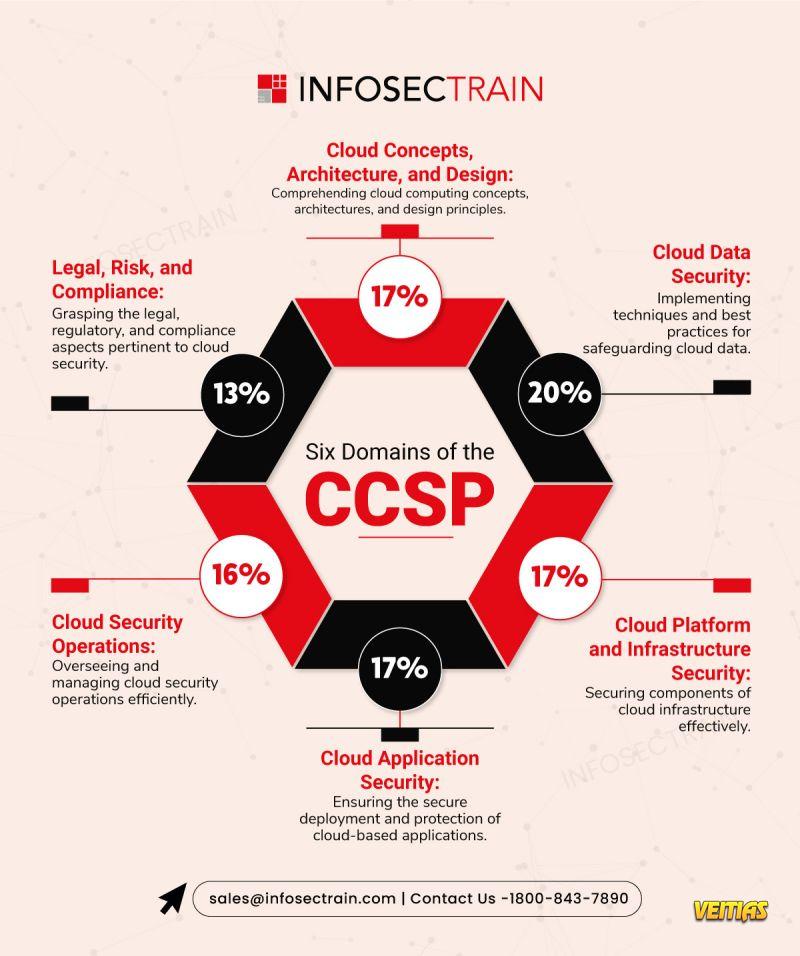
Master the Six Domains of the CCSP Certification!
Are you ready to validate your cloud security expertise and boost your career with the CCSP (Certified Cloud Security Professional) certification?
Check out more about CCSP here: https://www.infosectrain.com/courses/ccsp-certification-training/
Here’s a quick breakdown of the six essential domains covered in the given infographic.
Need help preparing? Let our experts guide you on your CCSP journey!
Contact us: sales@infosectrain.com
#CCSP #CloudSecurity #CyberSecurity #InfoSecTrain #CCSPDomains #ISC2 #CloudCertifications #CloudComputing #TechTraining #CareerInCybersecurity #SecurityProfessional #CloudExperts #Infosec
Are you ready to validate your cloud security expertise and boost your career with the CCSP (Certified Cloud Security Professional) certification?
Check out more about CCSP here: https://www.infosectrain.com/courses/ccsp-certification-training/
Here’s a quick breakdown of the six essential domains covered in the given infographic.
Need help preparing? Let our experts guide you on your CCSP journey!
Contact us: sales@infosectrain.com
#CCSP #CloudSecurity #CyberSecurity #InfoSecTrain #CCSPDomains #ISC2 #CloudCertifications #CloudComputing #TechTraining #CareerInCybersecurity #SecurityProfessional #CloudExperts #Infosec
Master the Six Domains of the CCSP Certification! ☁️🔐
Are you ready to validate your cloud security expertise and boost your career with the CCSP (Certified Cloud Security Professional) certification?
Check out more about CCSP here: https://www.infosectrain.com/courses/ccsp-certification-training/
Here’s a quick breakdown of the six essential domains covered in the given infographic.
📩 Need help preparing? Let our experts guide you on your CCSP journey!
📞 Contact us: sales@infosectrain.com
#CCSP #CloudSecurity #CyberSecurity #InfoSecTrain #CCSPDomains #ISC2 #CloudCertifications #CloudComputing #TechTraining #CareerInCybersecurity #SecurityProfessional #CloudExperts #Infosec
0 Yorumlar
0 hisse senetleri
2105 Views
0 önizleme