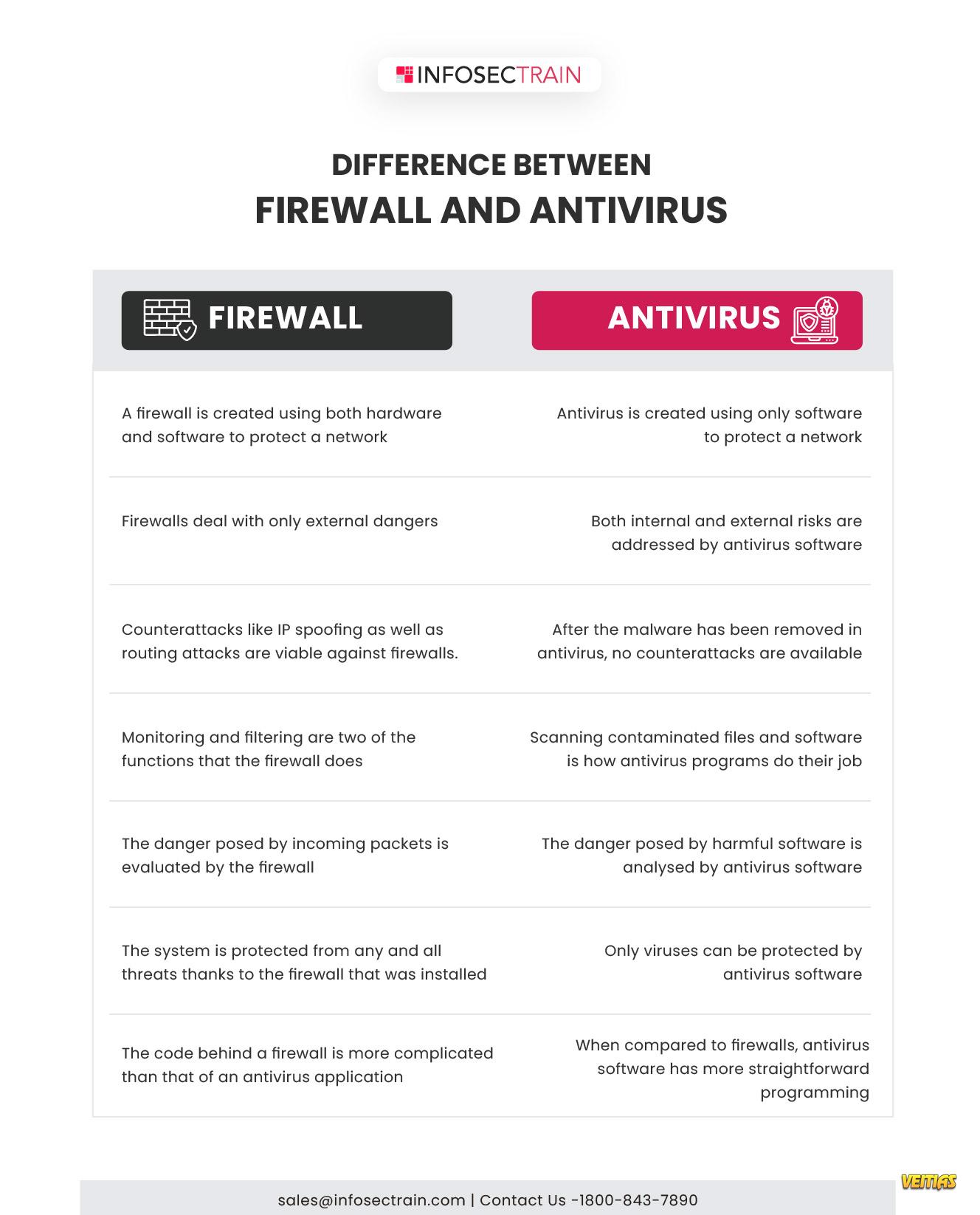
Protect Your Digital Assets with a Strong Security Architecture
Cyber threats are everywhere from hackers and malware to insider threats and accidental data leaks. Just like you wouldn’t leave your house unlocked, you shouldn’t leave your digital systems unprotected. That’s where Security Architecture steps in.
Think of security architecture as the blueprint for protecting your digital world. It’s not just about installing antivirus software or using a strong password. It’s about designing your entire IT setup from networks to apps with security built into every layer.
Want to learn more? Read the full article here: https://www.infosectrain.com/blog/key-elements-of-security-architecture/
Stay Ahead in Cybersecurity https://www.linkedin.com/company/infosec-train/posts/?feedView=all for the latest updates on training programs, free webinars, expert insights and industry trends in Cybersecurity, Cloud, GRC, and more.
#CyberSecurity #SecurityArchitecture #DigitalProtection #ZeroTrust #IAM #ApplicationSecurity #TechSecurity #DataSecurity #NetworkSecurity #Infosectrain
Cyber threats are everywhere from hackers and malware to insider threats and accidental data leaks. Just like you wouldn’t leave your house unlocked, you shouldn’t leave your digital systems unprotected. That’s where Security Architecture steps in.
Think of security architecture as the blueprint for protecting your digital world. It’s not just about installing antivirus software or using a strong password. It’s about designing your entire IT setup from networks to apps with security built into every layer.
Want to learn more? Read the full article here: https://www.infosectrain.com/blog/key-elements-of-security-architecture/
Stay Ahead in Cybersecurity https://www.linkedin.com/company/infosec-train/posts/?feedView=all for the latest updates on training programs, free webinars, expert insights and industry trends in Cybersecurity, Cloud, GRC, and more.
#CyberSecurity #SecurityArchitecture #DigitalProtection #ZeroTrust #IAM #ApplicationSecurity #TechSecurity #DataSecurity #NetworkSecurity #Infosectrain
Protect Your Digital Assets with a Strong Security Architecture
Cyber threats are everywhere from hackers and malware to insider threats and accidental data leaks. Just like you wouldn’t leave your house unlocked, you shouldn’t leave your digital systems unprotected. That’s where Security Architecture steps in.
Think of security architecture as the blueprint for protecting your digital world. It’s not just about installing antivirus software or using a strong password. It’s about designing your entire IT setup from networks to apps with security built into every layer.
🔗 Want to learn more? Read the full article here: https://www.infosectrain.com/blog/key-elements-of-security-architecture/
Stay Ahead in Cybersecurity 👉 https://www.linkedin.com/company/infosec-train/posts/?feedView=all for the latest updates on training programs, free webinars, expert insights and industry trends in Cybersecurity, Cloud, GRC, and more.
#CyberSecurity #SecurityArchitecture #DigitalProtection #ZeroTrust #IAM #ApplicationSecurity #TechSecurity #DataSecurity #NetworkSecurity #Infosectrain
0 Comments
0 Shares
6068 Views
0 Reviews