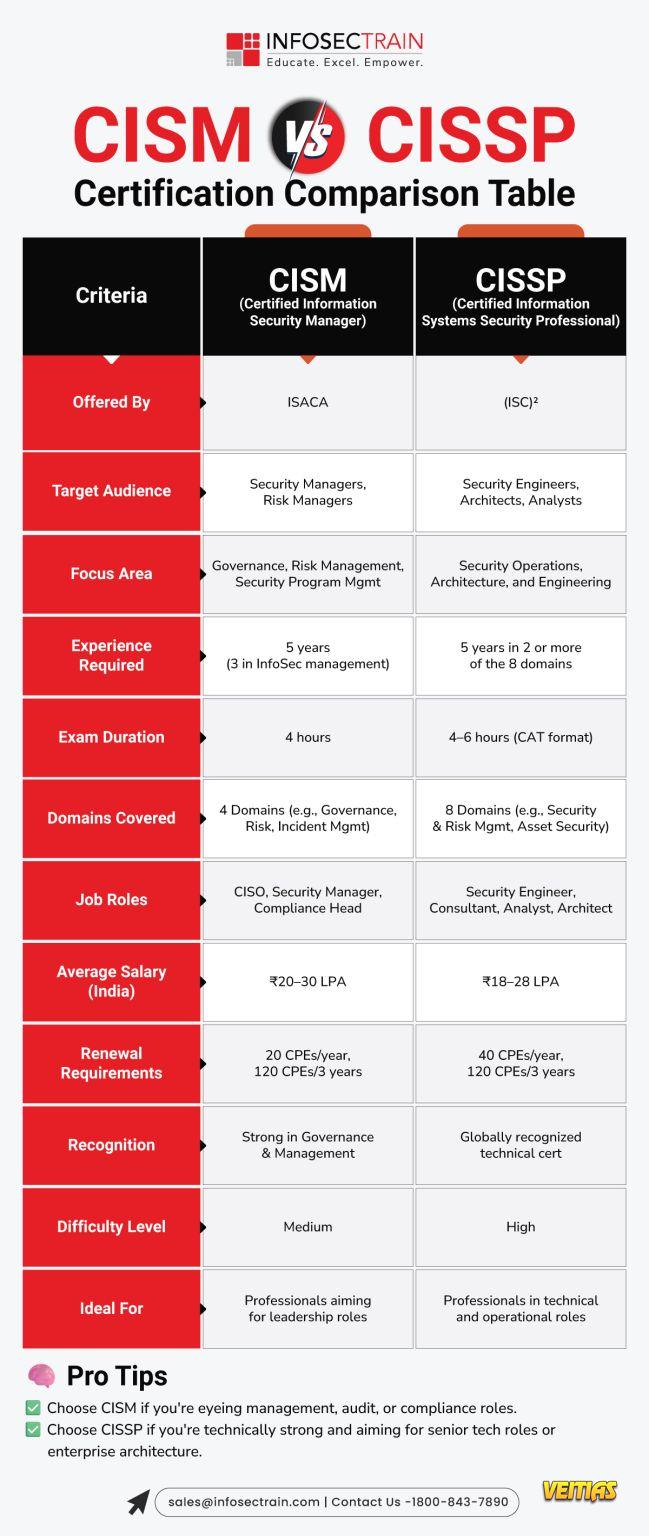
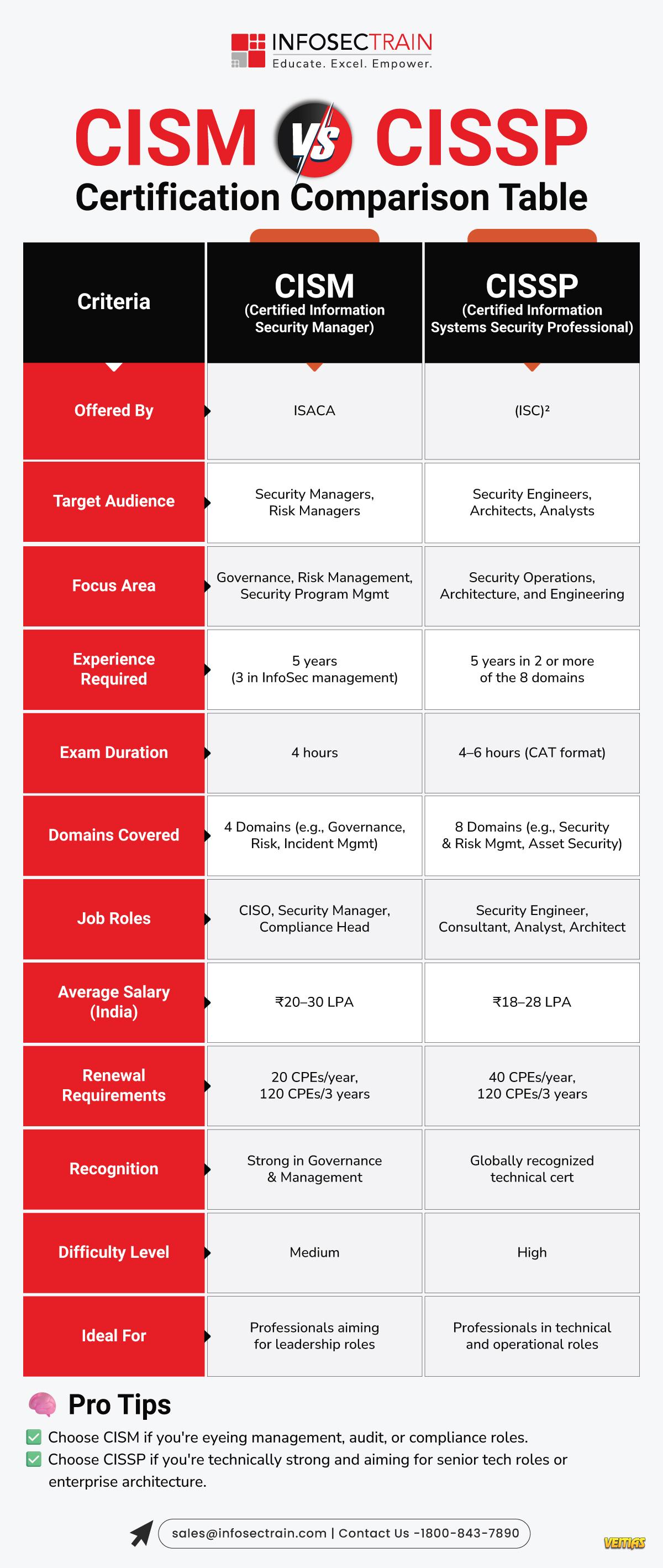
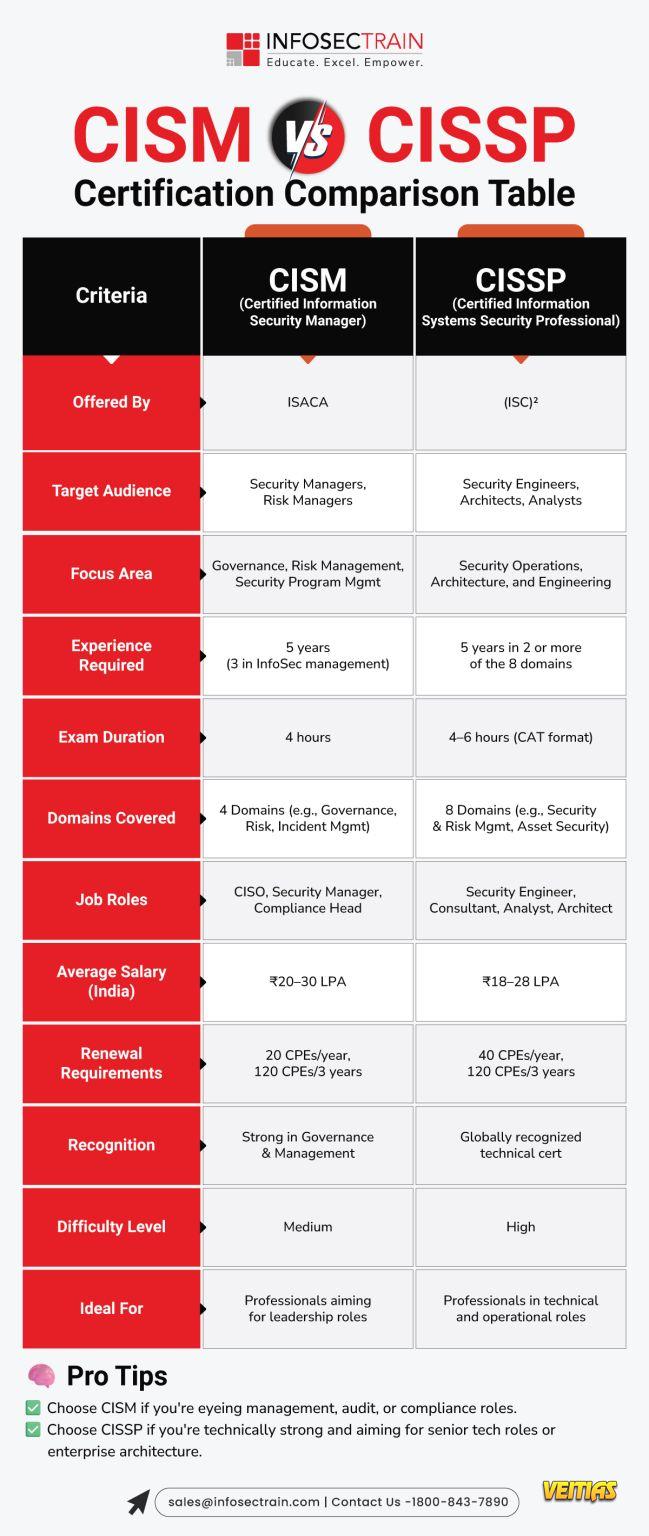
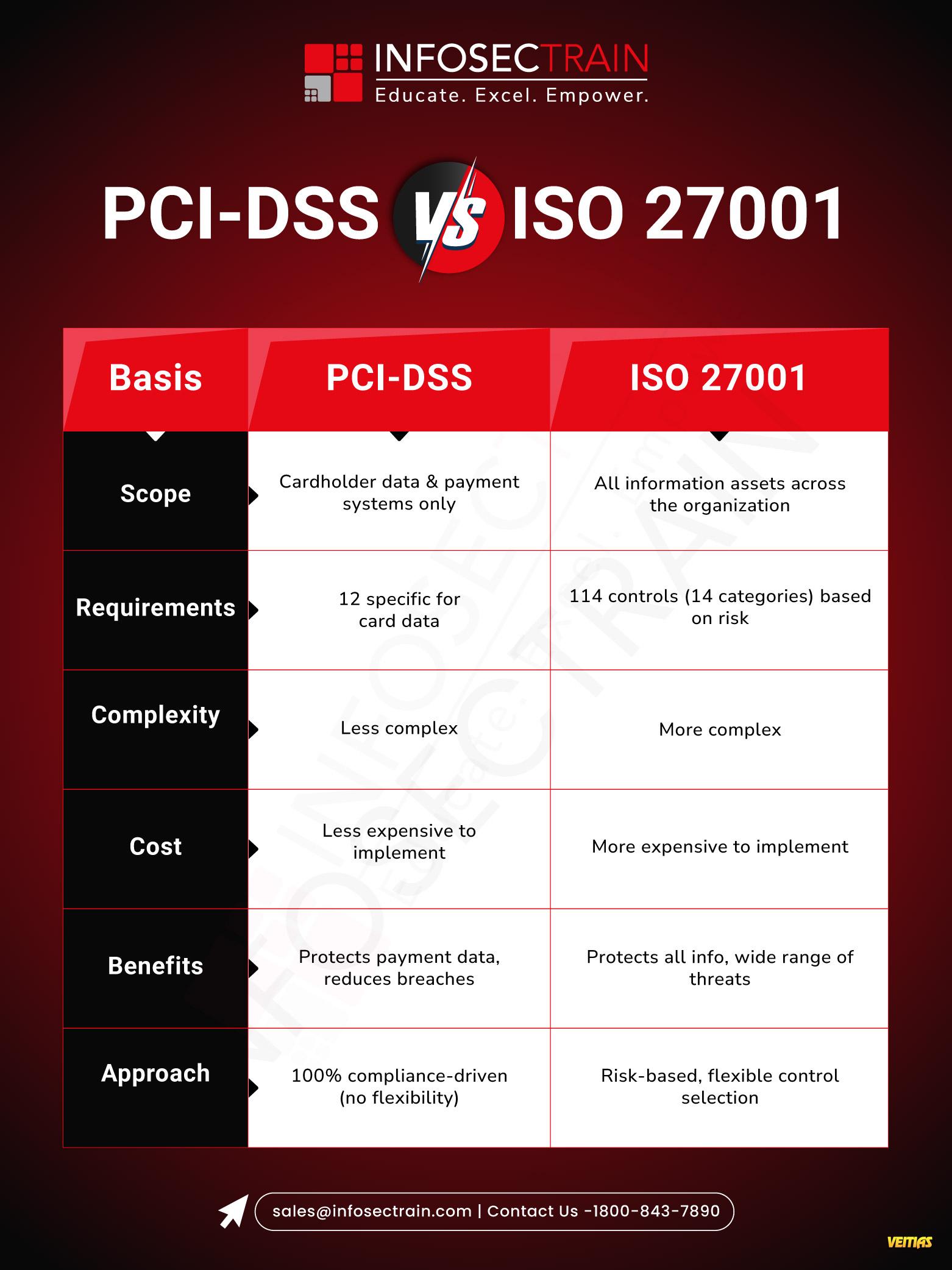
Google vs Microsoft vs Zoho: Which Intelligent Workspace Rules 2026?
In this YouTube video, we compare Google Workspace, Microsoft 365, and Zoho Workplace—three platforms redefining the future of AI-powered digital workspaces.
What you’ll discover:
AI copilots & automation capabilities
Security & compliance strengths
Collaboration and productivity tools
Integration with business ecosystems
Cost efficiency & scalability
Watch Here: https://youtu.be/rIK0013N1Lk?si=G2jgN2C4sGrS_bbg
#DigitalWorkspace #AIProductivity #GoogleWorkspace #Microsoft365 #ZohoWorkplace #FutureOfWork #TechComparison
In this YouTube video, we compare Google Workspace, Microsoft 365, and Zoho Workplace—three platforms redefining the future of AI-powered digital workspaces.
What you’ll discover:
AI copilots & automation capabilities
Security & compliance strengths
Collaboration and productivity tools
Integration with business ecosystems
Cost efficiency & scalability
Watch Here: https://youtu.be/rIK0013N1Lk?si=G2jgN2C4sGrS_bbg
#DigitalWorkspace #AIProductivity #GoogleWorkspace #Microsoft365 #ZohoWorkplace #FutureOfWork #TechComparison
Google vs Microsoft vs Zoho: Which Intelligent Workspace Rules 2026?
In this YouTube video, we compare Google Workspace, Microsoft 365, and Zoho Workplace—three platforms redefining the future of AI-powered digital workspaces.
🔍 What you’ll discover:
👉 AI copilots & automation capabilities
👉 Security & compliance strengths
👉 Collaboration and productivity tools
👉 Integration with business ecosystems
👉 Cost efficiency & scalability
Watch Here: https://youtu.be/rIK0013N1Lk?si=G2jgN2C4sGrS_bbg
#DigitalWorkspace #AIProductivity #GoogleWorkspace #Microsoft365 #ZohoWorkplace #FutureOfWork #TechComparison

0 Comentários
0 Compartilhamentos
4430 Visualizações
0 Anterior