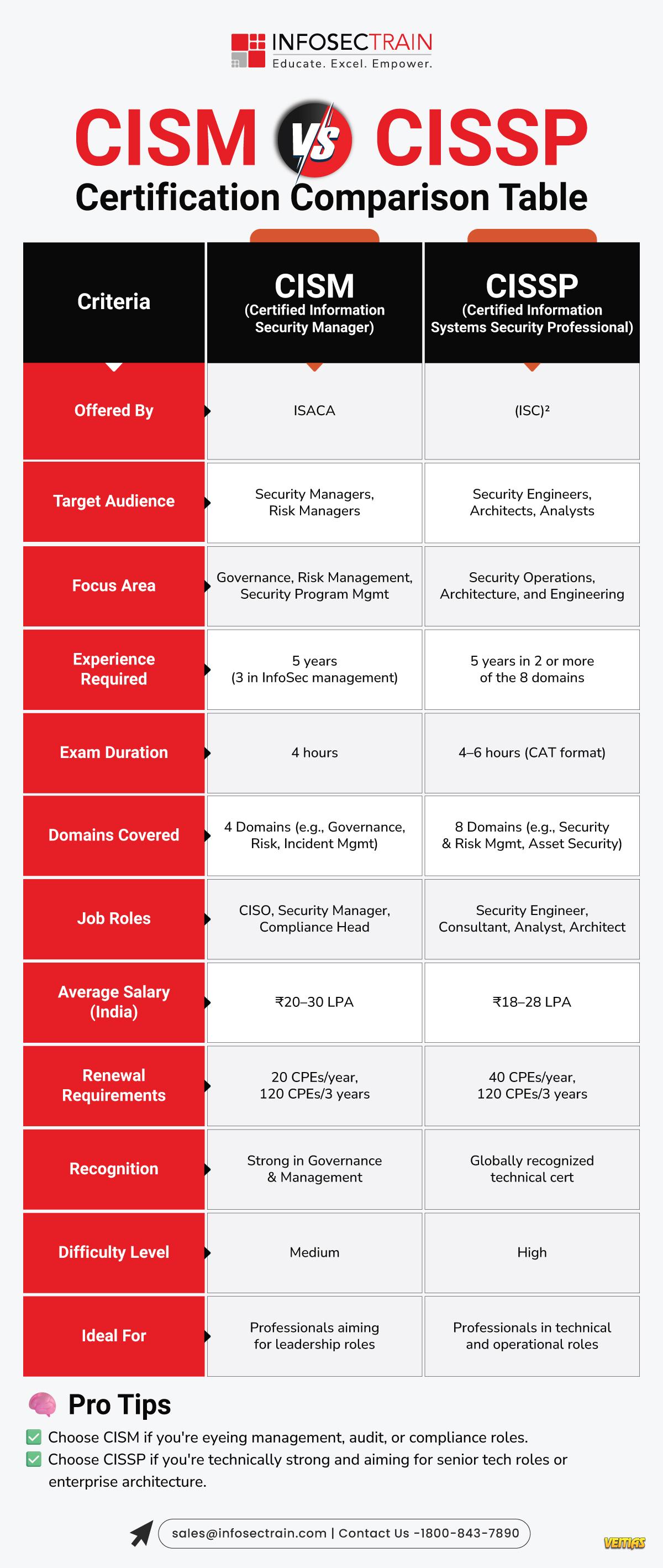
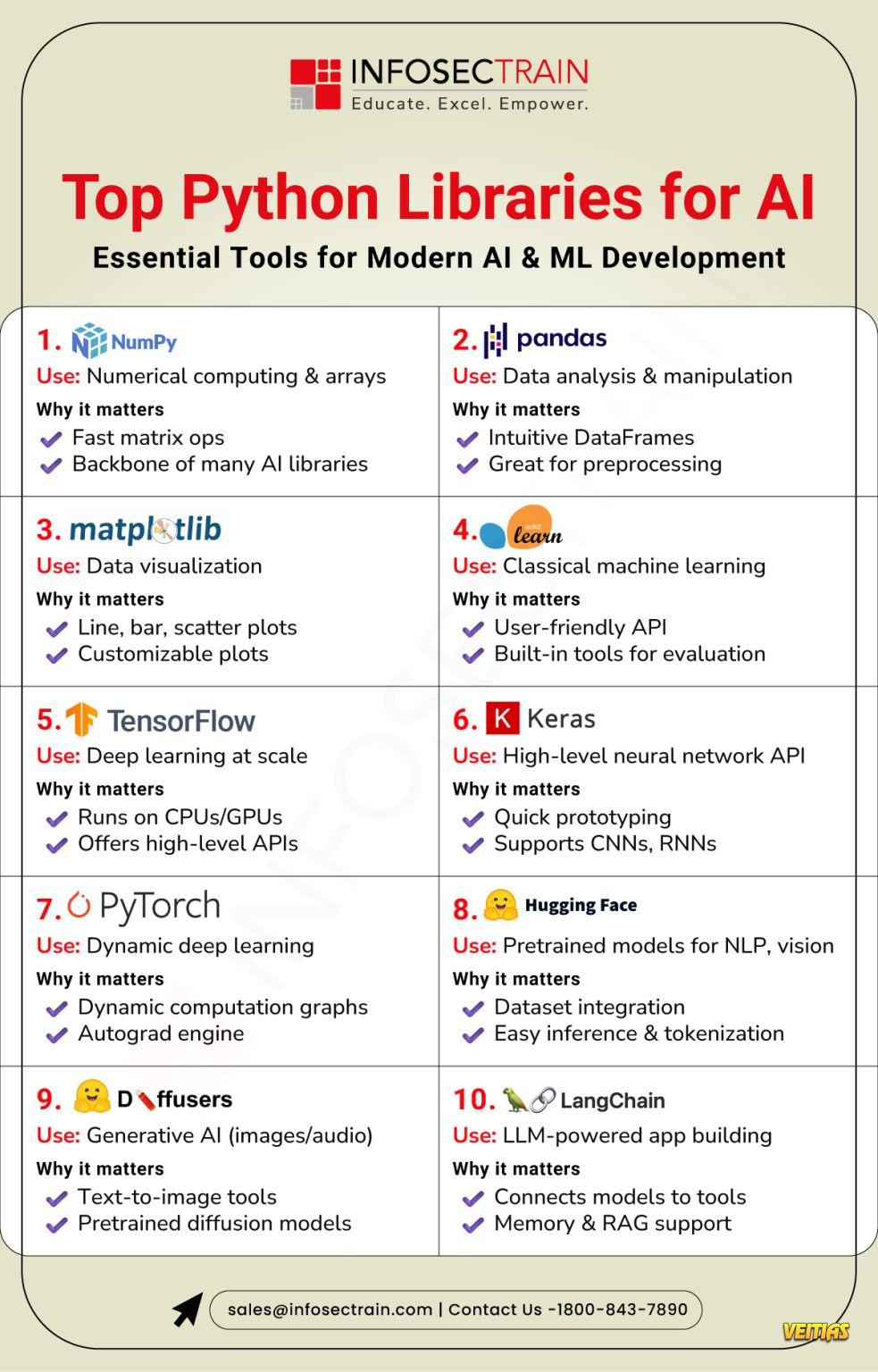
𝟏𝟓 𝐌𝐮𝐬𝐭-𝐇𝐚𝐯𝐞 𝐃𝐨𝐜𝐮𝐦𝐞𝐧𝐭𝐬 & 𝐄𝐯𝐢𝐝𝐞𝐧𝐜𝐞 𝐟𝐨𝐫 𝐚𝐧 𝐈𝐒𝐎/𝐈𝐄𝐂 𝟒𝟐𝟎𝟎𝟏 𝐀𝐮𝐝𝐢𝐭
Audits in the framework of ISO/IEC 42001 are not about your claim to have a process in place, they're about proving that you have a consistently applied process in place.
𝐖𝐢𝐭𝐡 𝟐𝟎𝟐𝟓 𝐛𝐫𝐢𝐧𝐠𝐢𝐧𝐠 𝐬𝐭𝐫𝐢𝐜𝐭𝐞𝐫 𝐀𝐈 𝐫𝐞𝐠𝐮𝐥𝐚𝐭𝐢𝐨𝐧𝐬. Hence, the alignment with ISO/IEC 42001 is quickly being recognized as the standard for the maturity, transparency, and trust of AI. Documentation plays the role of the immune system in AI governance, demonstrating the manner in which your AI systems are being designed, deployed, and controlled.
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/15-must-have-documents-evidence-for-an-iso-iec-42001-audit
𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐈𝐒𝐎/𝐈𝐄𝐂 𝟒𝟐𝟎𝟎𝟏 𝐋𝐞𝐚𝐝 𝐀𝐮𝐝𝐢𝐭𝐨𝐫 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 equips professionals with the skills to conduct evidence-based AI audits that meet global expectations.
#ISO42001 #AIGovernance #ResponsibleAI #AIAudits #Compliance #RiskManagement #infosectrain #learntorise
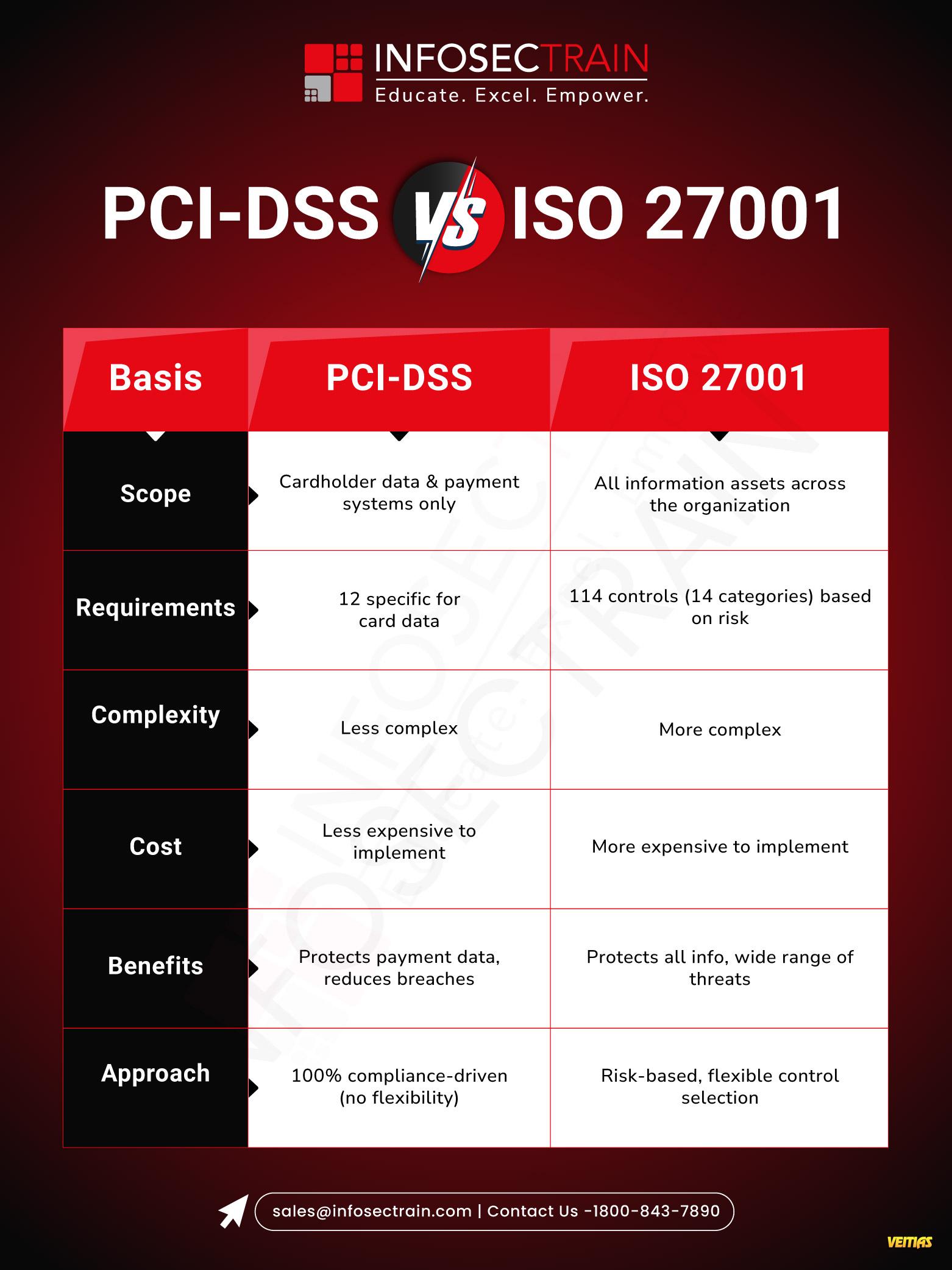
Audits in the framework of ISO/IEC 42001 are not about your claim to have a process in place, they're about proving that you have a consistently applied process in place.
𝐖𝐢𝐭𝐡 𝟐𝟎𝟐𝟓 𝐛𝐫𝐢𝐧𝐠𝐢𝐧𝐠 𝐬𝐭𝐫𝐢𝐜𝐭𝐞𝐫 𝐀𝐈 𝐫𝐞𝐠𝐮𝐥𝐚𝐭𝐢𝐨𝐧𝐬. Hence, the alignment with ISO/IEC 42001 is quickly being recognized as the standard for the maturity, transparency, and trust of AI. Documentation plays the role of the immune system in AI governance, demonstrating the manner in which your AI systems are being designed, deployed, and controlled.
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/15-must-have-documents-evidence-for-an-iso-iec-42001-audit
𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐈𝐒𝐎/𝐈𝐄𝐂 𝟒𝟐𝟎𝟎𝟏 𝐋𝐞𝐚𝐝 𝐀𝐮𝐝𝐢𝐭𝐨𝐫 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 equips professionals with the skills to conduct evidence-based AI audits that meet global expectations.
#ISO42001 #AIGovernance #ResponsibleAI #AIAudits #Compliance #RiskManagement #infosectrain #learntorise
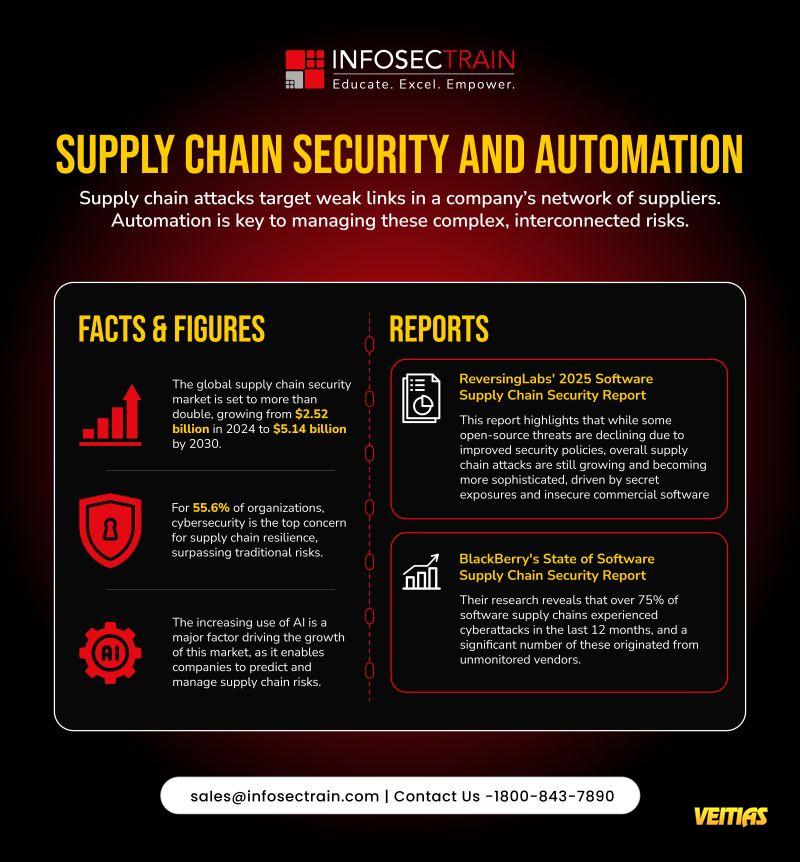
𝟏𝟓 𝐌𝐮𝐬𝐭-𝐇𝐚𝐯𝐞 𝐃𝐨𝐜𝐮𝐦𝐞𝐧𝐭𝐬 & 𝐄𝐯𝐢𝐝𝐞𝐧𝐜𝐞 𝐟𝐨𝐫 𝐚𝐧 𝐈𝐒𝐎/𝐈𝐄𝐂 𝟒𝟐𝟎𝟎𝟏 𝐀𝐮𝐝𝐢𝐭
Audits in the framework of ISO/IEC 42001 are not about your claim to have a process in place, they're about proving that you have a consistently applied process in place.
𝐖𝐢𝐭𝐡 𝟐𝟎𝟐𝟓 𝐛𝐫𝐢𝐧𝐠𝐢𝐧𝐠 𝐬𝐭𝐫𝐢𝐜𝐭𝐞𝐫 𝐀𝐈 𝐫𝐞𝐠𝐮𝐥𝐚𝐭𝐢𝐨𝐧𝐬. Hence, the alignment with ISO/IEC 42001 is quickly being recognized as the standard for the maturity, transparency, and trust of AI. Documentation plays the role of the immune system in AI governance, demonstrating the manner in which your AI systems are being designed, deployed, and controlled.
👉 𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/15-must-have-documents-evidence-for-an-iso-iec-42001-audit
✅ 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐈𝐒𝐎/𝐈𝐄𝐂 𝟒𝟐𝟎𝟎𝟏 𝐋𝐞𝐚𝐝 𝐀𝐮𝐝𝐢𝐭𝐨𝐫 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 equips professionals with the skills to conduct evidence-based AI audits that meet global expectations.
#ISO42001 #AIGovernance #ResponsibleAI #AIAudits #Compliance #RiskManagement #infosectrain #learntorise
0 Yorumlar
0 hisse senetleri
3011 Views
0 önizleme