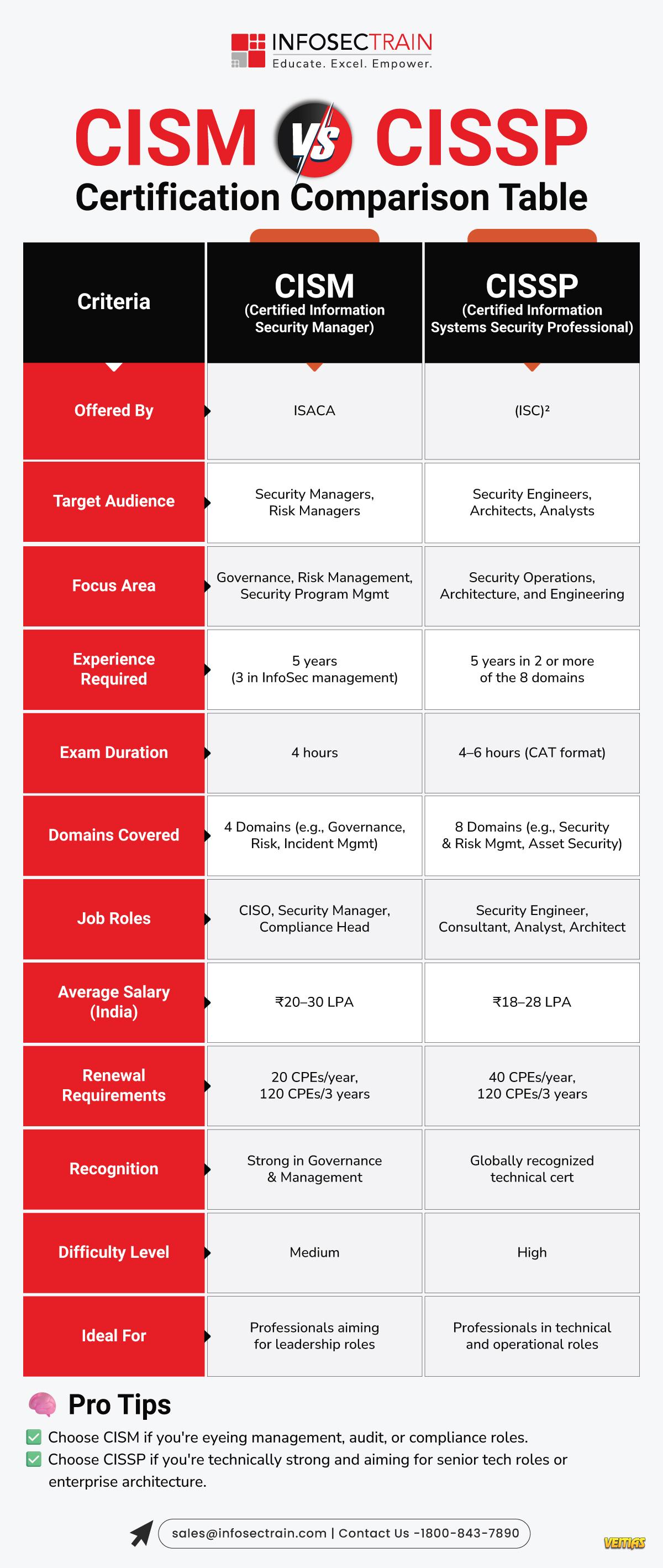
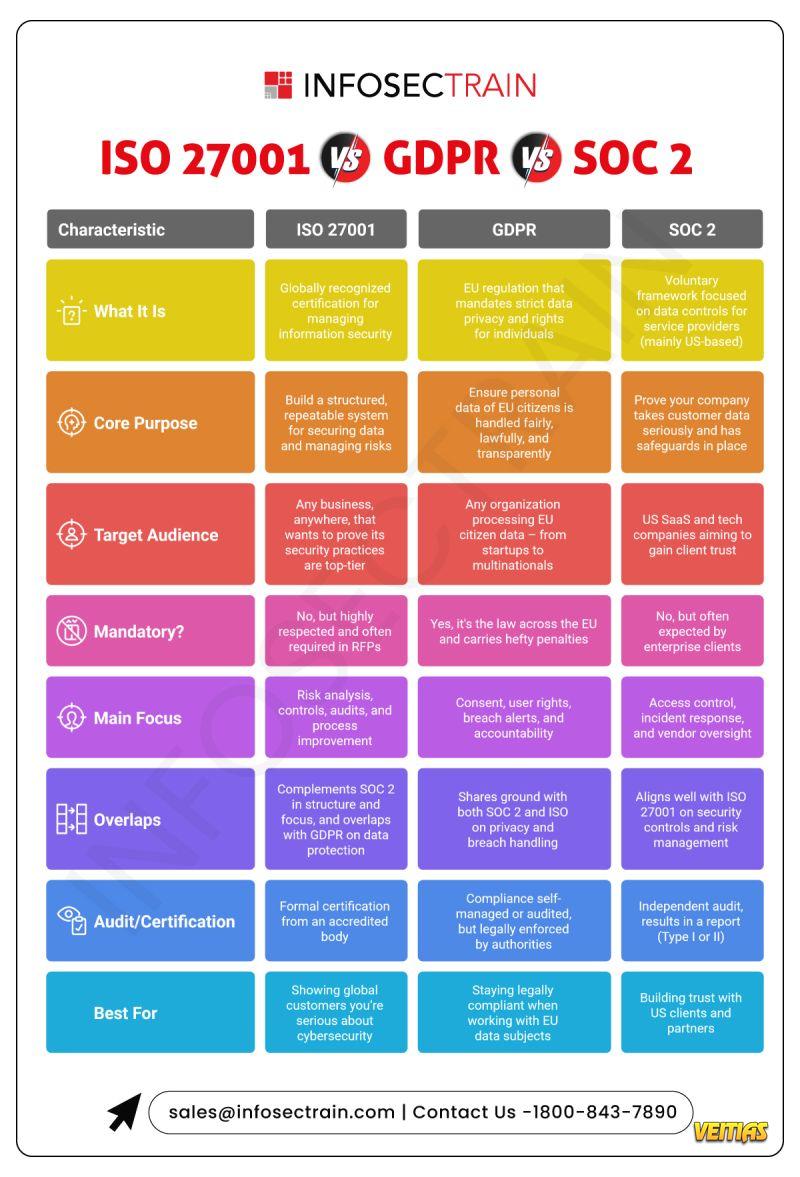
Stay Resilient in an Unpredictable World!
Today, in an era of increasing cyberattacks, supply chain interruptions, and compliance requirements, Business Continuity Know how is not optional, it’s essential.
InfosecTrain’s ISO 22301 Lead Implementer Course enables you with skills to manage and develop a robust Business Continuity Management System (BCMS) based on ISO 22301:2019 standards.
It’s risk management, disaster recovery, and business resiliency all wrapped into one training that provides the techniques your organization needs most right now.
Read more here: https://www.infosectrain.com/blog/why-choose-the-iso-22301-lead-implementer-course-with-infosectrain/
#ISO22301 #BusinessContinuity #OperationalResilience #RiskManagement #DisasterRecovery #InfosecTrain #BCMS #CybersecurityTraining #ContinuityPlanning
Today, in an era of increasing cyberattacks, supply chain interruptions, and compliance requirements, Business Continuity Know how is not optional, it’s essential.
InfosecTrain’s ISO 22301 Lead Implementer Course enables you with skills to manage and develop a robust Business Continuity Management System (BCMS) based on ISO 22301:2019 standards.
It’s risk management, disaster recovery, and business resiliency all wrapped into one training that provides the techniques your organization needs most right now.
Read more here: https://www.infosectrain.com/blog/why-choose-the-iso-22301-lead-implementer-course-with-infosectrain/
#ISO22301 #BusinessContinuity #OperationalResilience #RiskManagement #DisasterRecovery #InfosecTrain #BCMS #CybersecurityTraining #ContinuityPlanning
Stay Resilient in an Unpredictable World!
Today, in an era of increasing cyberattacks, supply chain interruptions, and compliance requirements, Business Continuity Know how is not optional, it’s essential.
InfosecTrain’s ISO 22301 Lead Implementer Course enables you with skills to manage and develop a robust Business Continuity Management System (BCMS) based on ISO 22301:2019 standards.
It’s risk management, disaster recovery, and business resiliency all wrapped into one training that provides the techniques your organization needs most right now.
Read more here: https://www.infosectrain.com/blog/why-choose-the-iso-22301-lead-implementer-course-with-infosectrain/
#ISO22301 #BusinessContinuity #OperationalResilience #RiskManagement #DisasterRecovery #InfosecTrain #BCMS #CybersecurityTraining #ContinuityPlanning
0 Commentaires
0 Parts
1159 Vue
0 Aperçu