𝐇𝐨𝐰 𝐈𝐧𝐟𝐨𝐬𝐞𝐜 𝐓𝐫𝐚𝐢𝐧 𝐀𝐝𝐯𝐚𝐧𝐜𝐞𝐝 𝐓𝐡𝐫𝐞𝐚𝐭 𝐇𝐮𝐧𝐭𝐢𝐧𝐠 𝐚𝐧𝐝 𝐃𝐅𝐈𝐑 𝐜𝐨𝐮𝐫𝐬𝐞 𝐢𝐬 𝐃𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐭 𝐟𝐫𝐨𝐦 𝐎𝐭𝐡𝐞𝐫𝐬?
Cyber attacks are advancing at an unprecedented rate and so is reactive security’s irrelevance.
Today’s defenders need the ability to hunt threats, find unknown attacker activity, and respond with certainty.
𝐓𝐡𝐚𝐭’𝐬 𝐰𝐡𝐞𝐫𝐞 𝐈𝐧𝐟𝐨𝐒𝐞𝐜𝐓𝐫𝐚𝐢𝐧’𝐬 𝐀𝐝𝐯𝐚𝐧𝐜𝐞𝐝 𝐓𝐡𝐫𝐞𝐚𝐭 𝐇𝐮𝐧𝐭𝐢𝐧𝐠 & 𝐃𝐅𝐈𝐑 𝐏𝐫𝐨𝐠𝐫𝐚𝐦 𝐬𝐭𝐚𝐧𝐝𝐬 𝐨𝐮𝐭.
𝟐𝟓+ 𝐇𝐚𝐧𝐝𝐬-𝐎𝐧 𝐋𝐚𝐛𝐬
Complete real-world attack simulations including malware analysis, memory forensics, network decoding and adversary tracking.
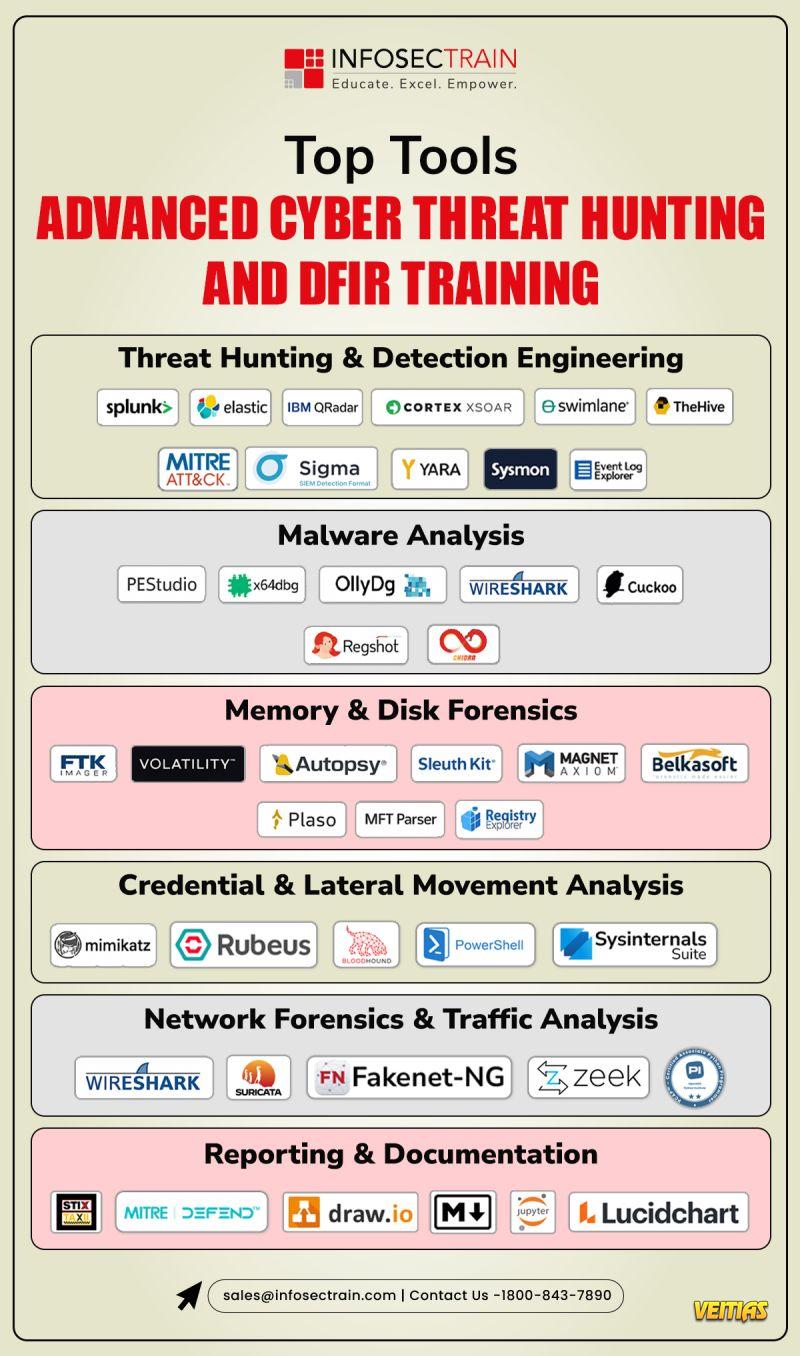
𝐌𝐚𝐬𝐭𝐞𝐫 𝐈𝐧𝐝𝐮𝐬𝐭𝐫𝐲-𝐒𝐭𝐚𝐧𝐝𝐚𝐫𝐝 𝐓𝐨𝐨𝐥𝐬
Volatility | Wireshark | YARA | MITRE ATT&CK | Log Forensics & Threat Intel Tool
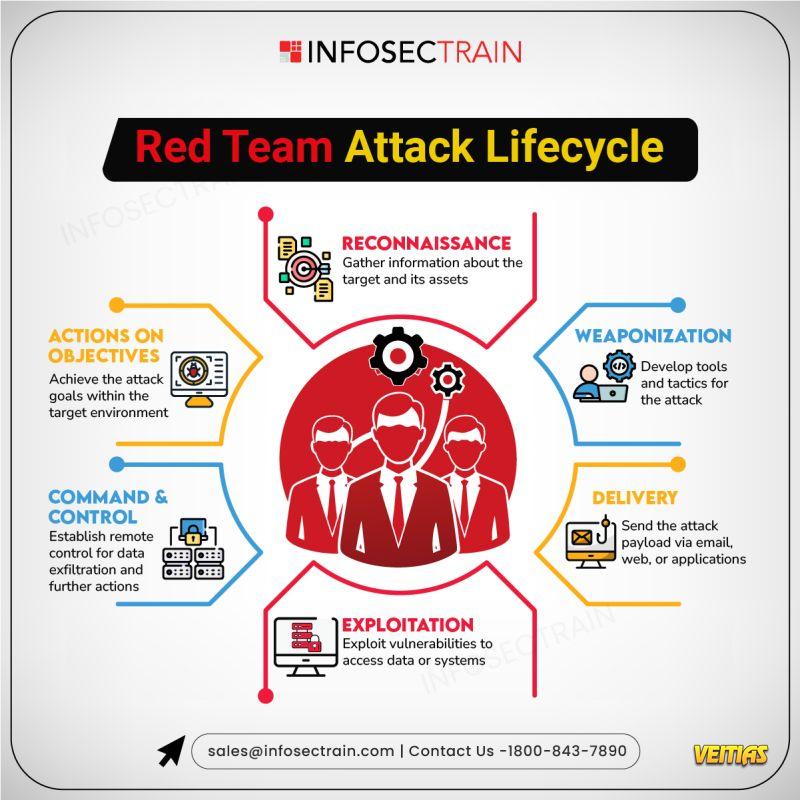
𝐈𝐧𝐭𝐞𝐠𝐫𝐚𝐭𝐞𝐝 𝐓𝐡𝐫𝐞𝐚𝐭 𝐇𝐮𝐧𝐭𝐢𝐧𝐠 + 𝐅𝐨𝐫𝐞𝐧𝐬𝐢𝐜𝐬 + 𝐈𝐑 𝐖𝐨𝐫𝐤𝐟𝐥𝐨𝐰
Watch how real DFIR teams investigate, respond, and contain threats (live-to-tape).
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/how-infosectrains-advanced-threat-hunting-and-dfir-course-is-different-from-others/
#CyberSecurity #InfoSec #CyberDefense #BlueTeam #ThreatHunting #DFIR #IncidentResponse #MalwareAnalysis #DigitalForensics
Cyber attacks are advancing at an unprecedented rate and so is reactive security’s irrelevance.
Today’s defenders need the ability to hunt threats, find unknown attacker activity, and respond with certainty.
𝐓𝐡𝐚𝐭’𝐬 𝐰𝐡𝐞𝐫𝐞 𝐈𝐧𝐟𝐨𝐒𝐞𝐜𝐓𝐫𝐚𝐢𝐧’𝐬 𝐀𝐝𝐯𝐚𝐧𝐜𝐞𝐝 𝐓𝐡𝐫𝐞𝐚𝐭 𝐇𝐮𝐧𝐭𝐢𝐧𝐠 & 𝐃𝐅𝐈𝐑 𝐏𝐫𝐨𝐠𝐫𝐚𝐦 𝐬𝐭𝐚𝐧𝐝𝐬 𝐨𝐮𝐭.
𝟐𝟓+ 𝐇𝐚𝐧𝐝𝐬-𝐎𝐧 𝐋𝐚𝐛𝐬
Complete real-world attack simulations including malware analysis, memory forensics, network decoding and adversary tracking.
𝐌𝐚𝐬𝐭𝐞𝐫 𝐈𝐧𝐝𝐮𝐬𝐭𝐫𝐲-𝐒𝐭𝐚𝐧𝐝𝐚𝐫𝐝 𝐓𝐨𝐨𝐥𝐬
Volatility | Wireshark | YARA | MITRE ATT&CK | Log Forensics & Threat Intel Tool
𝐈𝐧𝐭𝐞𝐠𝐫𝐚𝐭𝐞𝐝 𝐓𝐡𝐫𝐞𝐚𝐭 𝐇𝐮𝐧𝐭𝐢𝐧𝐠 + 𝐅𝐨𝐫𝐞𝐧𝐬𝐢𝐜𝐬 + 𝐈𝐑 𝐖𝐨𝐫𝐤𝐟𝐥𝐨𝐰
Watch how real DFIR teams investigate, respond, and contain threats (live-to-tape).
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/how-infosectrains-advanced-threat-hunting-and-dfir-course-is-different-from-others/
#CyberSecurity #InfoSec #CyberDefense #BlueTeam #ThreatHunting #DFIR #IncidentResponse #MalwareAnalysis #DigitalForensics
𝐇𝐨𝐰 𝐈𝐧𝐟𝐨𝐬𝐞𝐜 𝐓𝐫𝐚𝐢𝐧 𝐀𝐝𝐯𝐚𝐧𝐜𝐞𝐝 𝐓𝐡𝐫𝐞𝐚𝐭 𝐇𝐮𝐧𝐭𝐢𝐧𝐠 𝐚𝐧𝐝 𝐃𝐅𝐈𝐑 𝐜𝐨𝐮𝐫𝐬𝐞 𝐢𝐬 𝐃𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐭 𝐟𝐫𝐨𝐦 𝐎𝐭𝐡𝐞𝐫𝐬?
Cyber attacks are advancing at an unprecedented rate and so is reactive security’s irrelevance.
Today’s defenders need the ability to hunt threats, find unknown attacker activity, and respond with certainty.
𝐓𝐡𝐚𝐭’𝐬 𝐰𝐡𝐞𝐫𝐞 𝐈𝐧𝐟𝐨𝐒𝐞𝐜𝐓𝐫𝐚𝐢𝐧’𝐬 𝐀𝐝𝐯𝐚𝐧𝐜𝐞𝐝 𝐓𝐡𝐫𝐞𝐚𝐭 𝐇𝐮𝐧𝐭𝐢𝐧𝐠 & 𝐃𝐅𝐈𝐑 𝐏𝐫𝐨𝐠𝐫𝐚𝐦 𝐬𝐭𝐚𝐧𝐝𝐬 𝐨𝐮𝐭.
✅ 𝟐𝟓+ 𝐇𝐚𝐧𝐝𝐬-𝐎𝐧 𝐋𝐚𝐛𝐬
Complete real-world attack simulations including malware analysis, memory forensics, network decoding and adversary tracking.
✅𝐌𝐚𝐬𝐭𝐞𝐫 𝐈𝐧𝐝𝐮𝐬𝐭𝐫𝐲-𝐒𝐭𝐚𝐧𝐝𝐚𝐫𝐝 𝐓𝐨𝐨𝐥𝐬
Volatility | Wireshark | YARA | MITRE ATT&CK | Log Forensics & Threat Intel Tool
✅𝐈𝐧𝐭𝐞𝐠𝐫𝐚𝐭𝐞𝐝 𝐓𝐡𝐫𝐞𝐚𝐭 𝐇𝐮𝐧𝐭𝐢𝐧𝐠 + 𝐅𝐨𝐫𝐞𝐧𝐬𝐢𝐜𝐬 + 𝐈𝐑 𝐖𝐨𝐫𝐤𝐟𝐥𝐨𝐰
Watch how real DFIR teams investigate, respond, and contain threats (live-to-tape).
👉 𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐝𝐞𝐭𝐚𝐢𝐥𝐞𝐝 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/how-infosectrains-advanced-threat-hunting-and-dfir-course-is-different-from-others/
#CyberSecurity #InfoSec #CyberDefense #BlueTeam #ThreatHunting #DFIR #IncidentResponse #MalwareAnalysis #DigitalForensics
0 Comentários
0 Compartilhamentos
2807 Visualizações
0 Anterior