Crack Your Next Pentest Interview | Must-Know Questions & Real Answers
Here’s what you’ll learn in this session:
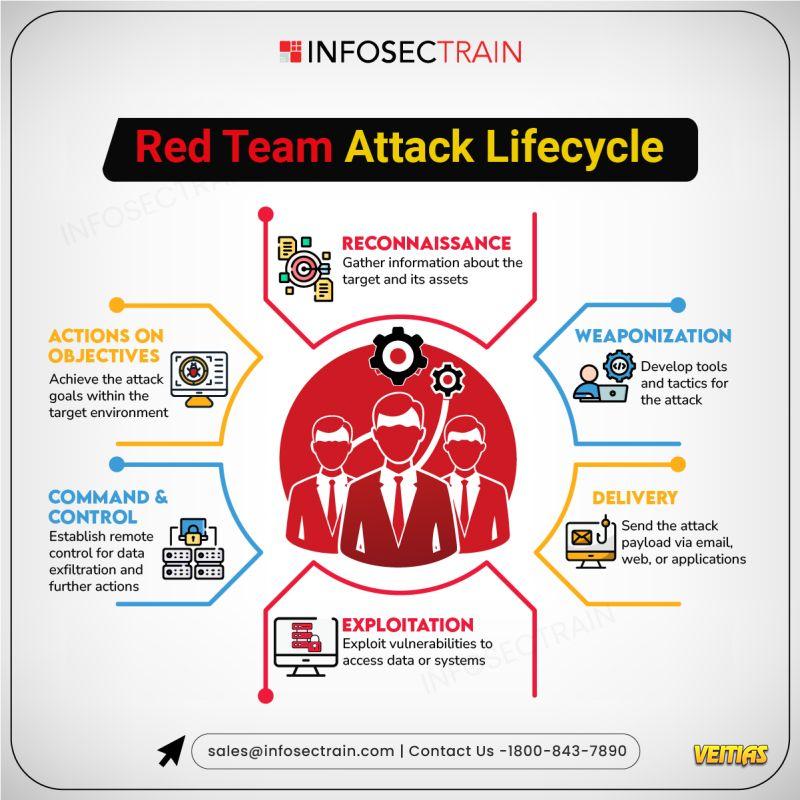
• Introduction
• Reconnaissance & Information Gathering
• Understanding the Penetration Testing Interview Process
• Exploitation & Privilege Escalation Techniques
Watch Here: https://youtu.be/ag7pam38yB8?si=YSaqvhU1TrhXa71b
#PenetrationTestingInterview #PentestQuestions2025 #RedTeamCareer #InfosecTrain #EthicalHackingJobs #EthicalHacker2025
Here’s what you’ll learn in this session:
• Introduction
• Reconnaissance & Information Gathering
• Understanding the Penetration Testing Interview Process
• Exploitation & Privilege Escalation Techniques
Watch Here: https://youtu.be/ag7pam38yB8?si=YSaqvhU1TrhXa71b
#PenetrationTestingInterview #PentestQuestions2025 #RedTeamCareer #InfosecTrain #EthicalHackingJobs #EthicalHacker2025
Crack Your Next Pentest Interview | Must-Know Questions & Real Answers
🔍 Here’s what you’ll learn in this session:
• Introduction
• Reconnaissance & Information Gathering
• Understanding the Penetration Testing Interview Process
• Exploitation & Privilege Escalation Techniques
Watch Here: https://youtu.be/ag7pam38yB8?si=YSaqvhU1TrhXa71b
#PenetrationTestingInterview #PentestQuestions2025 #RedTeamCareer #InfosecTrain #EthicalHackingJobs #EthicalHacker2025

0 Comentários
0 Compartilhamentos
2533 Visualizações
0 Anterior