Cybersecurity Research Analyst
- 1066 Berichten
- 207 foto's
- 1 Video’s
- Female
- 21/10/1997
- Gevolgd door 1 people
© 2025 Veitias Social Network Club  Dutch
Dutch
Actueel
- Free Masterclass on Mastering CIPP/E in 30 Days: A Strategic Guide to SuccessRead more
Date: 9 Jan (Thu)
Time: 08:30 – 09:30 PM (IST)
Speaker: Jai
Free Register Now: https://www.infosectrain.com/events/mastering-cipp-e-in-30-days-a-strategic-guide-to-success/
Agenda for the Masterclass
Introduction to CIPP/E Certification
Important Topics to Master in CIPP/E
The 30-Day Study Plan
Exam Strategies and Tips for Success
Opportunities in the Data Privacy Domain
Interactive Q&A Session
Why Attend This Masterclass
Get CPE Certificate
Learn from Industry Experts
FREE Career Guidance & Mentorship
#FreeMasterclass #LearnCIPPE #DataPrivacyTraining #PrivacyCertification #PrivacyProfessionals #GDPRExperts #CIPPETraining #infosectrain #learntoriseFree Masterclass on Mastering CIPP/E in 30 Days: A Strategic Guide to Success 📅 Date: 9 Jan (Thu) ⌚ Time: 08:30 – 09:30 PM (IST) Speaker: Jai Free Register Now: https://www.infosectrain.com/events/mastering-cipp-e-in-30-days-a-strategic-guide-to-success/ ➡️ Agenda for the Masterclass 👉 Introduction to CIPP/E Certification 👉 Important Topics to Master in CIPP/E 👉 The 30-Day Study Plan 👉 Exam Strategies and Tips for Success 👉 Opportunities in the Data Privacy Domain 👉 Interactive Q&A Session ➡️ Why Attend This Masterclass 👉 Get CPE Certificate 👉 Learn from Industry Experts 👉 FREE Career Guidance & Mentorship #FreeMasterclass #LearnCIPPE #DataPrivacyTraining #PrivacyCertification #PrivacyProfessionals #GDPRExperts #CIPPETraining #infosectrain #learntoriseWWW.INFOSECTRAIN.COMMastering CIPP/E in 30 Days: A Strategic Guide to SuccessInfosecTrain offer free masterclass "Mastering CIPP/E in 30 Days: A Strategic Guide to Success" with Jai0 Reacties 0 aandelen 867 Views 0 voorbeeldPlease log in to like, share and comment! - Chief Enterprise Risk Officer Interview QuestionsRead more
As organizations face an increasingly complex risk landscape, the CERO plays a critical role in identifying, assessing, and mitigating risks that could impact the organization’s strategic objectives. Gain insights into the essential duties of a Chief Enterprise Risk Officer, including developing risk management strategies, ensuring regulatory compliance.
Read Here: https://www.infosectrain.com/blog/chief-enterprise-risk-officer-interview-questions/
#RiskManagement #InterviewPreparation #InfosecTrain #Cybersecurity #CareerDevelopmentChief Enterprise Risk Officer Interview Questions As organizations face an increasingly complex risk landscape, the CERO plays a critical role in identifying, assessing, and mitigating risks that could impact the organization’s strategic objectives. Gain insights into the essential duties of a Chief Enterprise Risk Officer, including developing risk management strategies, ensuring regulatory compliance. Read Here: https://www.infosectrain.com/blog/chief-enterprise-risk-officer-interview-questions/ #RiskManagement #InterviewPreparation #InfosecTrain #Cybersecurity #CareerDevelopmentWWW.INFOSECTRAIN.COMChief Enterprise Risk Officer Interview QuestionsGetting ready for these interviews means not just knowing risk management but also understanding the bigger picture. Let’s dive into the important questions that can help candidates shine in a CERO interview.0 Reacties 0 aandelen 1583 Views 0 voorbeeld - What Is Chain of Custody?Read more
Read Here: https://infosec-train.blogspot.com/2024/12/what-is-chain-of-custody.html
#ChainOfCustody #DigitalForensics #CyberSecurity #EvidenceHandling #IncidentResponse #ForensicAnalysis #InfoSec #DataIntegrity #LegalCompliance #CyberDefense #infosectrainWhat Is Chain of Custody? Read Here: https://infosec-train.blogspot.com/2024/12/what-is-chain-of-custody.html #ChainOfCustody #DigitalForensics #CyberSecurity #EvidenceHandling #IncidentResponse #ForensicAnalysis #InfoSec #DataIntegrity #LegalCompliance #CyberDefense #infosectrainINFOSEC-TRAIN.BLOGSPOT.COMWhat Is Chain of Custody?In cloud security, the chain of custody refers to the sequential record-keeping or documentation that tracks the handling, transfer, access,...0 Reacties 0 aandelen 2330 Views 0 voorbeeld - Proven Strategies for Success in Your CISSP JourneyRead more
Watch Here: https://www.youtube.com/watch?v=C8iE90C7xcg
#CISSPJourney #CISSPStrategies #CybersecurityCertification #StudyCISSP #CISSPPreparation #CISSPSuccess #InfosecTraining #StayMotivatedCISSP #CISSPFocusTips #infosectrainProven Strategies for Success in Your CISSP Journey Watch Here: https://www.youtube.com/watch?v=C8iE90C7xcg #CISSPJourney #CISSPStrategies #CybersecurityCertification #StudyCISSP #CISSPPreparation #CISSPSuccess #InfosecTraining #StayMotivatedCISSP #CISSPFocusTips #infosectrain 0 Reacties 0 aandelen 2092 Views 0 voorbeeld
0 Reacties 0 aandelen 2092 Views 0 voorbeeld - CEH Module 6- System HackingRead more
This module is essential for understanding how to identify, exploit, and mitigate vulnerabilities within systems, equipping cybersecurity professionals with the skills needed to defend against malicious attacks.
Read Here: https://www.infosectrain.com/blog/ceh-module-6-system-hacking/
#CEH #SystemHacking #EthicalHacking #InfosecTrain #Cybersecurity #MetasploitCEH Module 6- System Hacking This module is essential for understanding how to identify, exploit, and mitigate vulnerabilities within systems, equipping cybersecurity professionals with the skills needed to defend against malicious attacks. Read Here: https://www.infosectrain.com/blog/ceh-module-6-system-hacking/ #CEH #SystemHacking #EthicalHacking #InfosecTrain #Cybersecurity #MetasploitWWW.INFOSECTRAIN.COMCEH Module 6- System HackingThroughout this blog post, we'll embark on a deep dive into CEH Module 6, drawing on the latest practices and tools in the field.0 Reacties 0 aandelen 1561 Views 0 voorbeeld - Join InfosecTrain Free Webinar!Read more
Mastering Cloud Security: A Deep Dive into CCSK V.5
Are you ready to take your cloud security skills to the next level? This webinar is your gateway to mastering cloud security concepts and acing the Certificate of Cloud Security Knowledge (CCSK) V.5.
What You Will Learn:
1⃣ Demystifying Cloud Security: A Comprehensive Overview
2⃣ Navigating the CCSK V.5 Exam Blueprint
3⃣ Effective Exam Preparation Strategies
4⃣ Study Plan, Materials and Practical tips
5⃣ Sample Questions Practice
6⃣ Q&A Session: Your Questions, Answered
Register Now: https://www.infosectrain.com/events/mastering-cloud-security-a-deep-dive-into-ccsk-v-5/
#FreeWebinar #CloudSecurity #CCSKTraining #InfoSecTrain #CyberSecurity #CCSKV5 #CyberSecSkills🚀 Join InfosecTrain Free Webinar! 🚀 🔒 Mastering Cloud Security: A Deep Dive into CCSK V.5 🔒 Are you ready to take your cloud security skills to the next level? This webinar is your gateway to mastering cloud security concepts and acing the Certificate of Cloud Security Knowledge (CCSK) V.5. ✅ What You Will Learn: 1⃣ Demystifying Cloud Security: A Comprehensive Overview 2⃣ Navigating the CCSK V.5 Exam Blueprint 3⃣ Effective Exam Preparation Strategies 4⃣ Study Plan, Materials and Practical tips 5⃣ Sample Questions Practice 6⃣ Q&A Session: Your Questions, Answered 🔗 Register Now: https://www.infosectrain.com/events/mastering-cloud-security-a-deep-dive-into-ccsk-v-5/ #FreeWebinar #CloudSecurity #CCSKTraining #InfoSecTrain #CyberSecurity #CCSKV5 #CyberSecSkillsWWW.INFOSECTRAIN.COMMastering Cloud Security: A Deep Dive into CCSK V.5InfosecTrain offer free masterclass "Mastering Cloud Security: A Deep Dive into CCSK V.5" with Krish0 Reacties 0 aandelen 869 Views 0 voorbeeld - The Best CISSP Study Materials: Learning Guide for 2025Read more
Watch Here: https://www.youtube.com/watch?v=g1LPvVWTfCQ&t=1s
Thank you for watching this video! For more details or to get a free demo with our expert, just give us a heads up at sales@infosectrain.com
#CISSPStudyGuide #CybersecurityCertification #CISSPExamTips #CISSPPreparation #InfosecTraining #CISSPResources #CISSPMaterials #CybersecurityCareers #StudyCISSP #infosectrainThe Best CISSP Study Materials: Learning Guide for 2025 Watch Here: https://www.youtube.com/watch?v=g1LPvVWTfCQ&t=1s Thank you for watching this video! For more details or to get a free demo with our expert, just give us a heads up at sales@infosectrain.com #CISSPStudyGuide #CybersecurityCertification #CISSPExamTips #CISSPPreparation #InfosecTraining #CISSPResources #CISSPMaterials #CybersecurityCareers #StudyCISSP #infosectrain 0 Reacties 0 aandelen 853 Views 0 voorbeeld
0 Reacties 0 aandelen 853 Views 0 voorbeeld - What is Zero Trust Architecture?Read more
Read Here: https://medium.com/@Infosec-Train/what-is-zero-trust-architecture-6cd772464856
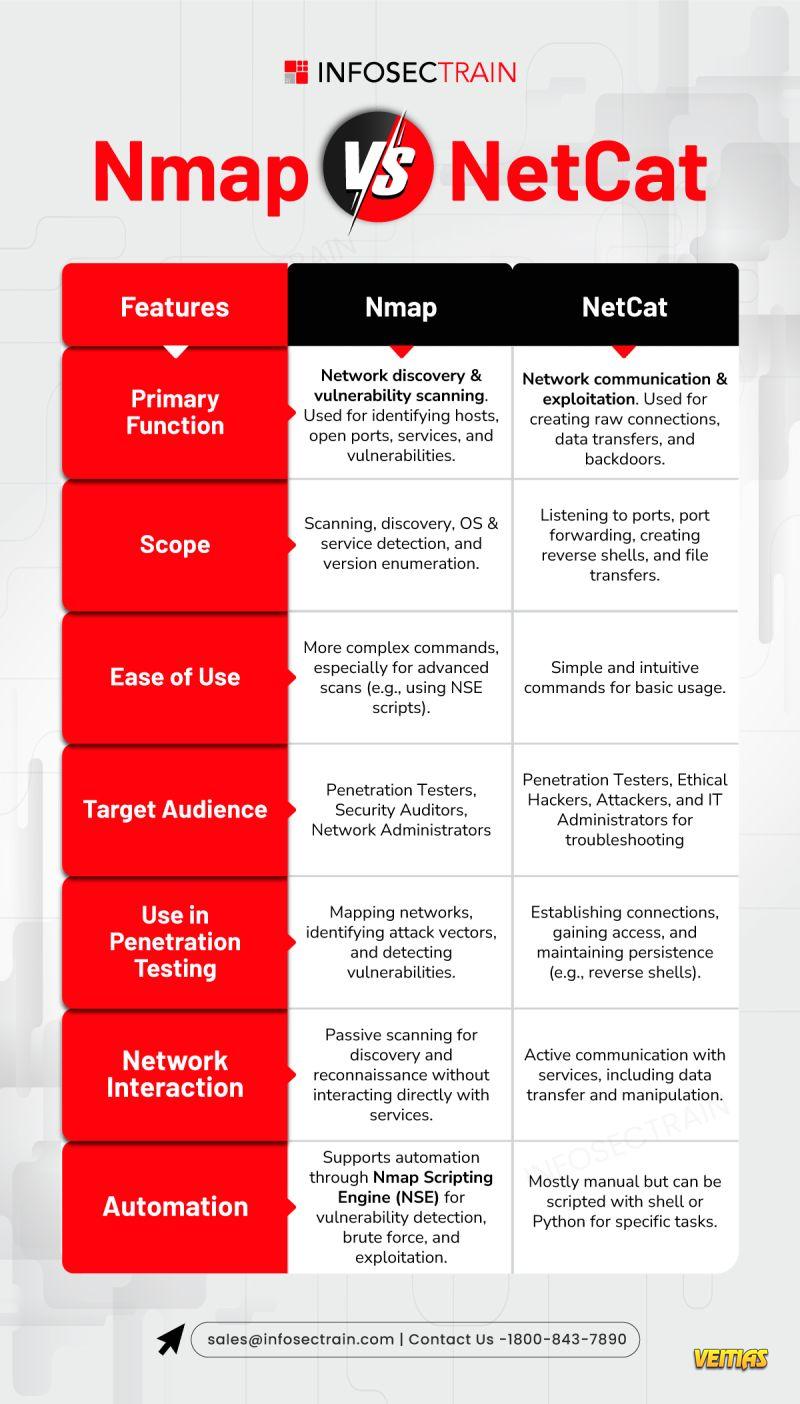
#ZeroTrustArchitecture #CyberSecurity #ZeroTrust #NetworkSecurity #InfoSec #ITSecurity #CyberDefense #SecurityArchitecture #AccessControl #DataProtection #CyberResilience #IdentityManagement #CloudSecurity #infosectrainWhat is Zero Trust Architecture? Read Here: https://medium.com/@Infosec-Train/what-is-zero-trust-architecture-6cd772464856 #ZeroTrustArchitecture #CyberSecurity #ZeroTrust #NetworkSecurity #InfoSec #ITSecurity #CyberDefense #SecurityArchitecture #AccessControl #DataProtection #CyberResilience #IdentityManagement #CloudSecurity #infosectrainMEDIUM.COMWhat is Zero Trust Architecture?Zero Trust Architecture (ZTA) is a modern cybersecurity model designed to address the increasing complexity of IT systems and the evolving…0 Reacties 0 aandelen 553 Views 0 voorbeeld - Nmap Vs NetCatRead more
Nmap and NetCat – two essential tools in the cybersecurity toolkit, but which one reigns supreme for your next penetration test or network audit? Let's break it down with this quick infographic comparison
Nmap 🕵♂
Primary Function: Network discovery & vulnerability scanning.
Scope: Identifying hosts, open ports, OS & service detection, version enumeration.
Target Audience: Pen Testers, Security Auditors, Admins.
Automation: Fully supports NSE scripts for automation.
Use: Discover vulnerabilities and attack vectors during network mapping.
Network Interaction: Passive, only scans without engaging services directly.
NetCat
Primary Function: Network communication & exploitation.
Scope: Port listening, creating reverse shells, file transfers, and port forwarding.
Target Audience: Pen Testers, Ethical Hackers, IT Admins.
Automation: Scriptable with shell/Python but manual by design.
Use: Establishing connections, gaining access, maintaining persistence.
Network Interaction: Active – directly communicates and manipulates services.
Key Takeaway:
Nmap is your go-to for 𝐬𝐜𝐚𝐧𝐧𝐢𝐧𝐠 𝐚𝐧𝐝 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐲 𝐝𝐢𝐬𝐜𝐨𝐯𝐞𝐫𝐲 . Perfect for mapping out a network’s attack surface.
NetCat is a 𝐧𝐞𝐭𝐰𝐨𝐫𝐤 𝐮𝐭𝐢𝐥𝐢𝐭𝐲 that's all about 𝐜𝐨𝐦𝐦𝐮𝐧𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐚𝐧𝐝 𝐞𝐱𝐩𝐥𝐨𝐢𝐭𝐚𝐭𝐢𝐨𝐧. If you need to 𝐜𝐫𝐞𝐚𝐭𝐞 𝐛𝐚𝐜𝐤𝐝𝐨𝐨𝐫𝐬 or transfer data, this is the tool for you.
Whether you’re #mappingnetworks or #exploitingvulnerabilities , knowing when to use each tool is key to mastering cybersecurity.
#Nmap #NetCat #CyberSecurity #EthicalHacking #NetworkScanning #PenTesting #InfoSecTools #CyberDefense #NetworkSecurity #HackingTools #RedTeaming #OffensiveSecurity #PortScanning #NetworkMonitoring #ITSecurity #SecurityTools #infosectrainNmap Vs NetCat Nmap and 🔗 NetCat – two essential tools in the cybersecurity toolkit, but which one reigns supreme for your next penetration test or network audit? Let's break it down with this quick infographic comparison Nmap 🕵♂ ➡️ Primary Function: Network discovery & vulnerability scanning. ➡️ Scope: Identifying hosts, open ports, OS & service detection, version enumeration. ➡️ Target Audience: Pen Testers, Security Auditors, Admins. ➡️ Automation: Fully supports NSE scripts for automation. ➡️ Use: Discover vulnerabilities and attack vectors during network mapping. ➡️ Network Interaction: Passive, only scans without engaging services directly. NetCat ⚡ ➡️ Primary Function: Network communication & exploitation. ➡️ Scope: Port listening, creating reverse shells, file transfers, and port forwarding. ➡️ Target Audience: Pen Testers, Ethical Hackers, IT Admins. ➡️ Automation: Scriptable with shell/Python but manual by design. ➡️ Use: Establishing connections, gaining access, maintaining persistence. ➡️ Network Interaction: Active – directly communicates and manipulates services. 🔑 Key Takeaway: Nmap is your go-to for 𝐬𝐜𝐚𝐧𝐧𝐢𝐧𝐠 𝐚𝐧𝐝 𝐯𝐮𝐥𝐧𝐞𝐫𝐚𝐛𝐢𝐥𝐢𝐭𝐲 𝐝𝐢𝐬𝐜𝐨𝐯𝐞𝐫𝐲 . Perfect for mapping out a network’s attack surface. NetCat is a 𝐧𝐞𝐭𝐰𝐨𝐫𝐤 𝐮𝐭𝐢𝐥𝐢𝐭𝐲 that's all about 𝐜𝐨𝐦𝐦𝐮𝐧𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐚𝐧𝐝 𝐞𝐱𝐩𝐥𝐨𝐢𝐭𝐚𝐭𝐢𝐨𝐧. If you need to 𝐜𝐫𝐞𝐚𝐭𝐞 𝐛𝐚𝐜𝐤𝐝𝐨𝐨𝐫𝐬 or transfer data, this is the tool for you. 🔐 Whether you’re #mappingnetworks or #exploitingvulnerabilities , knowing when to use each tool is key to mastering cybersecurity. 💻🔒 #Nmap #NetCat #CyberSecurity #EthicalHacking #NetworkScanning #PenTesting #InfoSecTools #CyberDefense #NetworkSecurity #HackingTools #RedTeaming #OffensiveSecurity #PortScanning #NetworkMonitoring #ITSecurity #SecurityTools #infosectrain0 Reacties 0 aandelen 828 Views 0 voorbeeld - Digital Forensics Analyst vs. Incident ResponderRead more
Have you ever wondered about the critical roles that Digital Forensics Analysts and Incident Responders play in cybersecurity? With cybercrime costs projected to reach $10.5 trillion annually by 2025, these professionals are at the forefront of protecting organizations from threats. Digital Forensics Analysts conduct post-incident analysis, while Incident Responders act in real-time to manage ongoing threats.
Read the full blog here: https://www.infosectrain.com/blog/digital-forensics-analyst-vs-incident-responder/
#DigitalForensics #IncidentResponder #CyberSecurity #ForensicsAnalysis #IncidentResponse #InfoSecCareers #CyberDefense #DataBreaches #DigitalEvidence #ThreatHunting #CyberSecurityProfessionals #infosectrainDigital Forensics Analyst vs. Incident Responder Have you ever wondered about the critical roles that Digital Forensics Analysts and Incident Responders play in cybersecurity? With cybercrime costs projected to reach $10.5 trillion annually by 2025, these professionals are at the forefront of protecting organizations from threats. Digital Forensics Analysts conduct post-incident analysis, while Incident Responders act in real-time to manage ongoing threats. 👉 Read the full blog here: https://www.infosectrain.com/blog/digital-forensics-analyst-vs-incident-responder/ #DigitalForensics #IncidentResponder #CyberSecurity #ForensicsAnalysis #IncidentResponse #InfoSecCareers #CyberDefense #DataBreaches #DigitalEvidence #ThreatHunting #CyberSecurityProfessionals #infosectrainWWW.INFOSECTRAIN.COMDigital Forensics Analyst vs. Incident ResponderHowever, their roles and responsibilities differ significantly. This article will unravel the distinct functions and importance of both these crucial roles.0 Reacties 0 aandelen 455 Views 0 voorbeeld
Meer blogs