𝐈𝐒𝐂𝟐 𝐈𝐒𝐒𝐀𝐏 𝐃𝐨𝐦𝐚𝐢𝐧 𝟒: 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐚𝐧𝐝 𝐀𝐜𝐜𝐞𝐬𝐬 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭 (𝐈𝐀𝐌) 𝐀𝐫𝐜𝐡𝐢𝐭𝐞𝐜𝐭𝐮𝐫𝐞
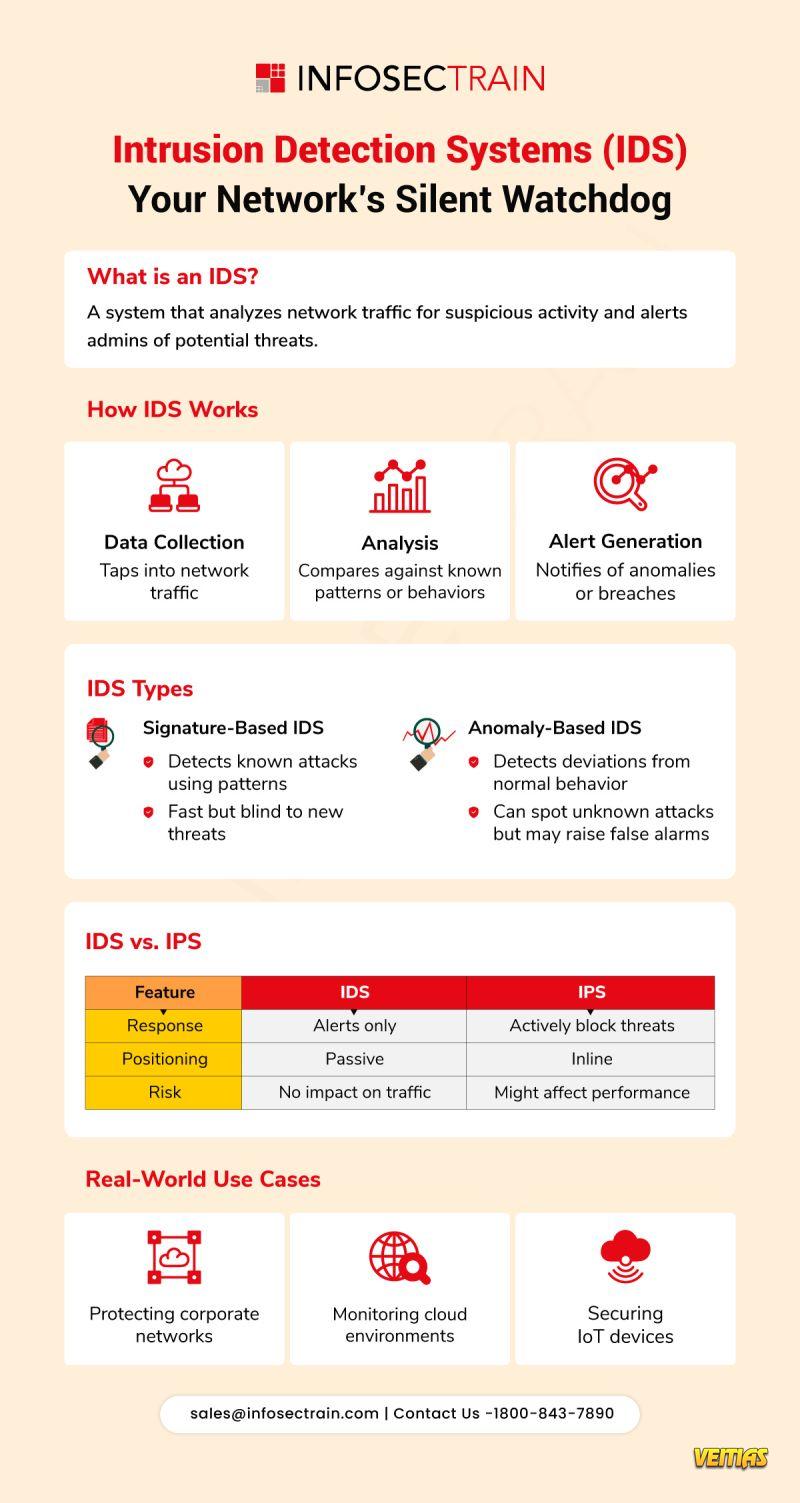
In the present-day cloud workloads, remote working, and IoT devices scenario, the old physical office boundary has practically disappeared. Security experts claim that identity has turned out to be the most important security control point for organizations. In this digital world, individuals as well as devices need to authenticate themselves first before getting access.
Understanding IAM architecture is essential for modern security professionals.
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐟𝐮𝐥𝐥 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐚𝐫𝐭𝐢𝐜𝐥𝐞: https://www.infosectrain.com/blog/isc2-issap-domain-4-identity-and-access-management-iam-architecture
#CyberSecurity #IAM #ISC2 #ISSAP #IdentityManagement #CloudSecurity #ZeroTrust #InfosecTrain
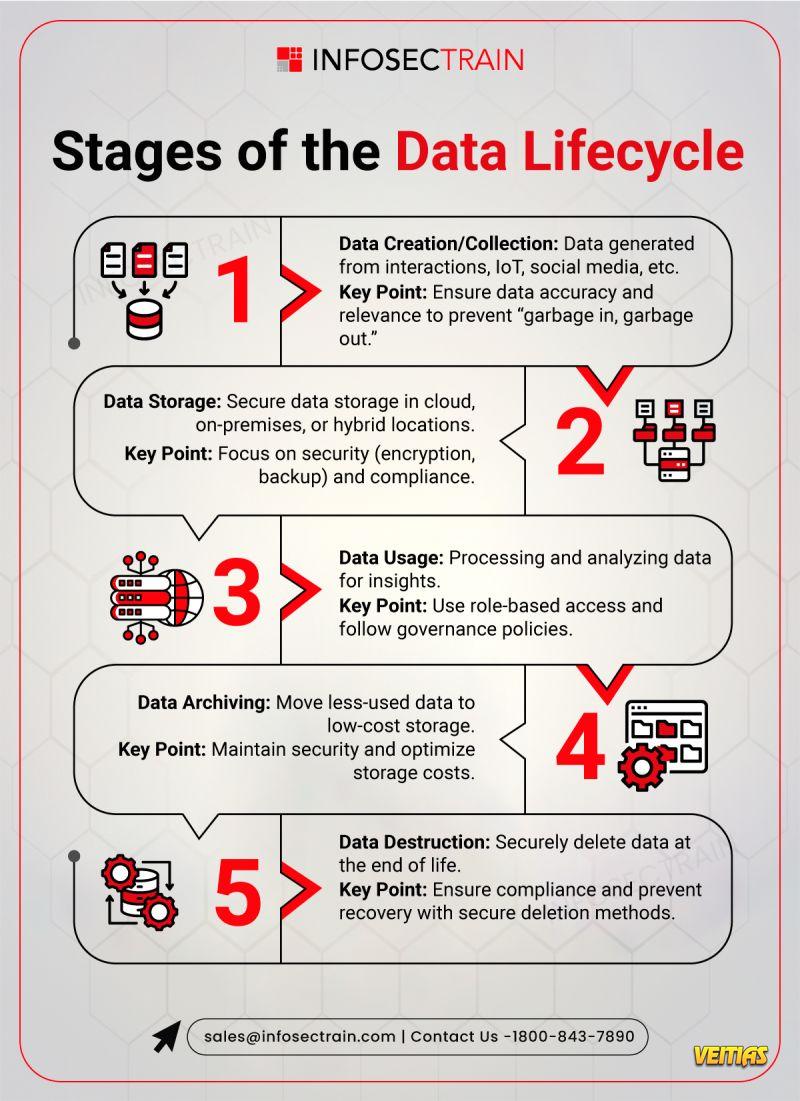
In the present-day cloud workloads, remote working, and IoT devices scenario, the old physical office boundary has practically disappeared. Security experts claim that identity has turned out to be the most important security control point for organizations. In this digital world, individuals as well as devices need to authenticate themselves first before getting access.
Understanding IAM architecture is essential for modern security professionals.
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐟𝐮𝐥𝐥 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐚𝐫𝐭𝐢𝐜𝐥𝐞: https://www.infosectrain.com/blog/isc2-issap-domain-4-identity-and-access-management-iam-architecture
#CyberSecurity #IAM #ISC2 #ISSAP #IdentityManagement #CloudSecurity #ZeroTrust #InfosecTrain
𝐈𝐒𝐂𝟐 𝐈𝐒𝐒𝐀𝐏 𝐃𝐨𝐦𝐚𝐢𝐧 𝟒: 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐚𝐧𝐝 𝐀𝐜𝐜𝐞𝐬𝐬 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭 (𝐈𝐀𝐌) 𝐀𝐫𝐜𝐡𝐢𝐭𝐞𝐜𝐭𝐮𝐫𝐞
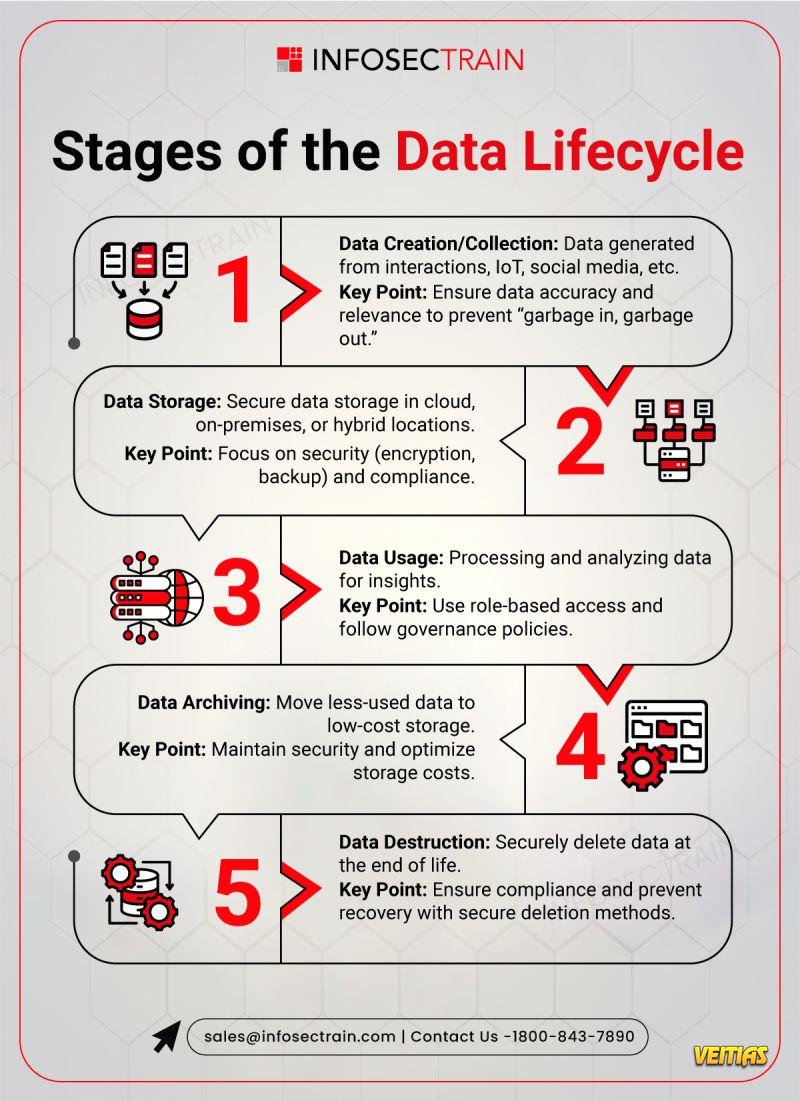
In the present-day cloud workloads, remote working, and IoT devices scenario, the old physical office boundary has practically disappeared. Security experts claim that identity has turned out to be the most important security control point for organizations. In this digital world, individuals as well as devices need to authenticate themselves first before getting access.
Understanding IAM architecture is essential for modern security professionals.
👉 𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐟𝐮𝐥𝐥 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐚𝐫𝐭𝐢𝐜𝐥𝐞: https://www.infosectrain.com/blog/isc2-issap-domain-4-identity-and-access-management-iam-architecture
#CyberSecurity #IAM #ISC2 #ISSAP #IdentityManagement #CloudSecurity #ZeroTrust #InfosecTrain
0 Comments
0 Shares
2352 Views
0 Reviews