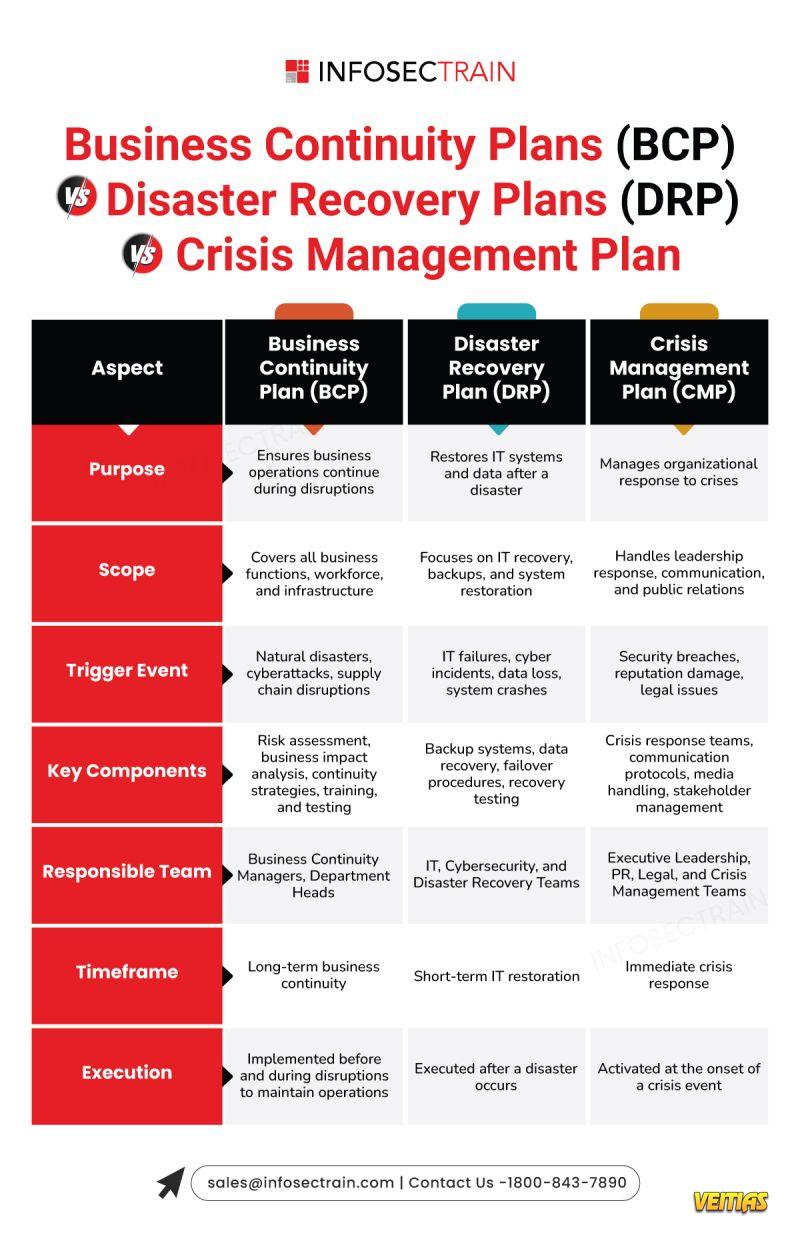
Business Continuity, Disaster Recovery, and Crisis Management are three critical components of an organization's resilience strategy, but they serve distinct purposes. Business Continuity (BC) focuses on ensuring that essential business functions continue to operate during and after a disruption. It involves proactive planning, risk assessment, and strategies to minimize downtime. Disaster Recovery (DR) is a subset of BC, primarily concerned with restoring IT infrastructure, data, and applications after a failure, cyberattack, or natural disaster.
Business Continuity, Disaster Recovery, and Crisis Management are three critical components of an organization's resilience strategy, but they serve distinct purposes. Business Continuity (BC) focuses on ensuring that essential business functions continue to operate during and after a disruption. It involves proactive planning, risk assessment, and strategies to minimize downtime. Disaster Recovery (DR) is a subset of BC, primarily concerned with restoring IT infrastructure, data, and applications after a failure, cyberattack, or natural disaster.
0 Comentários
0 Compartilhamentos
244 Visualizações
0 Anterior