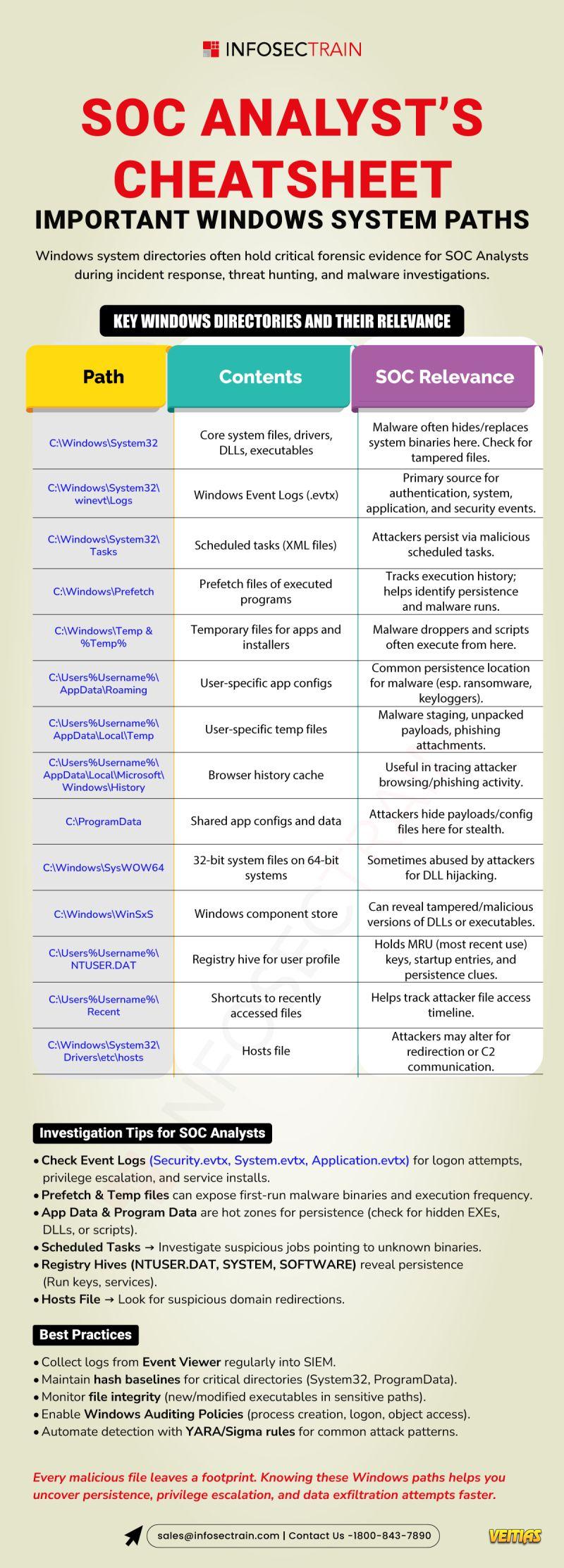
𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐄𝐯𝐞𝐧𝐭 𝐋𝐨𝐠𝐬: 𝐓𝐡𝐞 𝐁𝐚𝐜𝐤𝐛𝐨𝐧𝐞 𝐨𝐟 𝐂𝐲𝐛𝐞𝐫 𝐃𝐞𝐟𝐞𝐧𝐬𝐞
𝐕𝐢𝐬𝐢𝐛𝐢𝐥𝐢𝐭𝐲 is the first step in the cyber security process you need 𝐥𝐨𝐠𝐬 to see
The logs from security, directory services, DNS, applications, and systems are not merely documentsbut they are 𝐬𝐢𝐠𝐧𝐚𝐥𝐬 𝐨𝐟 𝐞𝐚𝐫𝐥𝐲 𝐰𝐚𝐫𝐧𝐢𝐧𝐠𝐬 that your security measures are (or aren’t) working.
Consider 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐄𝐯𝐞𝐧𝐭 𝐋𝐨𝐠𝐬 to be your 𝐈𝐓 𝐰𝐨𝐫𝐥𝐝’𝐬 𝐛𝐥𝐚𝐜𝐤 𝐛𝐨𝐱.
If an incident happens, logging is the only source that narrates the incidentno assumptions at all.
𝐋𝐨𝐠𝐬 𝐭𝐮𝐫𝐧 𝐞𝐯𝐞𝐫𝐲𝐝𝐚𝐲 𝐬𝐲𝐬𝐭𝐞𝐦 𝐚𝐜𝐭𝐢𝐯𝐢𝐭𝐲 𝐢𝐧𝐭𝐨 𝐚𝐜𝐭𝐢𝐨𝐧𝐚𝐛𝐥𝐞 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐢𝐧𝐭𝐞𝐥𝐥𝐢𝐠𝐞𝐧𝐜𝐞.
𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞 𝐓𝐨𝐩 𝟕 𝐋𝐨𝐠 𝐒𝐨𝐮𝐫𝐜𝐞𝐬 𝐄𝐯𝐞𝐫𝐲 𝐒𝐎𝐂 𝐀𝐧𝐚𝐥𝐲𝐬𝐭 𝐒𝐡𝐨𝐮𝐥𝐝 𝐊𝐧𝐨𝐰: https://www.infosectrain.com/blog/top-7-log-sources-every-soc-analyst-should-know
𝐈𝐧𝐟𝐨𝐠𝐫𝐚𝐩𝐡𝐢𝐜 𝐂𝐫𝐞𝐝𝐢𝐭: Infosec Train (Empowering professionals with practical cybersecurity knowledge & real-world insights)
#CyberSecurity #SecurityLogs #SIEM #ThreatDetection #BlueTeam #IncidentResponse #SecurityMonitoring #Infosec #SOC #InfoSecTrain
𝐕𝐢𝐬𝐢𝐛𝐢𝐥𝐢𝐭𝐲 is the first step in the cyber security process you need 𝐥𝐨𝐠𝐬 to see
The logs from security, directory services, DNS, applications, and systems are not merely documentsbut they are 𝐬𝐢𝐠𝐧𝐚𝐥𝐬 𝐨𝐟 𝐞𝐚𝐫𝐥𝐲 𝐰𝐚𝐫𝐧𝐢𝐧𝐠𝐬 that your security measures are (or aren’t) working.
Consider 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐄𝐯𝐞𝐧𝐭 𝐋𝐨𝐠𝐬 to be your 𝐈𝐓 𝐰𝐨𝐫𝐥𝐝’𝐬 𝐛𝐥𝐚𝐜𝐤 𝐛𝐨𝐱.
If an incident happens, logging is the only source that narrates the incidentno assumptions at all.
𝐋𝐨𝐠𝐬 𝐭𝐮𝐫𝐧 𝐞𝐯𝐞𝐫𝐲𝐝𝐚𝐲 𝐬𝐲𝐬𝐭𝐞𝐦 𝐚𝐜𝐭𝐢𝐯𝐢𝐭𝐲 𝐢𝐧𝐭𝐨 𝐚𝐜𝐭𝐢𝐨𝐧𝐚𝐛𝐥𝐞 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐢𝐧𝐭𝐞𝐥𝐥𝐢𝐠𝐞𝐧𝐜𝐞.
𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞 𝐓𝐨𝐩 𝟕 𝐋𝐨𝐠 𝐒𝐨𝐮𝐫𝐜𝐞𝐬 𝐄𝐯𝐞𝐫𝐲 𝐒𝐎𝐂 𝐀𝐧𝐚𝐥𝐲𝐬𝐭 𝐒𝐡𝐨𝐮𝐥𝐝 𝐊𝐧𝐨𝐰: https://www.infosectrain.com/blog/top-7-log-sources-every-soc-analyst-should-know
𝐈𝐧𝐟𝐨𝐠𝐫𝐚𝐩𝐡𝐢𝐜 𝐂𝐫𝐞𝐝𝐢𝐭: Infosec Train (Empowering professionals with practical cybersecurity knowledge & real-world insights)
#CyberSecurity #SecurityLogs #SIEM #ThreatDetection #BlueTeam #IncidentResponse #SecurityMonitoring #Infosec #SOC #InfoSecTrain
𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐄𝐯𝐞𝐧𝐭 𝐋𝐨𝐠𝐬: 𝐓𝐡𝐞 𝐁𝐚𝐜𝐤𝐛𝐨𝐧𝐞 𝐨𝐟 𝐂𝐲𝐛𝐞𝐫 𝐃𝐞𝐟𝐞𝐧𝐬𝐞
𝐕𝐢𝐬𝐢𝐛𝐢𝐥𝐢𝐭𝐲 is the first step in the cyber security process ➡️you need 𝐥𝐨𝐠𝐬 to see 👀🔐
✅The logs from security, directory services, DNS, applications, and systems are not merely documents➡️but they are 𝐬𝐢𝐠𝐧𝐚𝐥𝐬 𝐨𝐟 𝐞𝐚𝐫𝐥𝐲 𝐰𝐚𝐫𝐧𝐢𝐧𝐠𝐬 that your security measures are (or aren’t) working.
Consider 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐄𝐯𝐞𝐧𝐭 𝐋𝐨𝐠𝐬 to be your 𝐈𝐓 𝐰𝐨𝐫𝐥𝐝’𝐬 𝐛𝐥𝐚𝐜𝐤 𝐛𝐨𝐱.
✅ If an incident happens, logging is the only source that narrates the incident➡️no assumptions at all.
✅ 𝐋𝐨𝐠𝐬 𝐭𝐮𝐫𝐧 𝐞𝐯𝐞𝐫𝐲𝐝𝐚𝐲 𝐬𝐲𝐬𝐭𝐞𝐦 𝐚𝐜𝐭𝐢𝐯𝐢𝐭𝐲 𝐢𝐧𝐭𝐨 𝐚𝐜𝐭𝐢𝐨𝐧𝐚𝐛𝐥𝐞 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐢𝐧𝐭𝐞𝐥𝐥𝐢𝐠𝐞𝐧𝐜𝐞.
🔗 𝐑𝐞𝐚𝐝 𝐦𝐨𝐫𝐞 ➡️ 𝐓𝐨𝐩 𝟕 𝐋𝐨𝐠 𝐒𝐨𝐮𝐫𝐜𝐞𝐬 𝐄𝐯𝐞𝐫𝐲 𝐒𝐎𝐂 𝐀𝐧𝐚𝐥𝐲𝐬𝐭 𝐒𝐡𝐨𝐮𝐥𝐝 𝐊𝐧𝐨𝐰: https://www.infosectrain.com/blog/top-7-log-sources-every-soc-analyst-should-know
👉 𝐈𝐧𝐟𝐨𝐠𝐫𝐚𝐩𝐡𝐢𝐜 𝐂𝐫𝐞𝐝𝐢𝐭: Infosec Train (Empowering professionals with practical cybersecurity knowledge & real-world insights)
#CyberSecurity #SecurityLogs #SIEM #ThreatDetection #BlueTeam #IncidentResponse #SecurityMonitoring #Infosec #SOC #InfoSecTrain
0 Comments
0 Shares
2595 Views
0 Reviews