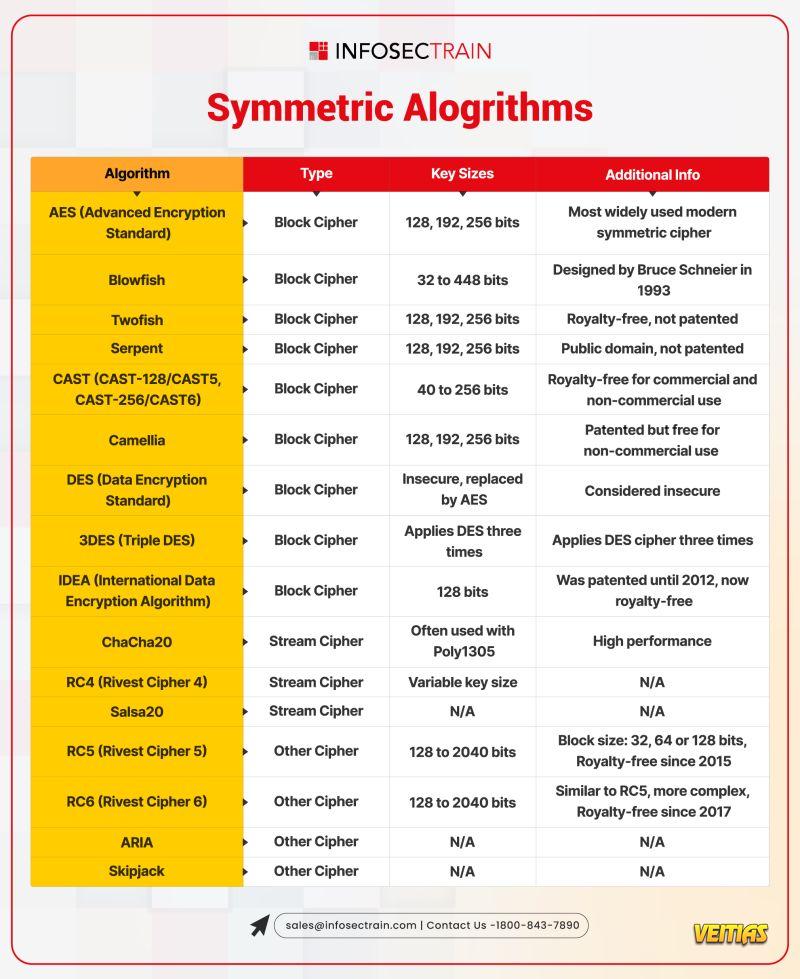
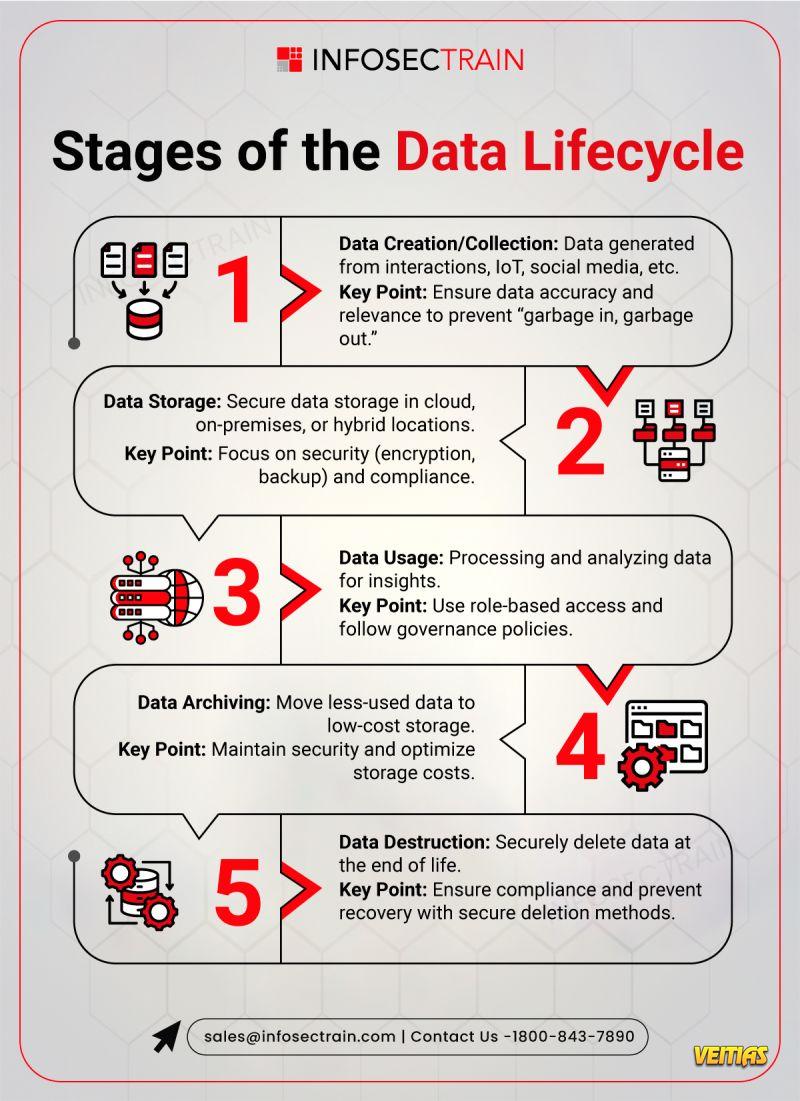
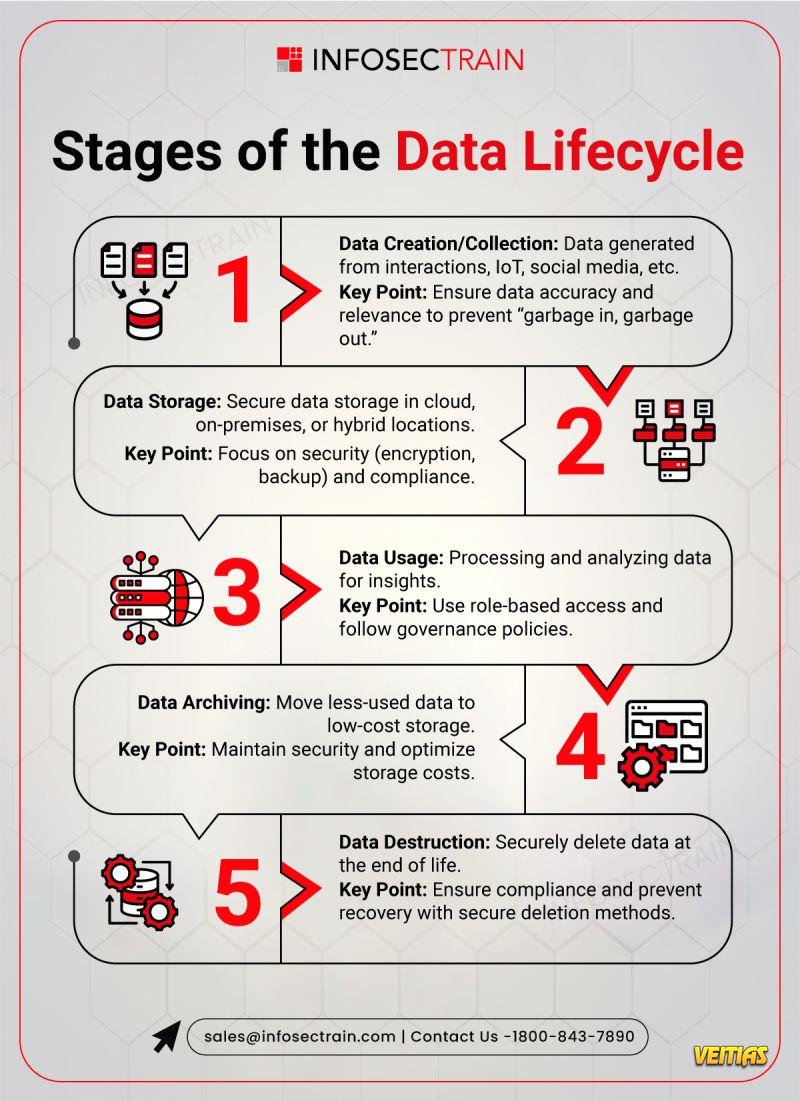
Free Masterclass: Perplexity AI – The Answer Engine for Verifiable Research
Stop searching. Start getting fact-checked answers with sources.
Date: 03 Feb 2026 (Tue)
Time: 8 – 9 PM (IST)
Speaker: Anas Hamid
What you’ll learn:
How Perplexity AI works as an answer engine vs traditional search
How it combines AI models like GPT & Claude for faster, accurate insights
Master citable research & source verification
Use Focus & Collections for structured, academic-grade research
Boost productivity with Perplexity Pro workflows
Understand data storage, privacy & research history
Skills in fact-checking, research & academic writing
Why attend?
CPE Certificate
FREE career guidance & mentorship
Learn directly from industry experts
Register FREE now:
https://www.infosectrain.com/events/perplexity-ai-masterclass-the-answer-engine-for-verifiable-factual-research/
#PerplexityAI #AIMasterclass #ResearchWithAI #AIForProfessionals #WebinarAlert #InfosecTrain
Stop searching. Start getting fact-checked answers with sources.
Date: 03 Feb 2026 (Tue)
Time: 8 – 9 PM (IST)
Speaker: Anas Hamid
What you’ll learn:
How Perplexity AI works as an answer engine vs traditional search
How it combines AI models like GPT & Claude for faster, accurate insights
Master citable research & source verification
Use Focus & Collections for structured, academic-grade research
Boost productivity with Perplexity Pro workflows
Understand data storage, privacy & research history
Skills in fact-checking, research & academic writing
Why attend?
CPE Certificate
FREE career guidance & mentorship
Learn directly from industry experts
Register FREE now:
https://www.infosectrain.com/events/perplexity-ai-masterclass-the-answer-engine-for-verifiable-factual-research/
#PerplexityAI #AIMasterclass #ResearchWithAI #AIForProfessionals #WebinarAlert #InfosecTrain
🚀 Free Masterclass: Perplexity AI – The Answer Engine for Verifiable Research
Stop searching. Start getting fact-checked answers with sources. 🔍🤖
📅 Date: 03 Feb 2026 (Tue)
⏰ Time: 8 – 9 PM (IST)
🎤 Speaker: Anas Hamid
🔎 What you’ll learn:
✅ How Perplexity AI works as an answer engine vs traditional search
✅ How it combines AI models like GPT & Claude for faster, accurate insights
✅ Master citable research & source verification
✅ Use Focus & Collections for structured, academic-grade research
✅ Boost productivity with Perplexity Pro workflows
✅ Understand data storage, privacy & research history
✅ Skills in fact-checking, research & academic writing
🎯 Why attend?
✔️ CPE Certificate
✔️ FREE career guidance & mentorship
✔️ Learn directly from industry experts
👉 Register FREE now:
🔗 https://www.infosectrain.com/events/perplexity-ai-masterclass-the-answer-engine-for-verifiable-factual-research/
#PerplexityAI #AIMasterclass #ResearchWithAI #AIForProfessionals #WebinarAlert #InfosecTrain
0 التعليقات
0 المشاركات
3239 مشاهدة
0 معاينة