Human Error vs Technological Vulnerabilities
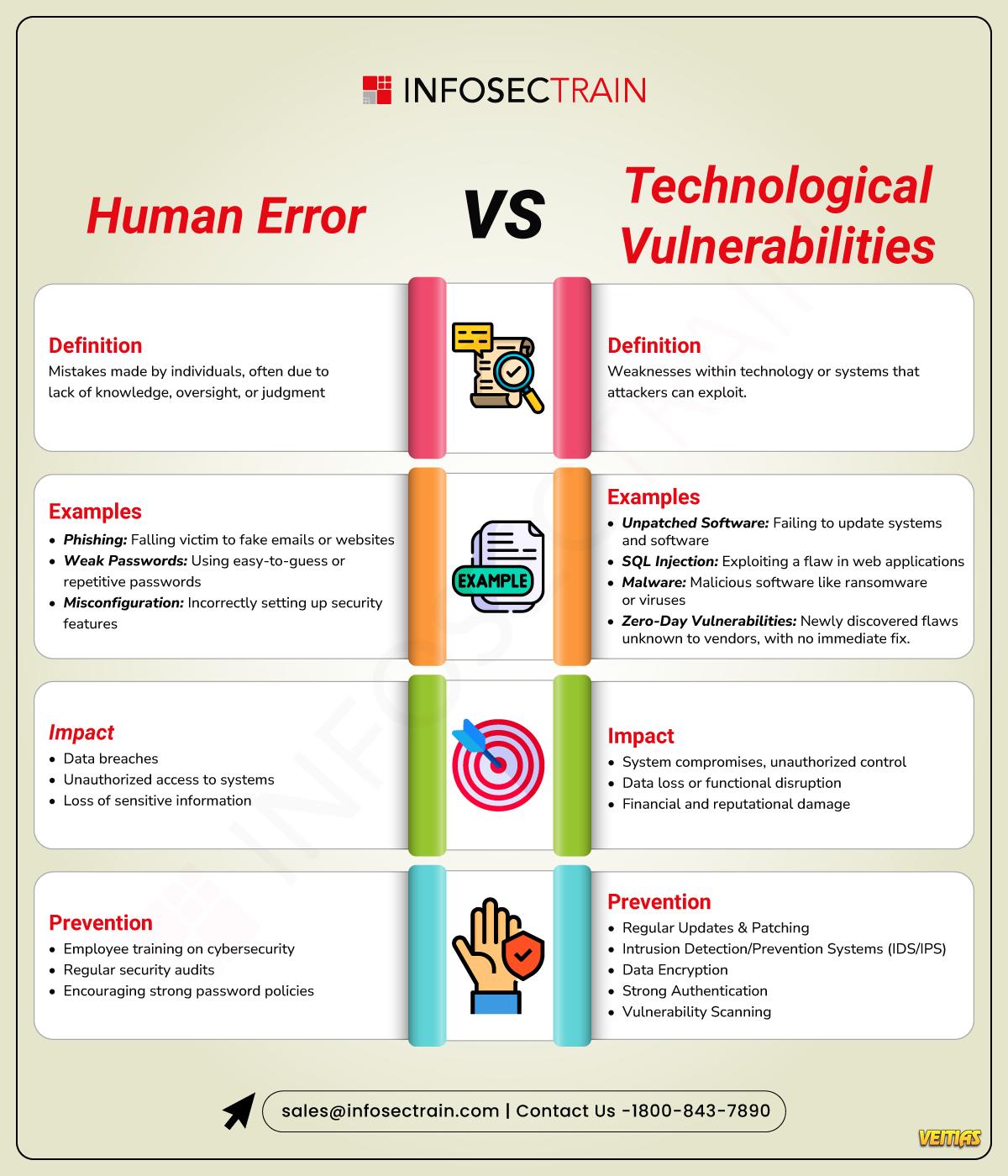
InfosecTrain’s latest infographic draws a clear comparison between human error and technological vulnerabilities—two major causes of security breaches. It explains their definitions, real-world examples, impacts, and prevention strategies, helping professionals better understand where risks originate and how to reduce them effectively.
How to Prevent the Most Common Cyber Attacks: https://www.infosectrain.com/blog/how-to-prevent-the-most-common-cyber-attacks/
#CyberSecurity #HumanError #Vulnerabilities #InfoSec #SecurityAwareness #CyberThreats #RiskManagement #DataProtection #SecurityTraining #InfosecTrain
InfosecTrain’s latest infographic draws a clear comparison between human error and technological vulnerabilities—two major causes of security breaches. It explains their definitions, real-world examples, impacts, and prevention strategies, helping professionals better understand where risks originate and how to reduce them effectively.
How to Prevent the Most Common Cyber Attacks: https://www.infosectrain.com/blog/how-to-prevent-the-most-common-cyber-attacks/
#CyberSecurity #HumanError #Vulnerabilities #InfoSec #SecurityAwareness #CyberThreats #RiskManagement #DataProtection #SecurityTraining #InfosecTrain
Human Error vs Technological Vulnerabilities
InfosecTrain’s latest infographic draws a clear comparison between human error and technological vulnerabilities—two major causes of security breaches. It explains their definitions, real-world examples, impacts, and prevention strategies, helping professionals better understand where risks originate and how to reduce them effectively.
How to Prevent the Most Common Cyber Attacks: https://www.infosectrain.com/blog/how-to-prevent-the-most-common-cyber-attacks/
#CyberSecurity #HumanError #Vulnerabilities #InfoSec #SecurityAwareness #CyberThreats #RiskManagement #DataProtection #SecurityTraining #InfosecTrain
0 Commenti
0 condivisioni
3763 Views
0 Anteprima