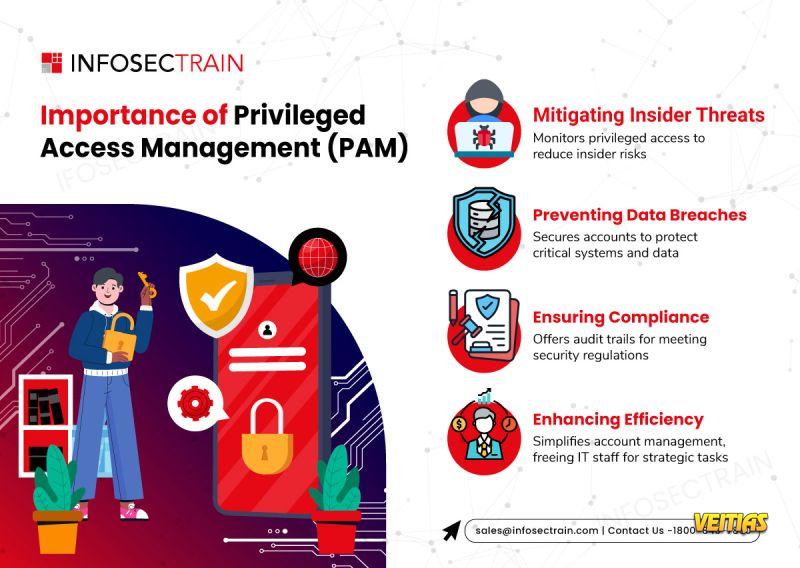
Insider Threats? Use Separation of Duties to Stay Safe!
In this video, we break down Separation of Duties (SoD)—a critical cybersecurity principle that helps prevent fraud, misuse, and insider threats by ensuring no single individual controls all critical processes. You will learn how SoD is applied across IT operations, why it is essential for protecting sensitive systems and data, and how it supports regulatory compliance with standards such as SOX, HIPAA, and ISO 27001.
Watch Here: https://youtu.be/6w6r97Pl6do?si=9d7wu-wQ1V2jGeAR
#CyberSecurity #SeparationOfDuties #InsiderThreats #IAM #ITSecurity #RiskManagement #ISO27001 #SOX #HIPAA #CyberAwareness
In this video, we break down Separation of Duties (SoD)—a critical cybersecurity principle that helps prevent fraud, misuse, and insider threats by ensuring no single individual controls all critical processes. You will learn how SoD is applied across IT operations, why it is essential for protecting sensitive systems and data, and how it supports regulatory compliance with standards such as SOX, HIPAA, and ISO 27001.
Watch Here: https://youtu.be/6w6r97Pl6do?si=9d7wu-wQ1V2jGeAR
#CyberSecurity #SeparationOfDuties #InsiderThreats #IAM #ITSecurity #RiskManagement #ISO27001 #SOX #HIPAA #CyberAwareness
Insider Threats? Use Separation of Duties to Stay Safe!
In this video, we break down Separation of Duties (SoD)—a critical cybersecurity principle that helps prevent fraud, misuse, and insider threats by ensuring no single individual controls all critical processes. You will learn how SoD is applied across IT operations, why it is essential for protecting sensitive systems and data, and how it supports regulatory compliance with standards such as SOX, HIPAA, and ISO 27001.
Watch Here: https://youtu.be/6w6r97Pl6do?si=9d7wu-wQ1V2jGeAR
#CyberSecurity #SeparationOfDuties #InsiderThreats #IAM #ITSecurity #RiskManagement #ISO27001 #SOX #HIPAA #CyberAwareness

0 Comments
0 Shares
2777 Views
0 Reviews