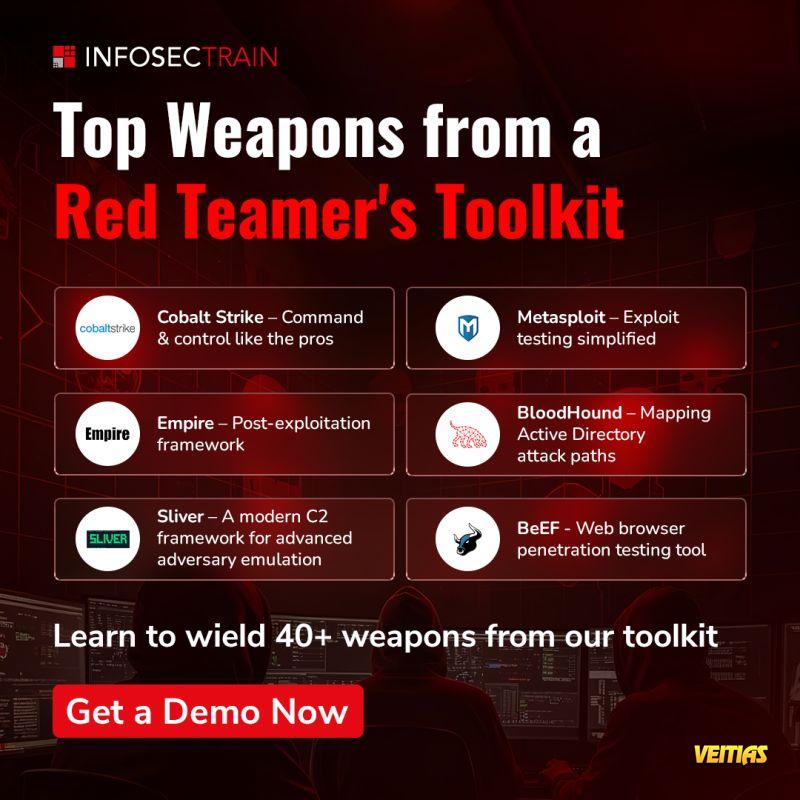
𝐓𝐨𝐩 𝐓𝐨𝐨𝐥𝐬 𝐂𝐨𝐯𝐞𝐫𝐞𝐝 𝐢𝐧 𝐑𝐞𝐝 𝐓𝐞𝐚𝐦 𝐎𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐟𝐫𝐨𝐦 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧
Discover how to conduct real-world attacks to identify unknown weaknesses and build stronger defenses from within. Take advantage of the full extent of the attack lifecycle, 𝐫𝐞𝐜𝐨𝐧𝐧𝐚𝐢𝐬𝐬𝐚𝐧𝐜𝐞 𝐭𝐡𝐫𝐨𝐮𝐠𝐡 𝐞𝐱𝐩𝐥𝐨𝐢𝐭𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐩𝐨𝐬𝐭-𝐞𝐱𝐩𝐥𝐨𝐢𝐭𝐚𝐭𝐢𝐨𝐧 𝐰𝐢𝐭𝐡 𝐭𝐨𝐨𝐥𝐬 𝐬𝐮𝐜𝐡 𝐚𝐬 𝐍𝐦𝐚𝐩, 𝐌𝐞𝐭𝐚𝐬𝐩𝐥𝐨𝐢𝐭, 𝐚𝐧𝐝 𝐂𝐨𝐛𝐚𝐥𝐭 𝐒𝐭𝐫𝐢𝐤𝐞.
Plus dive into next-gen tactics such as 𝐀𝐈-𝐝𝐫𝐢𝐯𝐞𝐧 𝐫𝐞𝐜𝐨𝐧𝐧𝐚𝐢𝐬𝐬𝐚𝐧𝐜𝐞 𝐚𝐧𝐝 𝐝𝐞𝐞𝐩𝐟𝐚𝐤𝐞-𝐛𝐚𝐬𝐞𝐝 𝐚𝐭𝐭𝐚𝐜𝐤𝐬.
𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/top-tools-covered-in-red-team-operation-training-from-infosectrain/
You are ready to go into the mind of the attacker with 𝐑𝐞𝐝 𝐓𝐞𝐚𝐦 𝐎𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐬 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐟𝐫𝐨𝐦 Infosec Train
#RedTeam #CyberSecurityTraining #EthicalHacking #PenTesting #InfoSec #RedTeamOperations #CyberAttackSimulation #HackingSkills #Nmap #InfosecTrain #CyberExperts #HackerMindset #SkillUp #TechTraining
Discover how to conduct real-world attacks to identify unknown weaknesses and build stronger defenses from within. Take advantage of the full extent of the attack lifecycle, 𝐫𝐞𝐜𝐨𝐧𝐧𝐚𝐢𝐬𝐬𝐚𝐧𝐜𝐞 𝐭𝐡𝐫𝐨𝐮𝐠𝐡 𝐞𝐱𝐩𝐥𝐨𝐢𝐭𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐩𝐨𝐬𝐭-𝐞𝐱𝐩𝐥𝐨𝐢𝐭𝐚𝐭𝐢𝐨𝐧 𝐰𝐢𝐭𝐡 𝐭𝐨𝐨𝐥𝐬 𝐬𝐮𝐜𝐡 𝐚𝐬 𝐍𝐦𝐚𝐩, 𝐌𝐞𝐭𝐚𝐬𝐩𝐥𝐨𝐢𝐭, 𝐚𝐧𝐝 𝐂𝐨𝐛𝐚𝐥𝐭 𝐒𝐭𝐫𝐢𝐤𝐞.
Plus dive into next-gen tactics such as 𝐀𝐈-𝐝𝐫𝐢𝐯𝐞𝐧 𝐫𝐞𝐜𝐨𝐧𝐧𝐚𝐢𝐬𝐬𝐚𝐧𝐜𝐞 𝐚𝐧𝐝 𝐝𝐞𝐞𝐩𝐟𝐚𝐤𝐞-𝐛𝐚𝐬𝐞𝐝 𝐚𝐭𝐭𝐚𝐜𝐤𝐬.
𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/top-tools-covered-in-red-team-operation-training-from-infosectrain/
You are ready to go into the mind of the attacker with 𝐑𝐞𝐝 𝐓𝐞𝐚𝐦 𝐎𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐬 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐟𝐫𝐨𝐦 Infosec Train
#RedTeam #CyberSecurityTraining #EthicalHacking #PenTesting #InfoSec #RedTeamOperations #CyberAttackSimulation #HackingSkills #Nmap #InfosecTrain #CyberExperts #HackerMindset #SkillUp #TechTraining
𝐓𝐨𝐩 𝐓𝐨𝐨𝐥𝐬 𝐂𝐨𝐯𝐞𝐫𝐞𝐝 𝐢𝐧 𝐑𝐞𝐝 𝐓𝐞𝐚𝐦 𝐎𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐟𝐫𝐨𝐦 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧
☑️ Discover how to conduct real-world attacks to identify unknown weaknesses and build stronger defenses from within. Take advantage of the full extent of the attack lifecycle, 𝐫𝐞𝐜𝐨𝐧𝐧𝐚𝐢𝐬𝐬𝐚𝐧𝐜𝐞 𝐭𝐡𝐫𝐨𝐮𝐠𝐡 𝐞𝐱𝐩𝐥𝐨𝐢𝐭𝐚𝐭𝐢𝐨𝐧 𝐚𝐧𝐝 𝐩𝐨𝐬𝐭-𝐞𝐱𝐩𝐥𝐨𝐢𝐭𝐚𝐭𝐢𝐨𝐧 𝐰𝐢𝐭𝐡 𝐭𝐨𝐨𝐥𝐬 𝐬𝐮𝐜𝐡 𝐚𝐬 𝐍𝐦𝐚𝐩, 𝐌𝐞𝐭𝐚𝐬𝐩𝐥𝐨𝐢𝐭, 𝐚𝐧𝐝 𝐂𝐨𝐛𝐚𝐥𝐭 𝐒𝐭𝐫𝐢𝐤𝐞.
☑️ Plus dive into next-gen tactics such as 𝐀𝐈-𝐝𝐫𝐢𝐯𝐞𝐧 𝐫𝐞𝐜𝐨𝐧𝐧𝐚𝐢𝐬𝐬𝐚𝐧𝐜𝐞 𝐚𝐧𝐝 𝐝𝐞𝐞𝐩𝐟𝐚𝐤𝐞-𝐛𝐚𝐬𝐞𝐝 𝐚𝐭𝐭𝐚𝐜𝐤𝐬.
👉 𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/top-tools-covered-in-red-team-operation-training-from-infosectrain/
☑️You are ready to go into the mind of the attacker with 𝐑𝐞𝐝 𝐓𝐞𝐚𝐦 𝐎𝐩𝐞𝐫𝐚𝐭𝐢𝐨𝐧𝐬 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐟𝐫𝐨𝐦 Infosec Train
#RedTeam #CyberSecurityTraining #EthicalHacking #PenTesting #InfoSec #RedTeamOperations #CyberAttackSimulation #HackingSkills #Nmap #InfosecTrain #CyberExperts #HackerMindset #SkillUp #TechTraining
0 Comments
0 Shares
186 Views
0 Reviews