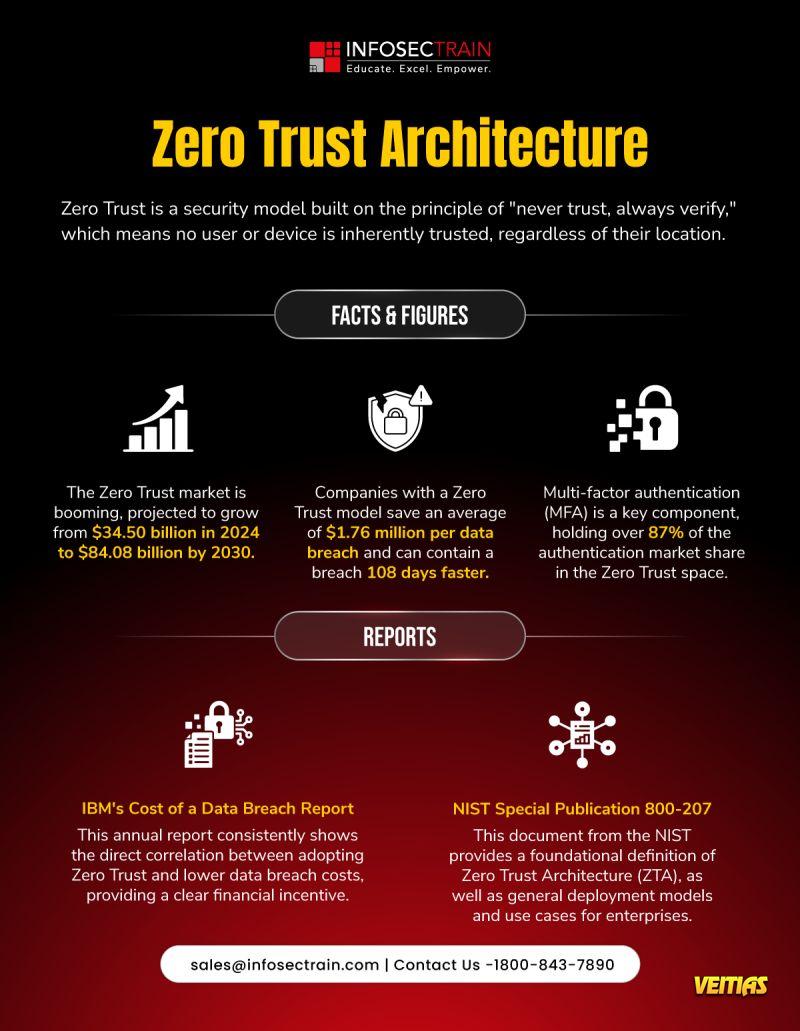
𝐈𝐒𝐂𝟐 𝐈𝐒𝐒𝐀𝐏 𝐃𝐨𝐦𝐚𝐢𝐧 𝟒.𝟒.𝟐: 𝐀𝐫𝐜𝐡𝐢𝐭𝐞𝐜𝐭 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐀𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧
Every time you sign in whether it’s to your email, bank account, social media, or work applications it seems straightforward at first glance. Just enter a username and password but that simplicity is misleading.
In reality, clicking that login button sets off a carefully designed 𝐢𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐬𝐲𝐬𝐭𝐞𝐦 working behind the scenesone that protects against attackers while still keeping the experience smooth and effortless for users.
𝐈𝐧 𝐈𝐒𝐂² 𝐈𝐒𝐒𝐀𝐏 𝐃𝐨𝐦𝐚𝐢𝐧, 𝐢𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐚𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 goes far beyond simply checking whether a user can log in. It focuses on how the login happens, where it’s coming from, and the level of risk involved at that moment, ensuring access is granted only when it truly makes sense from a security perspective.
𝐖𝐡𝐚𝐭 𝐌𝐨𝐝𝐞𝐫𝐧 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐀𝐫𝐜𝐡𝐢𝐭𝐞𝐜𝐭𝐮𝐫𝐞 𝐃𝐞𝐦𝐚𝐧𝐝𝐬:
Takeaway #1: Implementing 𝐌𝐮𝐥𝐭𝐢-𝐅𝐚𝐜𝐭𝐨𝐫 𝐀𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 (𝐌𝐅𝐀) as a strong primary defense.
Takeaway #2: Utilizing 𝐑𝐢𝐬𝐤-𝐁𝐚𝐬𝐞𝐝 𝐨𝐫 𝐀𝐝𝐚𝐩𝐭𝐢𝐯𝐞 𝐀𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 to assess login context.
Takeaway #3: Leveraging 𝐅𝐞𝐝𝐞𝐫𝐚𝐭𝐞𝐝 𝐏𝐫𝐨𝐭𝐨𝐜𝐨𝐥𝐬 to grant access without exposing credentials.
Takeaway #4: Applying a 𝐠𝐫𝐚𝐧𝐮𝐥𝐚𝐫 𝐥𝐚𝐲𝐞𝐫 𝐨𝐟 𝐀𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐚𝐭𝐢𝐨𝐧 to ensure restricted access.
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐟𝐮𝐥𝐥 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/isc2-issap-domain-4-4-2-architect-identity-authentication
Mastering this domain helps you design systems that are 𝐬𝐞𝐜𝐮𝐫𝐞, 𝐬𝐜𝐚𝐥𝐚𝐛𝐥𝐞, 𝐚𝐧𝐝 𝐮𝐬𝐞𝐫-𝐜𝐞𝐧𝐭𝐫𝐢𝐜.
#ISC2 #ISSAP #IdentitySecurity #AuthenticationArchitecture #MFA #ZeroTrust #CyberSecurity #InfosecTrain #IAM #SecurityArchitecture
Every time you sign in whether it’s to your email, bank account, social media, or work applications it seems straightforward at first glance. Just enter a username and password but that simplicity is misleading.
In reality, clicking that login button sets off a carefully designed 𝐢𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐬𝐲𝐬𝐭𝐞𝐦 working behind the scenesone that protects against attackers while still keeping the experience smooth and effortless for users.
𝐈𝐧 𝐈𝐒𝐂² 𝐈𝐒𝐒𝐀𝐏 𝐃𝐨𝐦𝐚𝐢𝐧, 𝐢𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐚𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 goes far beyond simply checking whether a user can log in. It focuses on how the login happens, where it’s coming from, and the level of risk involved at that moment, ensuring access is granted only when it truly makes sense from a security perspective.
𝐖𝐡𝐚𝐭 𝐌𝐨𝐝𝐞𝐫𝐧 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐀𝐫𝐜𝐡𝐢𝐭𝐞𝐜𝐭𝐮𝐫𝐞 𝐃𝐞𝐦𝐚𝐧𝐝𝐬:
Takeaway #1: Implementing 𝐌𝐮𝐥𝐭𝐢-𝐅𝐚𝐜𝐭𝐨𝐫 𝐀𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 (𝐌𝐅𝐀) as a strong primary defense.
Takeaway #2: Utilizing 𝐑𝐢𝐬𝐤-𝐁𝐚𝐬𝐞𝐝 𝐨𝐫 𝐀𝐝𝐚𝐩𝐭𝐢𝐯𝐞 𝐀𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 to assess login context.
Takeaway #3: Leveraging 𝐅𝐞𝐝𝐞𝐫𝐚𝐭𝐞𝐝 𝐏𝐫𝐨𝐭𝐨𝐜𝐨𝐥𝐬 to grant access without exposing credentials.
Takeaway #4: Applying a 𝐠𝐫𝐚𝐧𝐮𝐥𝐚𝐫 𝐥𝐚𝐲𝐞𝐫 𝐨𝐟 𝐀𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐚𝐭𝐢𝐨𝐧 to ensure restricted access.
𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐟𝐮𝐥𝐥 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/isc2-issap-domain-4-4-2-architect-identity-authentication
Mastering this domain helps you design systems that are 𝐬𝐞𝐜𝐮𝐫𝐞, 𝐬𝐜𝐚𝐥𝐚𝐛𝐥𝐞, 𝐚𝐧𝐝 𝐮𝐬𝐞𝐫-𝐜𝐞𝐧𝐭𝐫𝐢𝐜.
#ISC2 #ISSAP #IdentitySecurity #AuthenticationArchitecture #MFA #ZeroTrust #CyberSecurity #InfosecTrain #IAM #SecurityArchitecture
𝐈𝐒𝐂𝟐 𝐈𝐒𝐒𝐀𝐏 𝐃𝐨𝐦𝐚𝐢𝐧 𝟒.𝟒.𝟐: 𝐀𝐫𝐜𝐡𝐢𝐭𝐞𝐜𝐭 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐀𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧
Every time you sign in ➡️ whether it’s to your email, bank account, social media, or work applications ➡️ it seems straightforward at first glance. Just enter a username and password but that simplicity is misleading.
In reality, clicking that login button sets off a carefully designed 𝐢𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐬𝐲𝐬𝐭𝐞𝐦 working behind the scenes➡️one that protects against attackers while still keeping the experience smooth and effortless for users.
✅ 𝐈𝐧 𝐈𝐒𝐂² 𝐈𝐒𝐒𝐀𝐏 𝐃𝐨𝐦𝐚𝐢𝐧, 𝐢𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐚𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 goes far beyond simply checking whether a user can log in. It focuses on how the login happens, where it’s coming from, and the level of risk involved at that moment, ensuring access is granted only when it truly makes sense from a security perspective.
➡️ 𝐖𝐡𝐚𝐭 𝐌𝐨𝐝𝐞𝐫𝐧 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐀𝐫𝐜𝐡𝐢𝐭𝐞𝐜𝐭𝐮𝐫𝐞 𝐃𝐞𝐦𝐚𝐧𝐝𝐬:
🔹 Takeaway #1: Implementing 𝐌𝐮𝐥𝐭𝐢-𝐅𝐚𝐜𝐭𝐨𝐫 𝐀𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 (𝐌𝐅𝐀) as a strong primary defense.
🔹Takeaway #2: Utilizing 𝐑𝐢𝐬𝐤-𝐁𝐚𝐬𝐞𝐝 𝐨𝐫 𝐀𝐝𝐚𝐩𝐭𝐢𝐯𝐞 𝐀𝐮𝐭𝐡𝐞𝐧𝐭𝐢𝐜𝐚𝐭𝐢𝐨𝐧 to assess login context.
🔹Takeaway #3: Leveraging 𝐅𝐞𝐝𝐞𝐫𝐚𝐭𝐞𝐝 𝐏𝐫𝐨𝐭𝐨𝐜𝐨𝐥𝐬 to grant access without exposing credentials.
🔹Takeaway #4: Applying a 𝐠𝐫𝐚𝐧𝐮𝐥𝐚𝐫 𝐥𝐚𝐲𝐞𝐫 𝐨𝐟 𝐀𝐮𝐭𝐡𝐨𝐫𝐢𝐳𝐚𝐭𝐢𝐨𝐧 to ensure restricted access.
👉 𝐑𝐞𝐚𝐝 𝐭𝐡𝐞 𝐟𝐮𝐥𝐥 𝐈𝐧𝐟𝐨𝐬𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐚𝐫𝐭𝐢𝐜𝐥𝐞 𝐡𝐞𝐫𝐞: https://www.infosectrain.com/blog/isc2-issap-domain-4-4-2-architect-identity-authentication
✅ Mastering this domain helps you design systems that are 𝐬𝐞𝐜𝐮𝐫𝐞, 𝐬𝐜𝐚𝐥𝐚𝐛𝐥𝐞, 𝐚𝐧𝐝 𝐮𝐬𝐞𝐫-𝐜𝐞𝐧𝐭𝐫𝐢𝐜.
#ISC2 #ISSAP #IdentitySecurity #AuthenticationArchitecture #MFA #ZeroTrust #CyberSecurity #InfosecTrain #IAM #SecurityArchitecture
0 Reacties
0 aandelen
3760 Views
0 voorbeeld