Types of Firewalls Explained: A Practical Security Overview
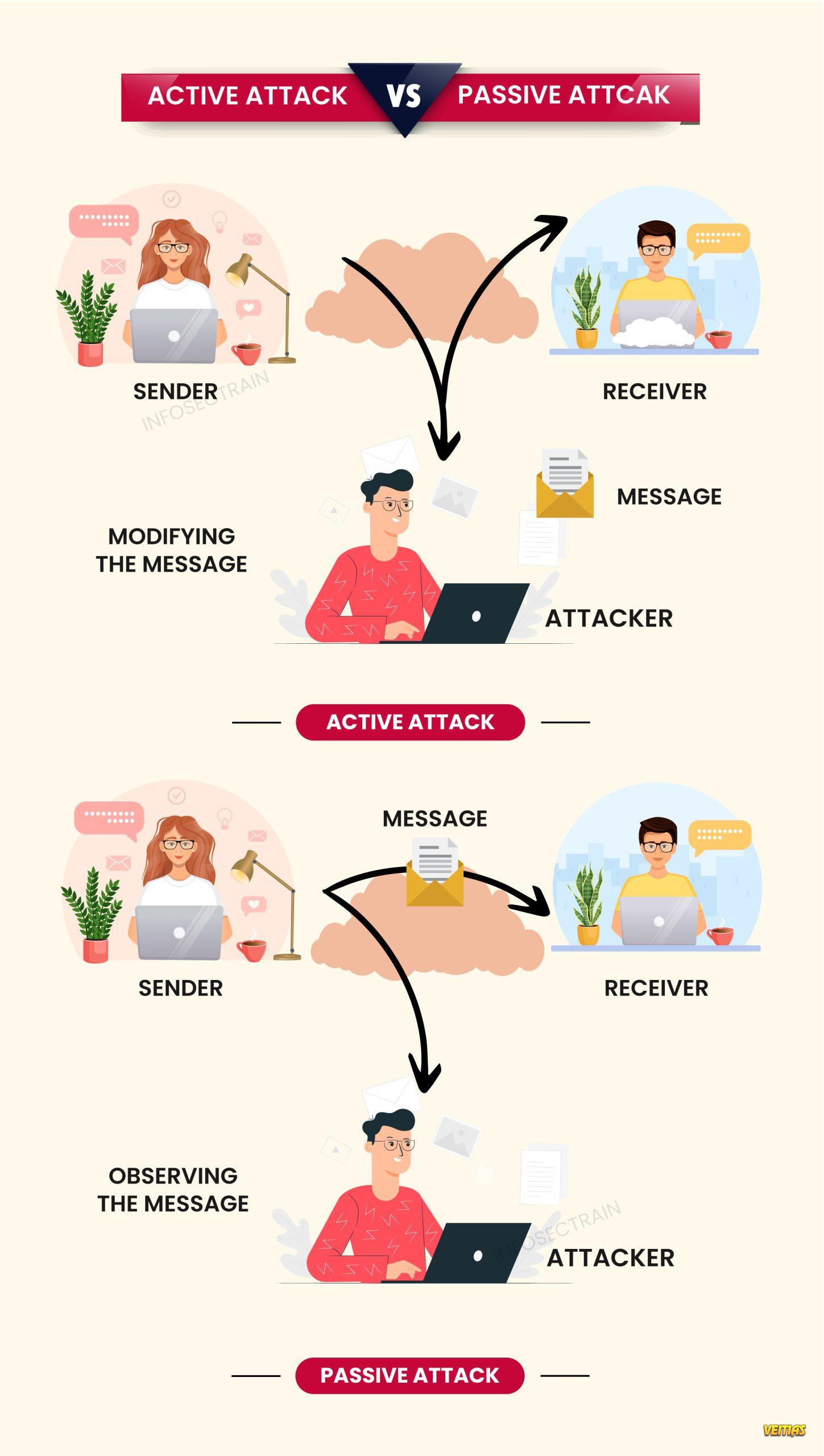
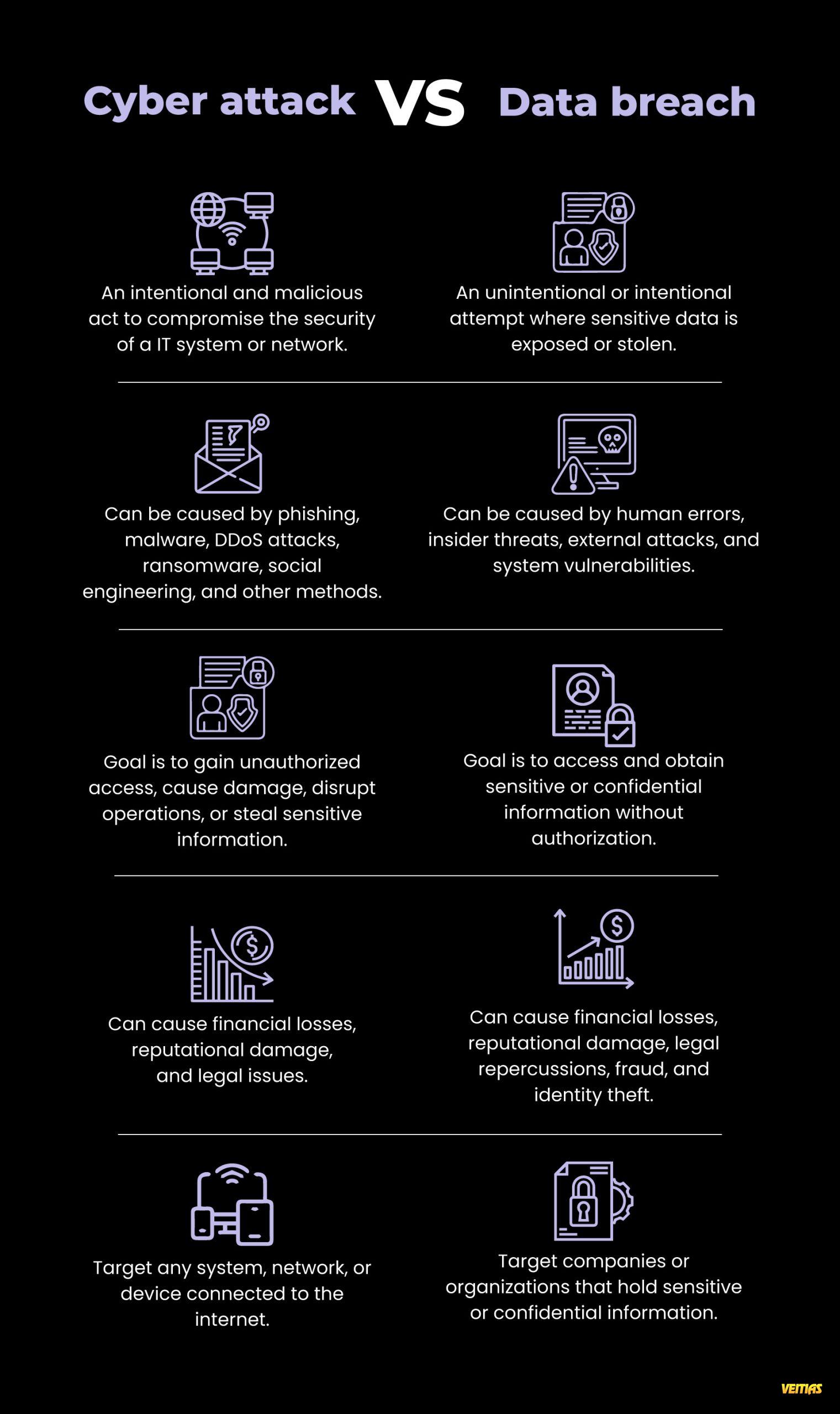
Firewalls are a foundational component of network security, designed to monitor and control incoming and outgoing traffic based on predefined rules. This visual overview explains the major types of firewalls, including packet filtering, proxy firewalls, stateful multi-layer inspection, unified threat management, next-generation firewalls, NAT firewalls, and virtual firewalls. Understanding these firewall types helps organizations choose the right security controls to protect networks, applications, and data from evolving cyber threats.
#CyberSecurity #NetworkSecurity #Firewalls #InfoSec #SecurityArchitecture #NGFW #UTM #ITSecurity #CyberDefense #Infosectrain
Firewalls are a foundational component of network security, designed to monitor and control incoming and outgoing traffic based on predefined rules. This visual overview explains the major types of firewalls, including packet filtering, proxy firewalls, stateful multi-layer inspection, unified threat management, next-generation firewalls, NAT firewalls, and virtual firewalls. Understanding these firewall types helps organizations choose the right security controls to protect networks, applications, and data from evolving cyber threats.
#CyberSecurity #NetworkSecurity #Firewalls #InfoSec #SecurityArchitecture #NGFW #UTM #ITSecurity #CyberDefense #Infosectrain
Types of Firewalls Explained: A Practical Security Overview
Firewalls are a foundational component of network security, designed to monitor and control incoming and outgoing traffic based on predefined rules. This visual overview explains the major types of firewalls, including packet filtering, proxy firewalls, stateful multi-layer inspection, unified threat management, next-generation firewalls, NAT firewalls, and virtual firewalls. Understanding these firewall types helps organizations choose the right security controls to protect networks, applications, and data from evolving cyber threats.
#CyberSecurity #NetworkSecurity #Firewalls #InfoSec #SecurityArchitecture #NGFW #UTM #ITSecurity #CyberDefense #Infosectrain
0 Comments
0 Shares
177 Views
0 Reviews