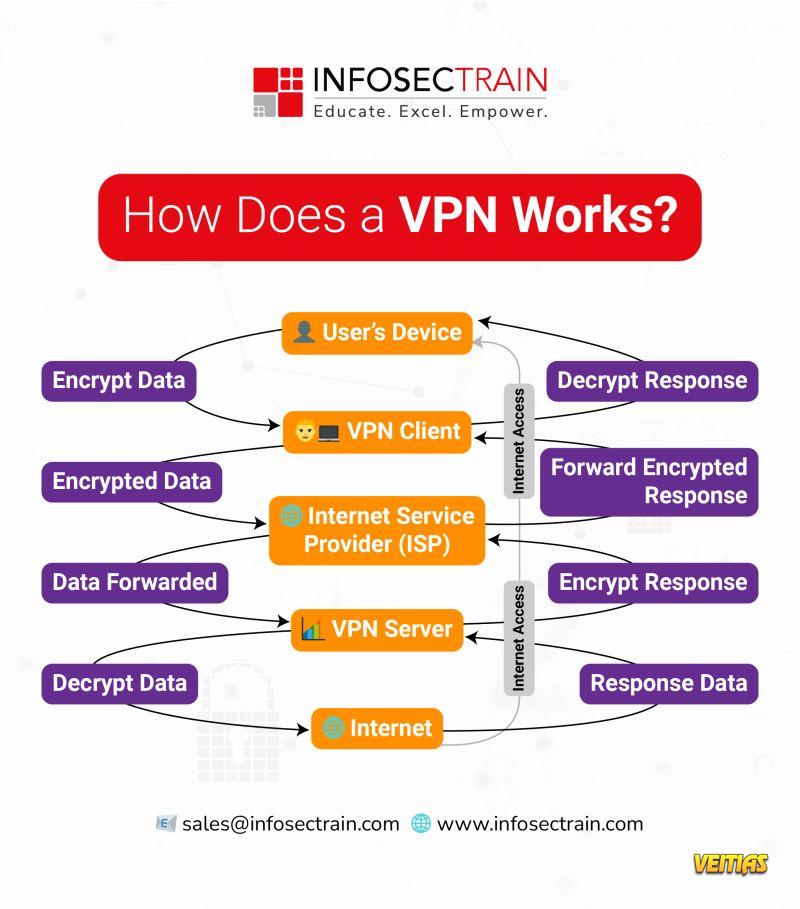
Ever wondered how a VPN actually works?
It creates a secure, encrypted tunnel between your device and the internet, hiding your IP address, protecting sensitive data, and keeping hackers away.
Browse safely on public Wi-Fi
Keep your identity private
Access content securely from anywhere
In short, it’s your digital shield in today’s online world!
Don’t miss out! Enroll here to join InfosecTrain Free Webinar and unlock expert insights. https://www.infosectrain.com/events/
#VPN #CyberSecurity #OnlinePrivacy #StaySafeOnline #DataProtection #TechTips
It creates a secure, encrypted tunnel between your device and the internet, hiding your IP address, protecting sensitive data, and keeping hackers away.
Browse safely on public Wi-Fi
Keep your identity private
Access content securely from anywhere
In short, it’s your digital shield in today’s online world!
Don’t miss out! Enroll here to join InfosecTrain Free Webinar and unlock expert insights. https://www.infosectrain.com/events/
#VPN #CyberSecurity #OnlinePrivacy #StaySafeOnline #DataProtection #TechTips
🔒 Ever wondered how a VPN actually works?
It creates a secure, encrypted tunnel between your device and the internet, hiding your IP address, protecting sensitive data, and keeping hackers away.
🌍 Browse safely on public Wi-Fi
🔒 Keep your identity private
🚀 Access content securely from anywhere
In short, it’s your digital shield in today’s online world!
Don’t miss out! 🎯 Enroll here to join InfosecTrain Free Webinar and unlock expert insights. 👉 https://www.infosectrain.com/events/
#VPN #CyberSecurity #OnlinePrivacy #StaySafeOnline #DataProtection #TechTips
0 Commentarios
0 Acciones
1516 Views
0 Vista previa