 𝐚𝐫𝐞 𝐧𝐨 𝐥𝐨𝐧𝐠𝐞𝐫 𝐨𝐩𝐭𝐢𝐨𝐧𝐚𝐥; 𝐭𝐡𝐞𝐲 𝐚𝐫𝐞 𝐞𝐬𝐬𝐞𝐧𝐭𝐢𝐚𝐥.
👉 𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/ai-associated-risks-and-how-to-mitigate-them/
🎓 Infosec Train AI and Cybersecurity Course empowers individuals to better comprehend the threats, develop ethical AI guidelines, and combat emerging digital threats leading to a safe and responsible AI-empowered future.
#ArtificialIntelligence #CyberSecurity #ResponsibleAI #AIethics #AIrisks #DataPrivacy #Deepfakes #TechResponsibility #EthicalAI #AIawareness #DigitalSafety #RiskManagement #Governance #AItraining #InfoSecTrain