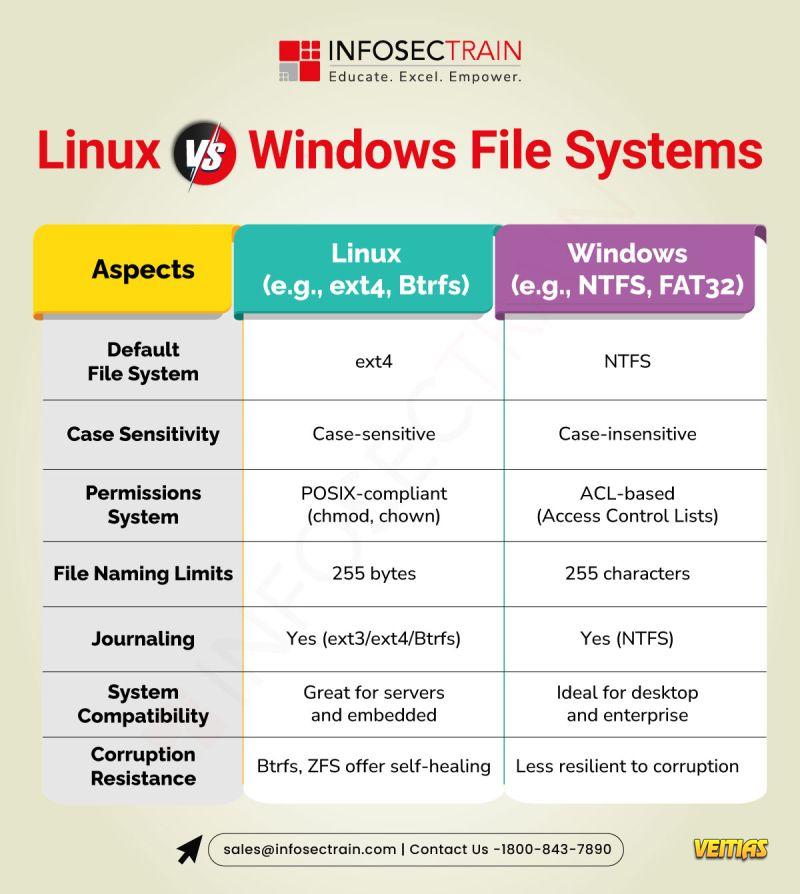
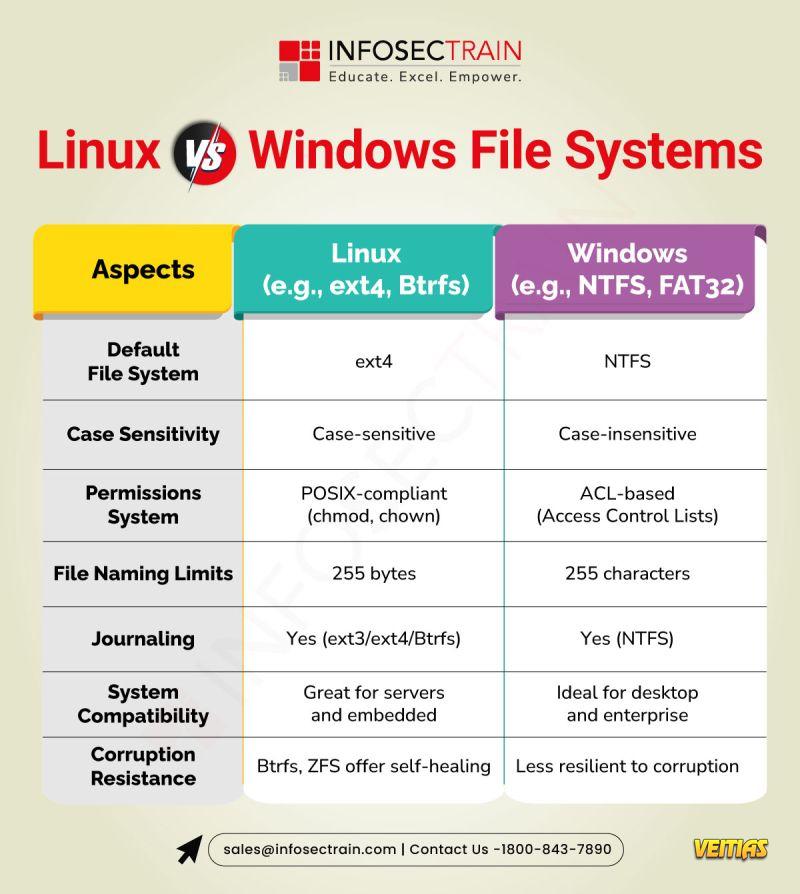
Linux commonly uses ext4, XFS, or Btrfs, which are designed for stability, security, and better handling of large files. These file systems support advanced features like journaling, symbolic links, and case sensitivity. Windows, on the other hand, mainly uses NTFS, which offers good compatibility, built-in encryption, and strong support for permissions but is less flexible than Linux file systems. In general, Linux file systems are preferred for servers and performance-heavy tasks, while NTFS is optimized for desktop use and Windows environments.
Linux commonly uses ext4, XFS, or Btrfs, which are designed for stability, security, and better handling of large files. These file systems support advanced features like journaling, symbolic links, and case sensitivity. Windows, on the other hand, mainly uses NTFS, which offers good compatibility, built-in encryption, and strong support for permissions but is less flexible than Linux file systems. In general, Linux file systems are preferred for servers and performance-heavy tasks, while NTFS is optimized for desktop use and Windows environments.
0 Comments
0 Shares
2416 Views
0 Reviews