In today’s data-driven world, knowing which standard or framework applies to your business is crucial. Here's a quick comparison to help you navigate the landscape:
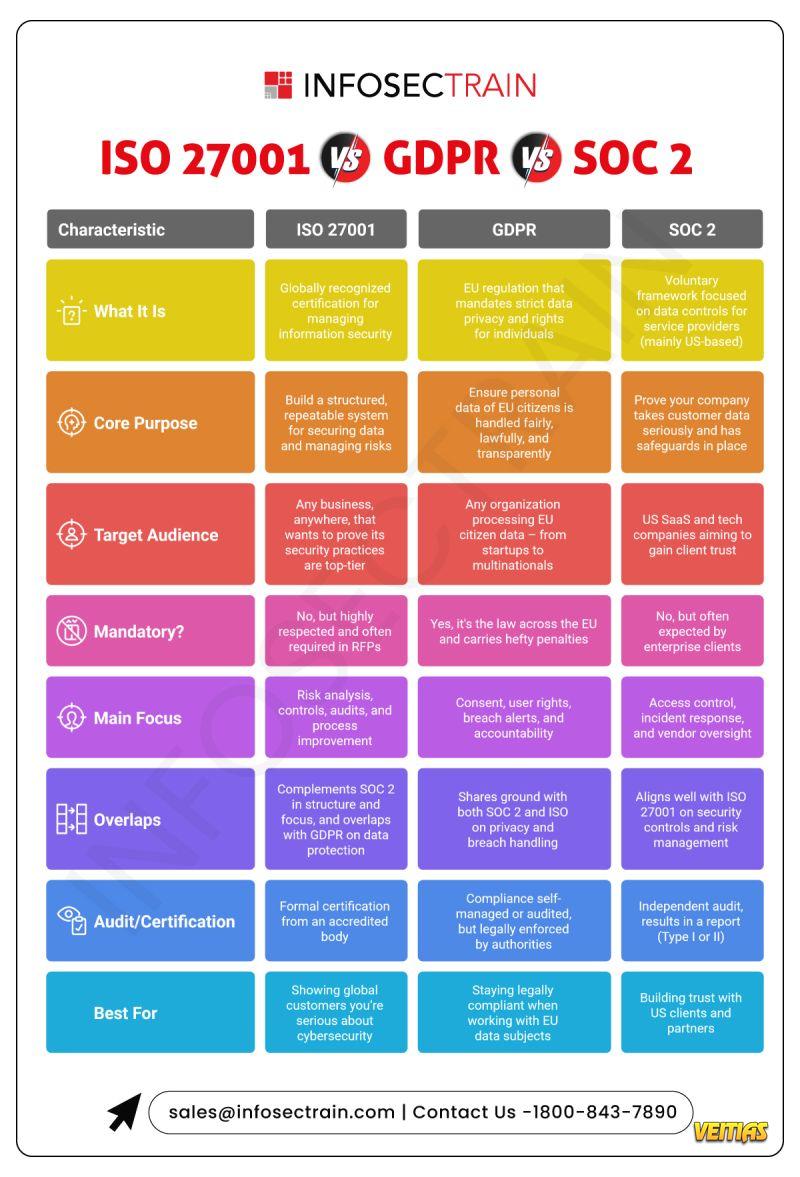
𝐈𝐒𝐎 𝟐𝟕𝟎𝟎𝟏
Global certification for information security management
Best for proving top-tier security practices
Focus: Risk management, controls, audits
Requires formal certification
𝐆𝐃𝐏𝐑
EU regulation for personal data protection
Legally mandatory for anyone handling EU citizen data
Focus: Consent, transparency, user rights
Enforced by data protection authorities
𝐒𝐎𝐂 𝟐
US-focused framework for service providers
Voluntary, but highly trusted by enterprise clients
Focus: Data security, access control, vendor oversight
Results in Type I/II audit reports
Overlap? Yes — all three focus on protecting data, managing risk, and building trust. But the approach, scope, and legal weight differ.
Whether you're chasing compliance, trust, or a competitive edge, understanding these frameworks is step one.
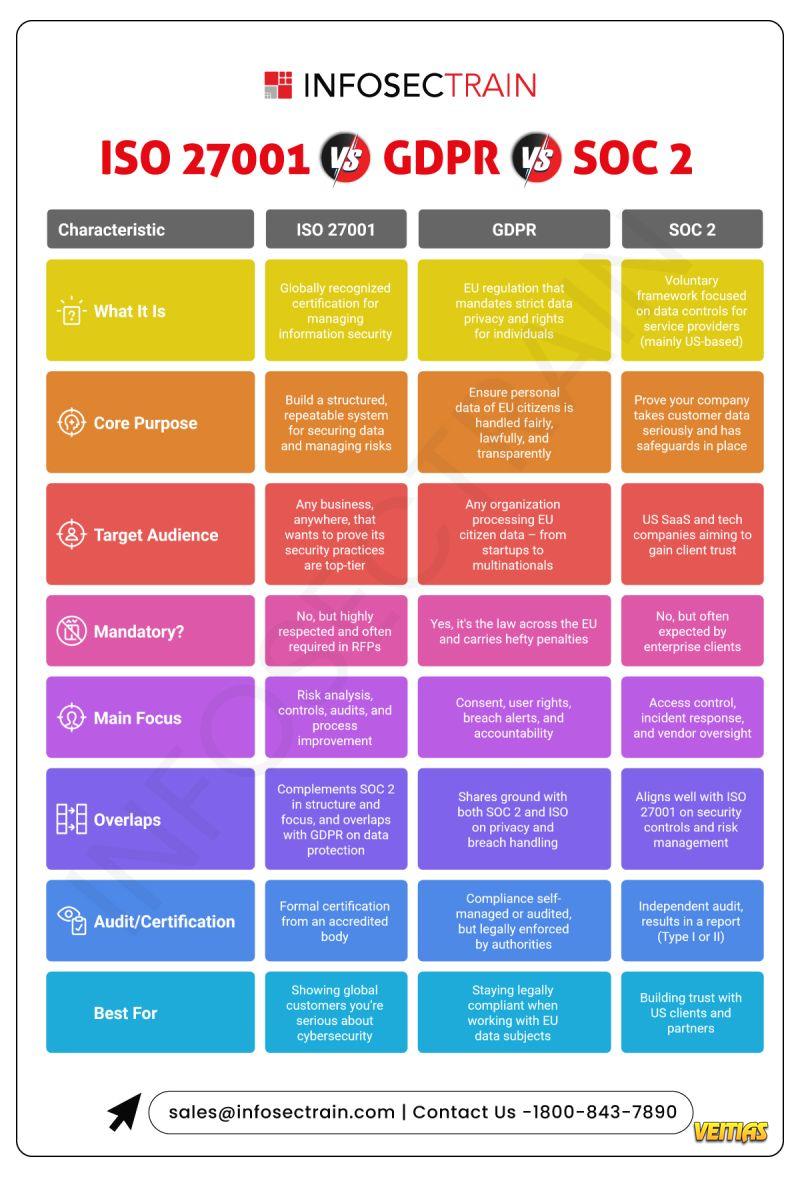
𝐈𝐒𝐎 𝟐𝟕𝟎𝟎𝟏
Global certification for information security management
Best for proving top-tier security practices
Focus: Risk management, controls, audits
Requires formal certification
𝐆𝐃𝐏𝐑
EU regulation for personal data protection
Legally mandatory for anyone handling EU citizen data
Focus: Consent, transparency, user rights
Enforced by data protection authorities
𝐒𝐎𝐂 𝟐
US-focused framework for service providers
Voluntary, but highly trusted by enterprise clients
Focus: Data security, access control, vendor oversight
Results in Type I/II audit reports
Overlap? Yes — all three focus on protecting data, managing risk, and building trust. But the approach, scope, and legal weight differ.
Whether you're chasing compliance, trust, or a competitive edge, understanding these frameworks is step one.
In today’s data-driven world, knowing which standard or framework applies to your business is crucial. Here's a quick comparison to help you navigate the landscape:
📌 𝐈𝐒𝐎 𝟐𝟕𝟎𝟎𝟏
🌍 Global certification for information security management
✅ Best for proving top-tier security practices
🛡️ Focus: Risk management, controls, audits
📄 Requires formal certification
📌 𝐆𝐃𝐏𝐑
🇪🇺 EU regulation for personal data protection
✅ Legally mandatory for anyone handling EU citizen data
🔐 Focus: Consent, transparency, user rights
⚖️ Enforced by data protection authorities
📌 𝐒𝐎𝐂 𝟐
🇺🇸 US-focused framework for service providers
✅ Voluntary, but highly trusted by enterprise clients
🧩 Focus: Data security, access control, vendor oversight
📑 Results in Type I/II audit reports
🧠 Overlap? Yes — all three focus on protecting data, managing risk, and building trust. But the approach, scope, and legal weight differ.
🎯 Whether you're chasing compliance, trust, or a competitive edge, understanding these frameworks is step one.
0 Comments
0 Shares
4512 Views
0 Reviews