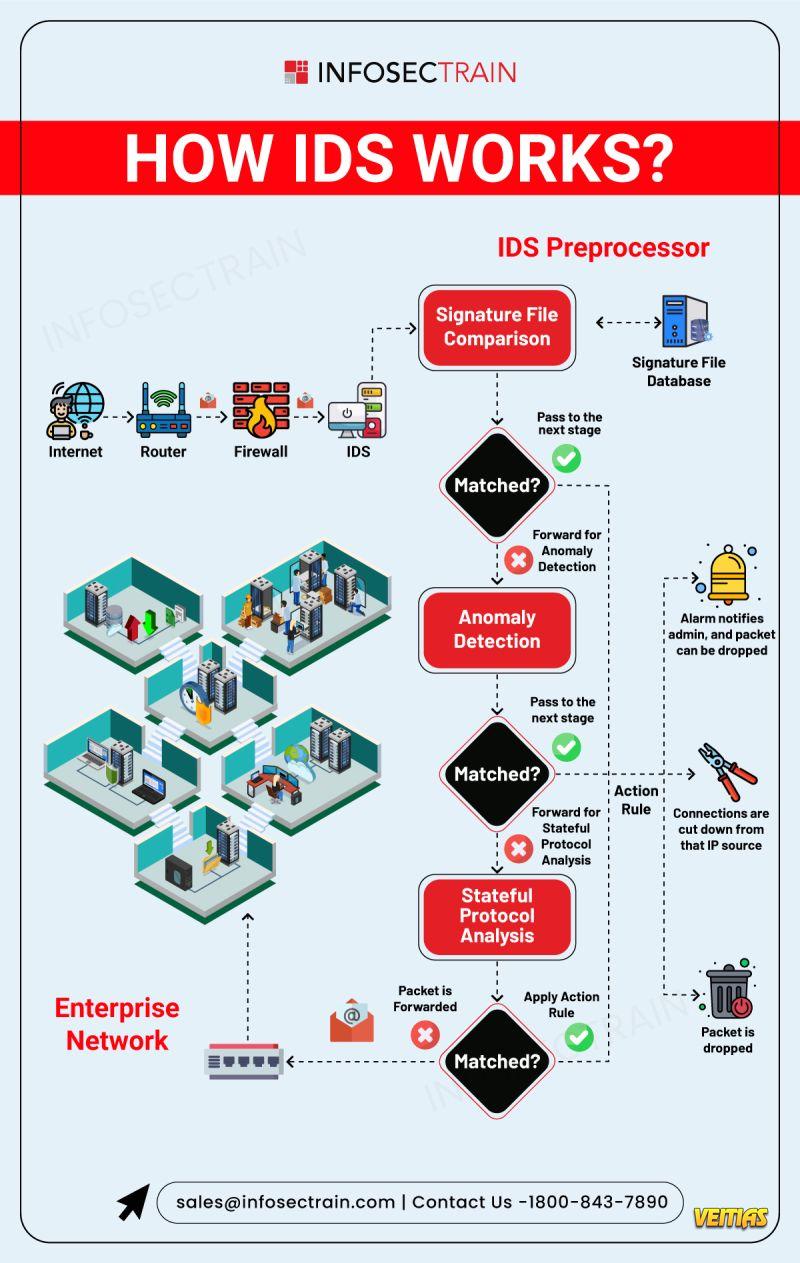
Ever wondered how your network stays safe from intrusions?
Here’s a quick look at How an Intrusion Detection System (IDS) works.
Key highlights:
✔ Matches traffic with known threat signatures
✔ Detects unusual behaviors
✔ Takes action before threats reach your systems
Follow us for more cybersecurity insights!
Reach out: sales@infosectrain.com | 1800-843-7890
#IntrusionDetectionSystem #IDS #CyberSecurity #NetworkSecurity #ThreatDetection #InfoSec #CyberDefense #ITSecurity #DigitalSafety #Firewall #SecurityTools #CyberAwareness #MalwareDetection #SecuritySolutions #AnomalyDetection #StatefulInspection #InfosecTrain
Here’s a quick look at How an Intrusion Detection System (IDS) works.
Key highlights:
✔ Matches traffic with known threat signatures
✔ Detects unusual behaviors
✔ Takes action before threats reach your systems
Follow us for more cybersecurity insights!
Reach out: sales@infosectrain.com | 1800-843-7890
#IntrusionDetectionSystem #IDS #CyberSecurity #NetworkSecurity #ThreatDetection #InfoSec #CyberDefense #ITSecurity #DigitalSafety #Firewall #SecurityTools #CyberAwareness #MalwareDetection #SecuritySolutions #AnomalyDetection #StatefulInspection #InfosecTrain
Ever wondered how your network stays safe from intrusions?
Here’s a quick look at How an Intrusion Detection System (IDS) works.
🔔 Key highlights:
✔ Matches traffic with known threat signatures
✔ Detects unusual behaviors
✔ Takes action before threats reach your systems
📲 Follow us for more cybersecurity insights!
📧 Reach out: sales@infosectrain.com | 📞 1800-843-7890
#IntrusionDetectionSystem #IDS #CyberSecurity #NetworkSecurity #ThreatDetection #InfoSec #CyberDefense #ITSecurity #DigitalSafety #Firewall #SecurityTools #CyberAwareness #MalwareDetection #SecuritySolutions #AnomalyDetection #StatefulInspection #InfosecTrain
0 Commenti
0 condivisioni
5567 Views
0 Anteprima