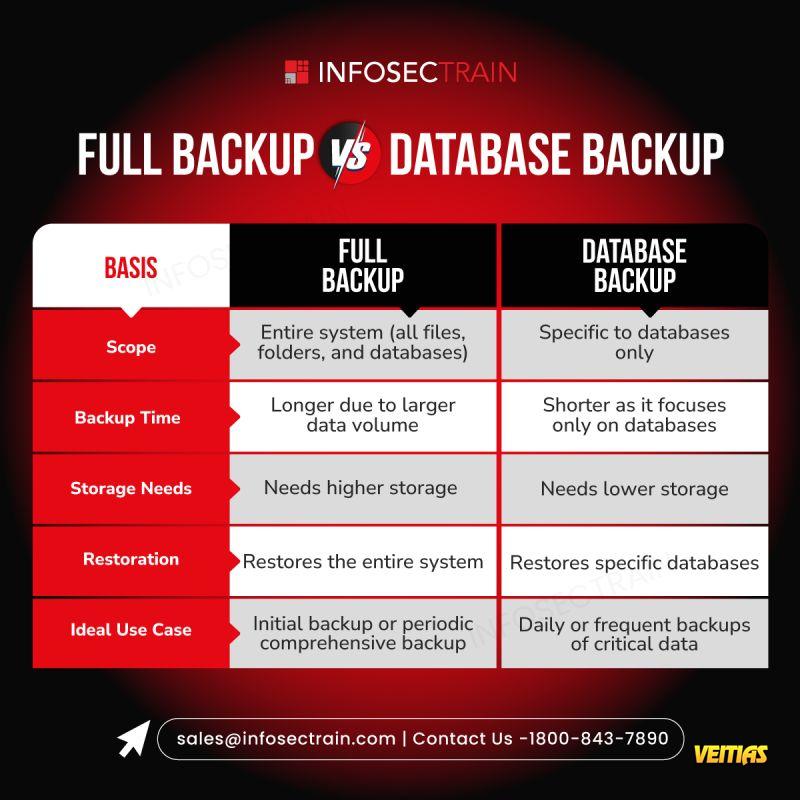
𝐅𝐮𝐥𝐥 𝐁𝐚𝐜𝐤𝐮𝐩 𝐯𝐬. 𝐃𝐚𝐭𝐚𝐛𝐚𝐬𝐞 𝐁𝐚𝐜𝐤𝐮𝐩: 𝐊𝐞𝐲 𝐃𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐜𝐞𝐬
When planning your backup strategy, it's crucial to understand the distinctions between a 𝐅𝐮𝐥𝐥 𝐁𝐚𝐜𝐤𝐮𝐩 and a 𝐃𝐚𝐭𝐚𝐛𝐚𝐬𝐞 𝐁𝐚𝐜𝐤𝐮𝐩.
Check out: https://www.infosectrain.com/blog/data-protection-vs-data-security/
#FullBackup #DatabaseBackup #DataBackup #BackupSolutions #DataProtection #ITInfrastructure #DataSecurity #BackupStrategy #StorageManagement #DisasterRecovery #InformationSecurity #TechExplained #DataManagement #BusinessContinuity #CyberSecurity #infosctrain
When planning your backup strategy, it's crucial to understand the distinctions between a 𝐅𝐮𝐥𝐥 𝐁𝐚𝐜𝐤𝐮𝐩 and a 𝐃𝐚𝐭𝐚𝐛𝐚𝐬𝐞 𝐁𝐚𝐜𝐤𝐮𝐩.
Check out: https://www.infosectrain.com/blog/data-protection-vs-data-security/
#FullBackup #DatabaseBackup #DataBackup #BackupSolutions #DataProtection #ITInfrastructure #DataSecurity #BackupStrategy #StorageManagement #DisasterRecovery #InformationSecurity #TechExplained #DataManagement #BusinessContinuity #CyberSecurity #infosctrain
𝐅𝐮𝐥𝐥 𝐁𝐚𝐜𝐤𝐮𝐩 𝐯𝐬. 𝐃𝐚𝐭𝐚𝐛𝐚𝐬𝐞 𝐁𝐚𝐜𝐤𝐮𝐩: 𝐊𝐞𝐲 𝐃𝐢𝐟𝐟𝐞𝐫𝐞𝐧𝐜𝐞𝐬
When planning your backup strategy, it's crucial to understand the distinctions between a 𝐅𝐮𝐥𝐥 𝐁𝐚𝐜𝐤𝐮𝐩 and a 𝐃𝐚𝐭𝐚𝐛𝐚𝐬𝐞 𝐁𝐚𝐜𝐤𝐮𝐩.
Check out: https://www.infosectrain.com/blog/data-protection-vs-data-security/
#FullBackup #DatabaseBackup #DataBackup #BackupSolutions #DataProtection #ITInfrastructure #DataSecurity #BackupStrategy #StorageManagement #DisasterRecovery #InformationSecurity #TechExplained #DataManagement #BusinessContinuity #CyberSecurity #infosctrain
0 Yorumlar
0 hisse senetleri
14028 Views
0 önizleme