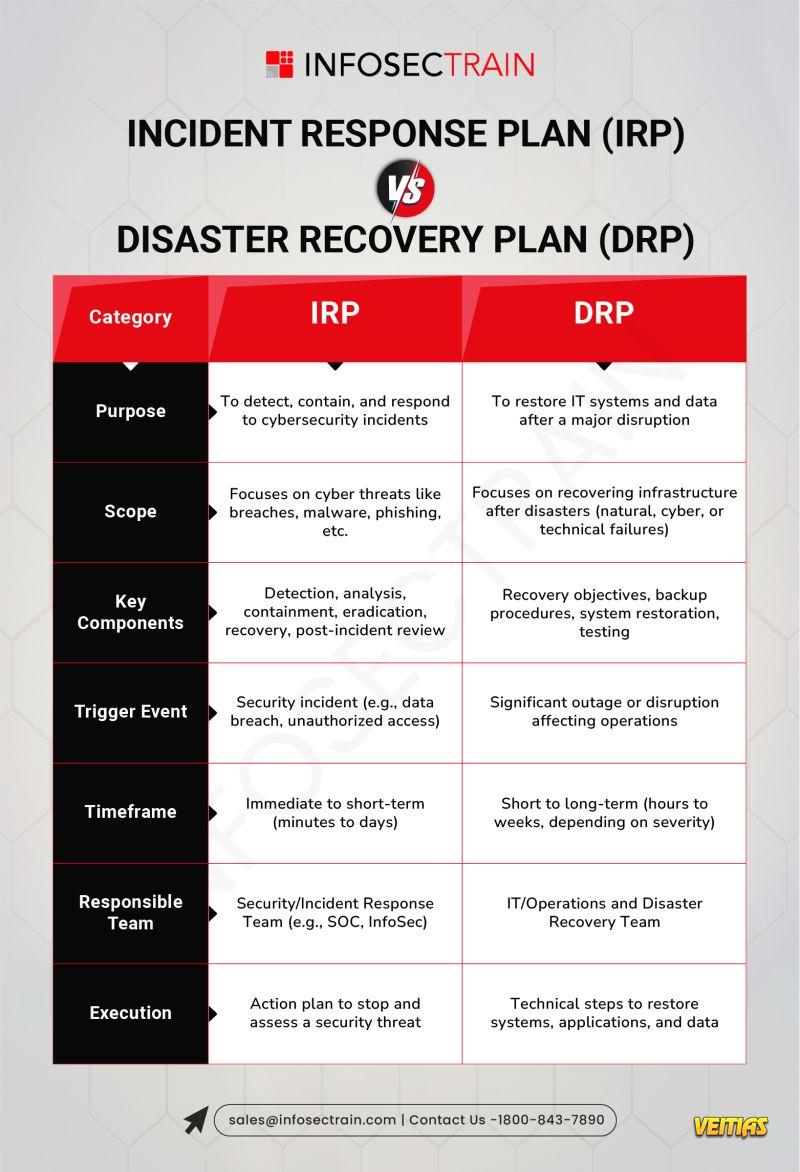
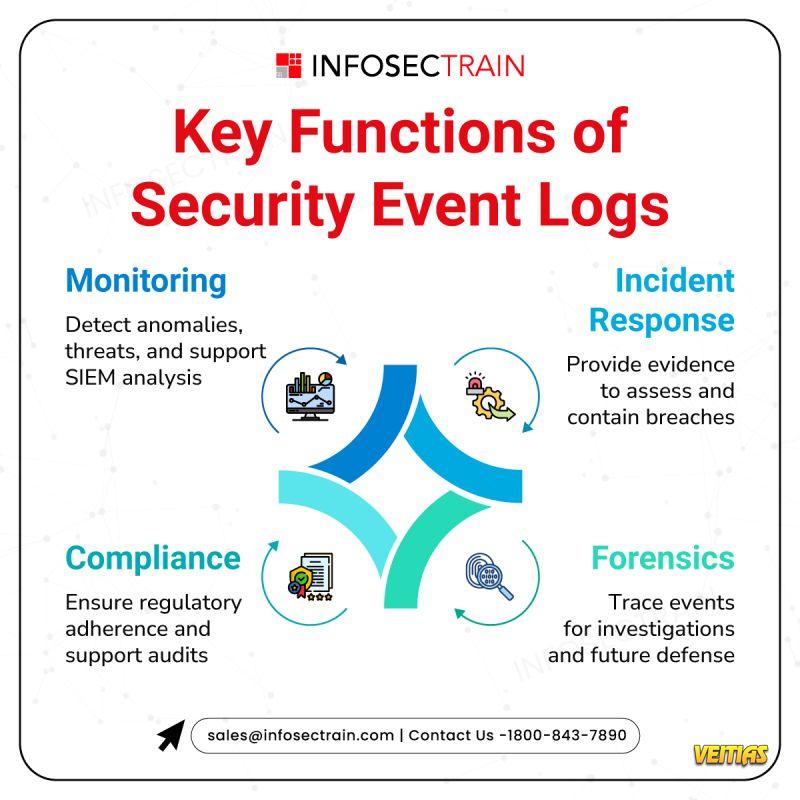
What is Azure Sentinel?
Microsoft’s Azure Sentinel is more than just a cloud-based security tool it's a powerful combination of SIEM + SOAR that delivers real-time threat detection, advanced analytics, and automated incident response.
Read Here: https://infosec-train.blogspot.com/2025/06/what-is-azure-sentinel.html
#AzureSentinel #CyberSecurity #SIEM #SOAR #ThreatDetection #IncidentResponse #MicrosoftSecurity #CloudSecurity #Infosec #CyberDefense #SOC #InfosecTrain
Microsoft’s Azure Sentinel is more than just a cloud-based security tool it's a powerful combination of SIEM + SOAR that delivers real-time threat detection, advanced analytics, and automated incident response.
Read Here: https://infosec-train.blogspot.com/2025/06/what-is-azure-sentinel.html
#AzureSentinel #CyberSecurity #SIEM #SOAR #ThreatDetection #IncidentResponse #MicrosoftSecurity #CloudSecurity #Infosec #CyberDefense #SOC #InfosecTrain
What is Azure Sentinel?
Microsoft’s Azure Sentinel is more than just a cloud-based security tool it's a powerful combination of SIEM + SOAR that delivers real-time threat detection, advanced analytics, and automated incident response.
Read Here: https://infosec-train.blogspot.com/2025/06/what-is-azure-sentinel.html
#AzureSentinel #CyberSecurity #SIEM #SOAR #ThreatDetection #IncidentResponse #MicrosoftSecurity #CloudSecurity #Infosec #CyberDefense #SOC #InfosecTrain
0 Commentarii
0 Distribuiri
2203 Views
0 previzualizare