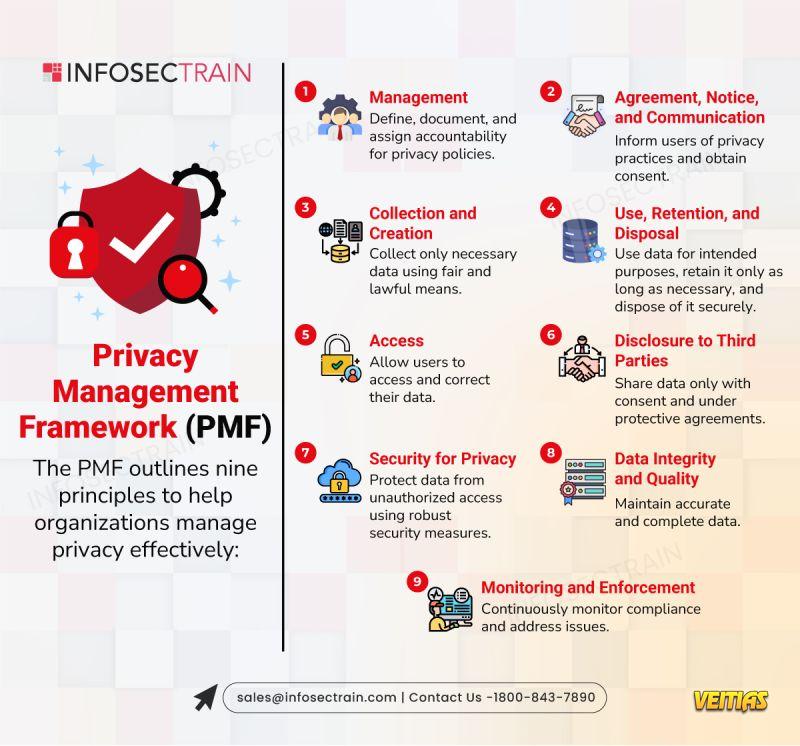
Enterprise AI Governance Vs. Responsible AI Governance
AI is transforming businesses but without structured governance, it can also create massive operational, ethical, and compliance risks. To deploy AI successfully, organizations must balance efficiency with trust.
Read Here: https://infosec-train.blogspot.com/2025/11/enterprise-ai-governance-vs-responsible-ai-governance.html
#AI #AIGovernance #ResponsibleAI #EnterpriseAI #AICompliance #EthicalAI #BiasMitigation #MLOps #XAI #DataSecurity #TrustworthyAI #RiskManagement #CAIGS #InfoSecTrain #DigitalTransformation #FutureOfAI
AI is transforming businesses but without structured governance, it can also create massive operational, ethical, and compliance risks. To deploy AI successfully, organizations must balance efficiency with trust.
Read Here: https://infosec-train.blogspot.com/2025/11/enterprise-ai-governance-vs-responsible-ai-governance.html
#AI #AIGovernance #ResponsibleAI #EnterpriseAI #AICompliance #EthicalAI #BiasMitigation #MLOps #XAI #DataSecurity #TrustworthyAI #RiskManagement #CAIGS #InfoSecTrain #DigitalTransformation #FutureOfAI
Enterprise AI Governance Vs. Responsible AI Governance
AI is transforming businesses but without structured governance, it can also create massive operational, ethical, and compliance risks. To deploy AI successfully, organizations must balance efficiency with trust.
Read Here: https://infosec-train.blogspot.com/2025/11/enterprise-ai-governance-vs-responsible-ai-governance.html
#AI #AIGovernance #ResponsibleAI #EnterpriseAI #AICompliance #EthicalAI #BiasMitigation #MLOps #XAI #DataSecurity #TrustworthyAI #RiskManagement #CAIGS #InfoSecTrain #DigitalTransformation #FutureOfAI
0 Comentários
0 Compartilhamentos
653 Visualizações
0 Anterior