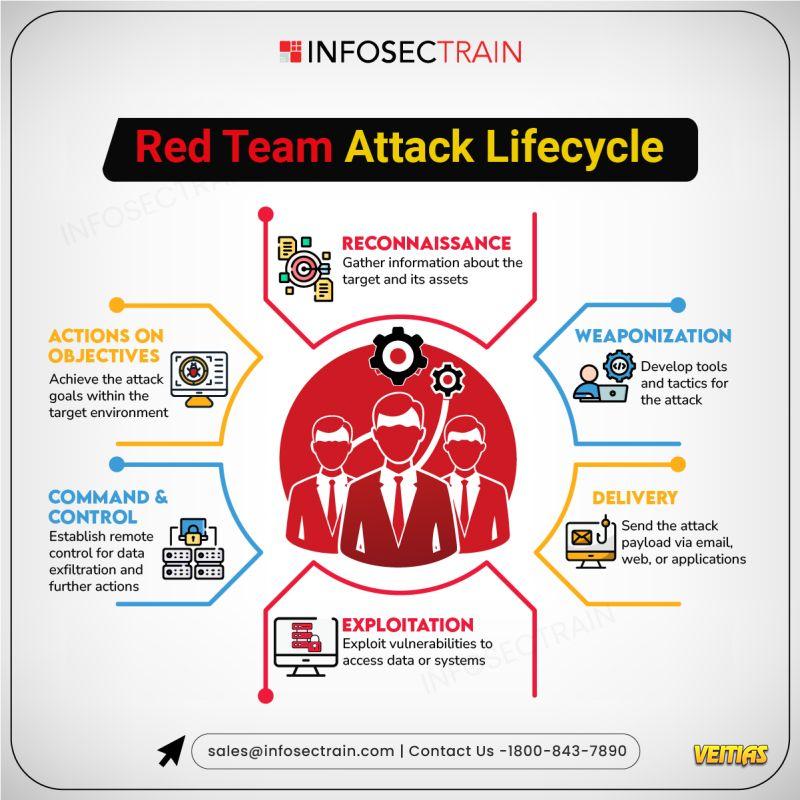
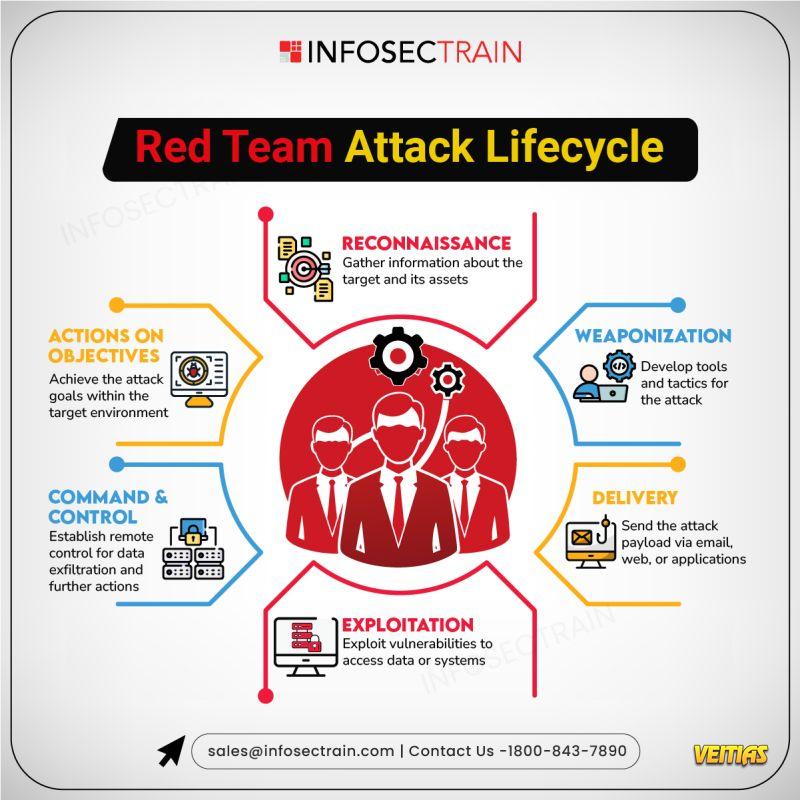
ISO Standards for Information and Cybersecurity
In today’s digital-first world, following the right standards isn’t optional—it’s essential. ISO standards provide a global framework to strengthen information security, ensure compliance, and build trust.
Key Focus Areas:
Core Information Security (ISO/IEC 27000 series)
Cybersecurity Framework & Controls
Privacy & Data Protection
Cloud & Emerging Technologies
Specialized & Supporting Standards
At InfosecTrain, we empower professionals with the knowledge and skills to implement, audit, and align with these ISO standards—helping you stay ahead in cybersecurity.
Don’t miss out! Enroll here to join InfosecTrain Free Webinar and unlock expert insights. https://www.infosectrain.com/events/
#ISO27001 #Cybersecurity #InformationSecurity #DataProtection #CloudSecurity #Compliance #InfosecTrain #ISMS #Privacy #RiskManagement #ISOStandards
In today’s digital-first world, following the right standards isn’t optional—it’s essential. ISO standards provide a global framework to strengthen information security, ensure compliance, and build trust.
Key Focus Areas:
Core Information Security (ISO/IEC 27000 series)
Cybersecurity Framework & Controls
Privacy & Data Protection
Cloud & Emerging Technologies
Specialized & Supporting Standards
At InfosecTrain, we empower professionals with the knowledge and skills to implement, audit, and align with these ISO standards—helping you stay ahead in cybersecurity.
Don’t miss out! Enroll here to join InfosecTrain Free Webinar and unlock expert insights. https://www.infosectrain.com/events/
#ISO27001 #Cybersecurity #InformationSecurity #DataProtection #CloudSecurity #Compliance #InfosecTrain #ISMS #Privacy #RiskManagement #ISOStandards
🔐 ISO Standards for Information and Cybersecurity
In today’s digital-first world, following the right standards isn’t optional—it’s essential. ISO standards provide a global framework to strengthen information security, ensure compliance, and build trust.
📌 Key Focus Areas:
✔️ Core Information Security (ISO/IEC 27000 series)
✔️ Cybersecurity Framework & Controls
✔️ Privacy & Data Protection
✔️ Cloud & Emerging Technologies
✔️ Specialized & Supporting Standards
💡 At InfosecTrain, we empower professionals with the knowledge and skills to implement, audit, and align with these ISO standards—helping you stay ahead in cybersecurity.
Don’t miss out! Enroll here to join InfosecTrain Free Webinar and unlock expert insights. 👉 https://www.infosectrain.com/events/
#ISO27001 #Cybersecurity #InformationSecurity #DataProtection #CloudSecurity #Compliance #InfosecTrain #ISMS #Privacy #RiskManagement #ISOStandards
0 Kommentare
0 Anteile
1763 Ansichten
0 Vorschau