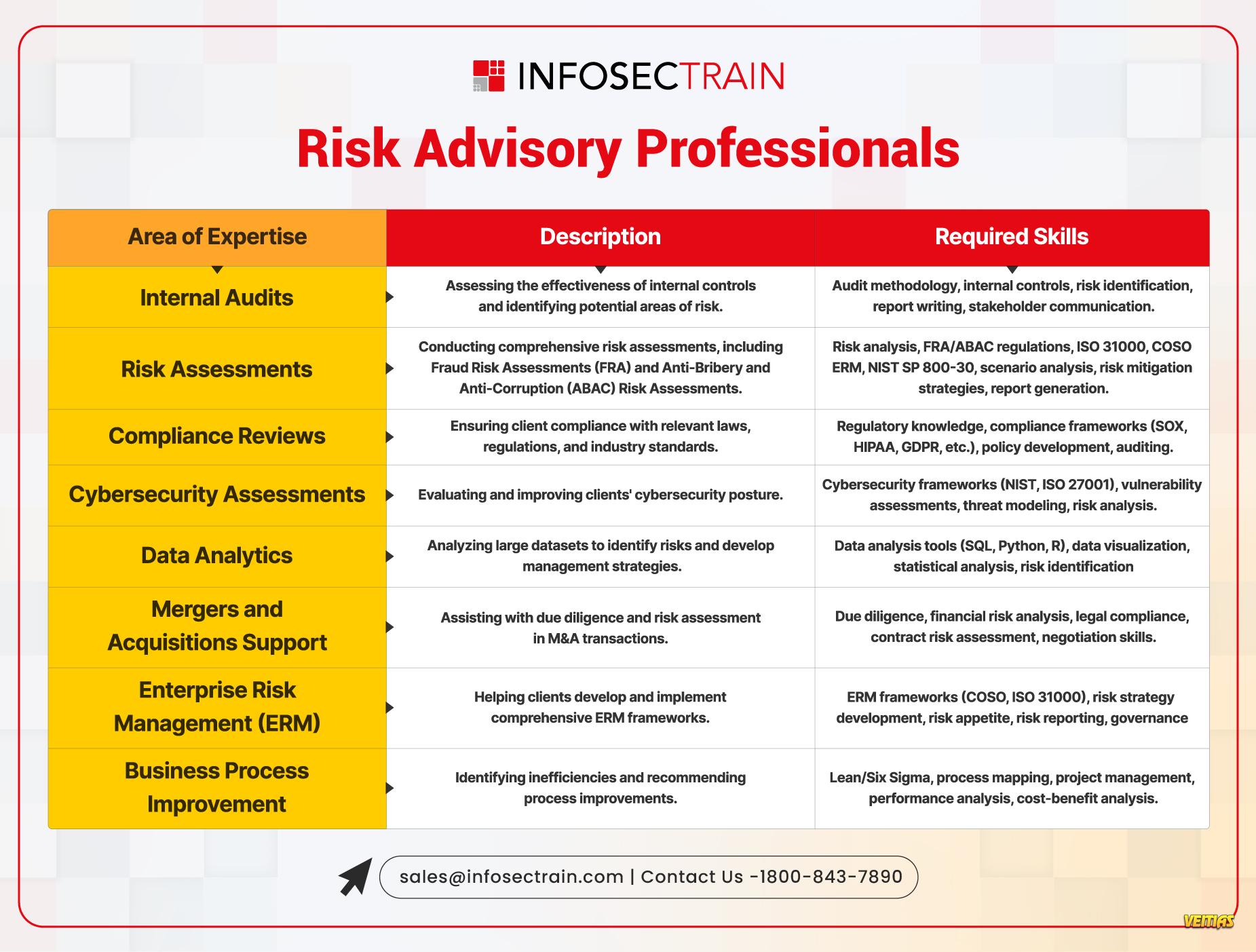
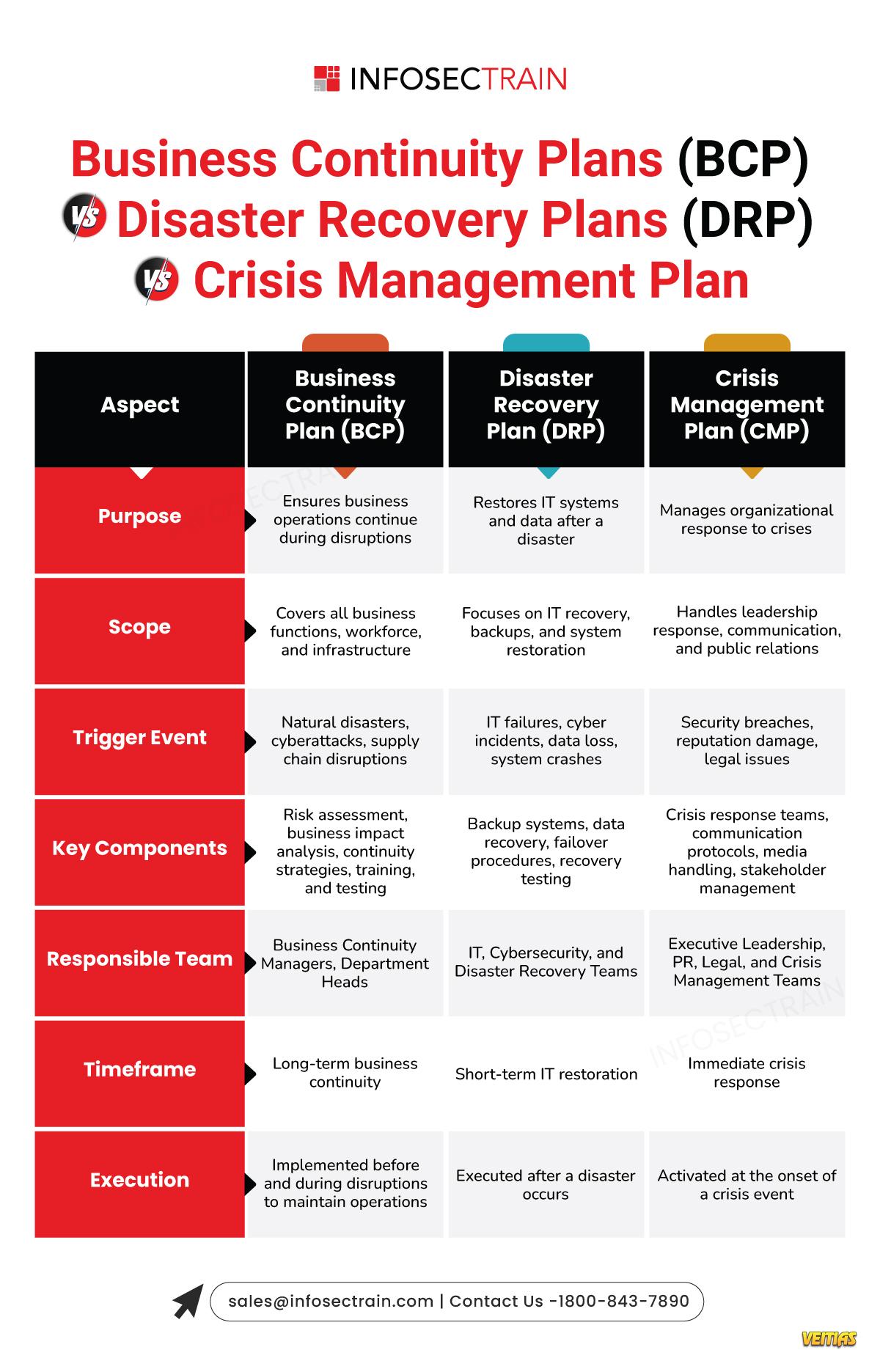
Canvas of Cybersecurity: Building a Strong Digital Defense!
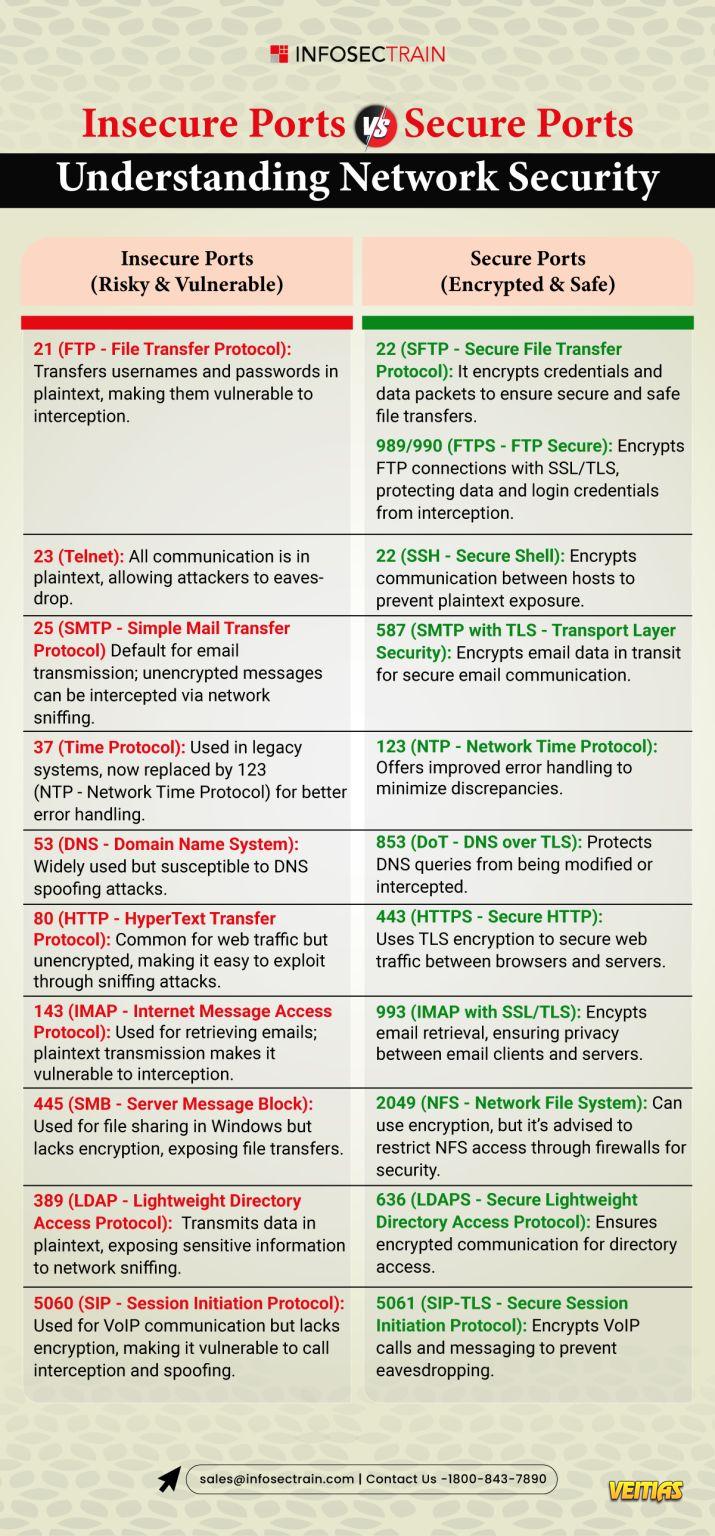
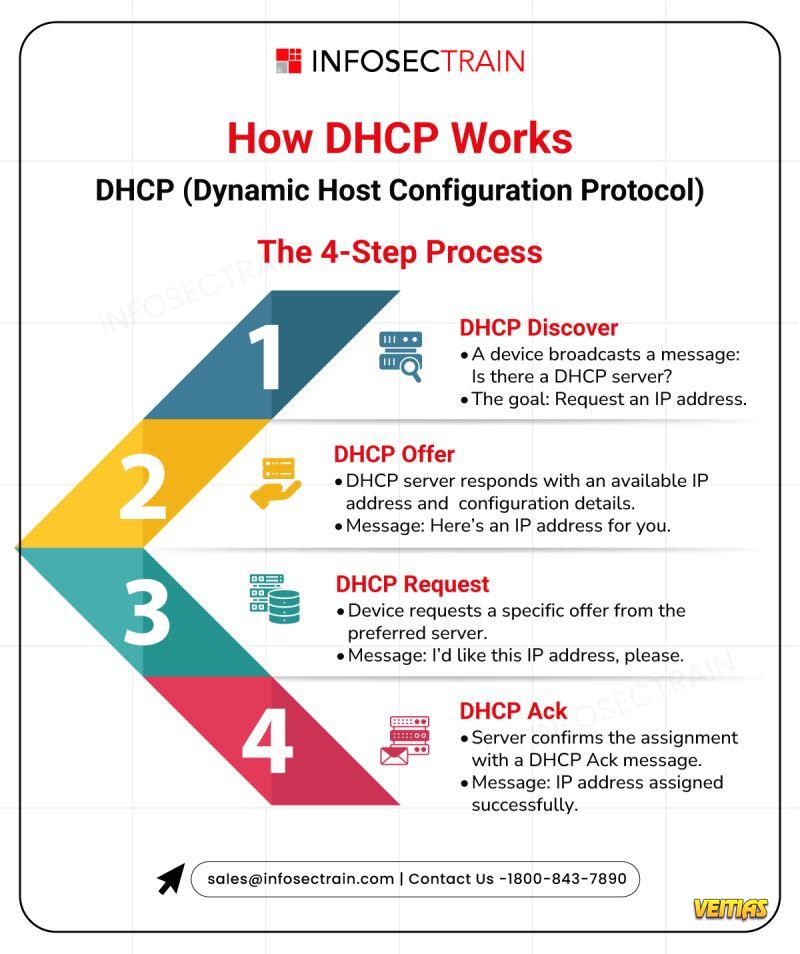
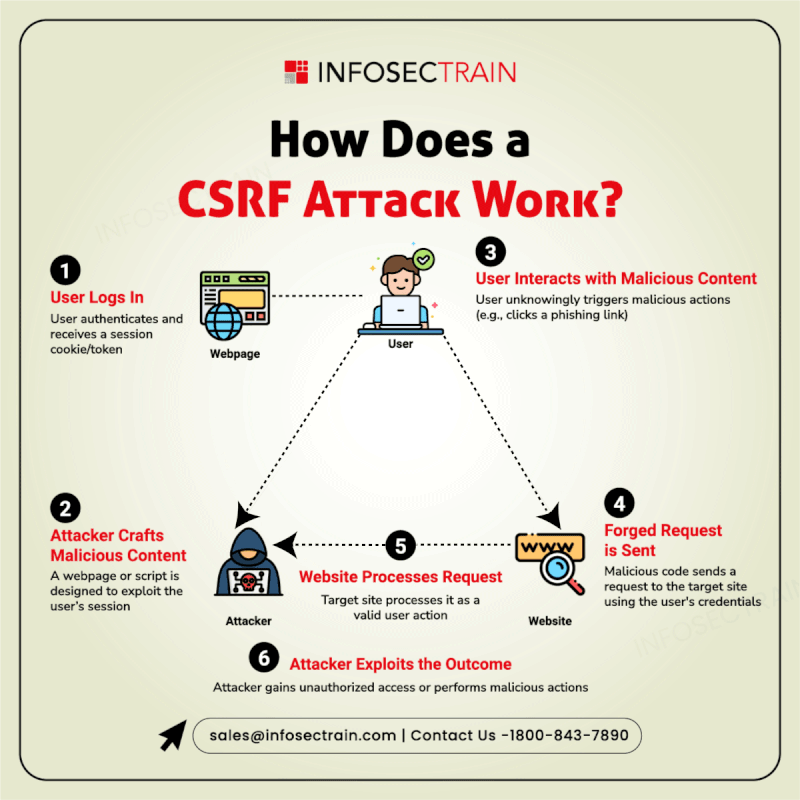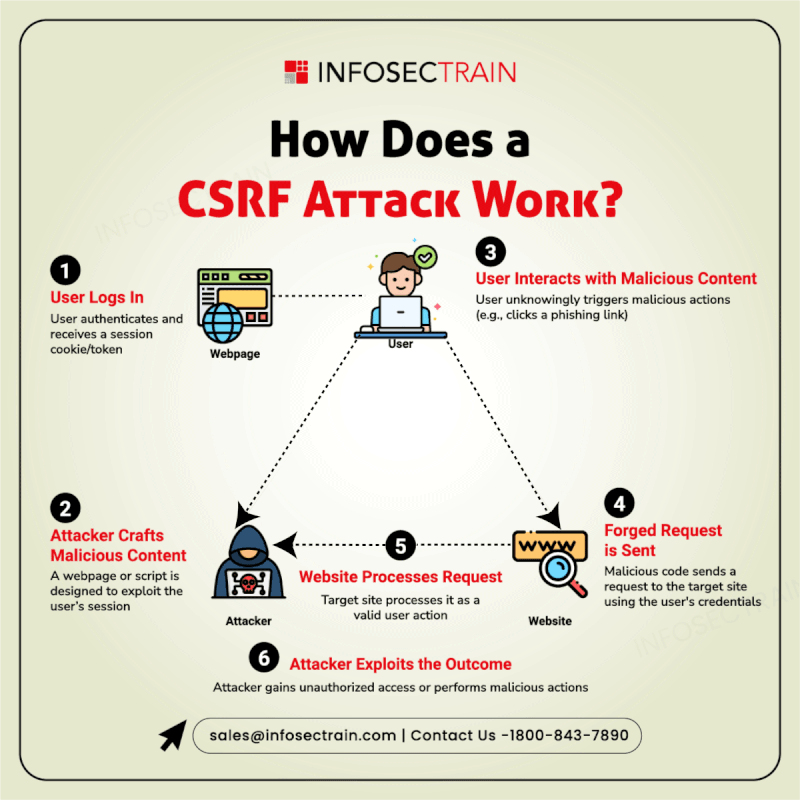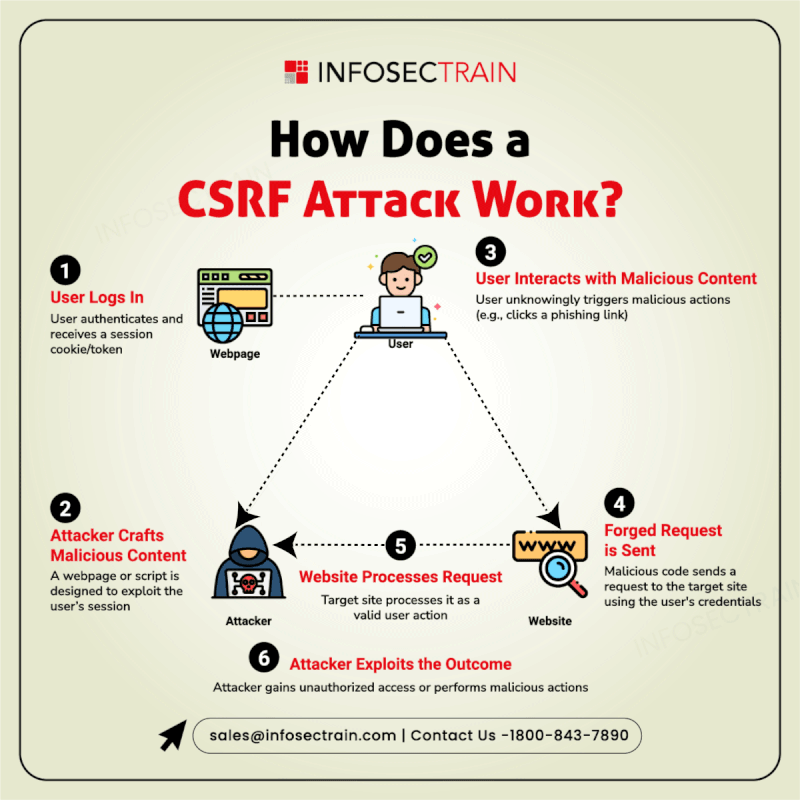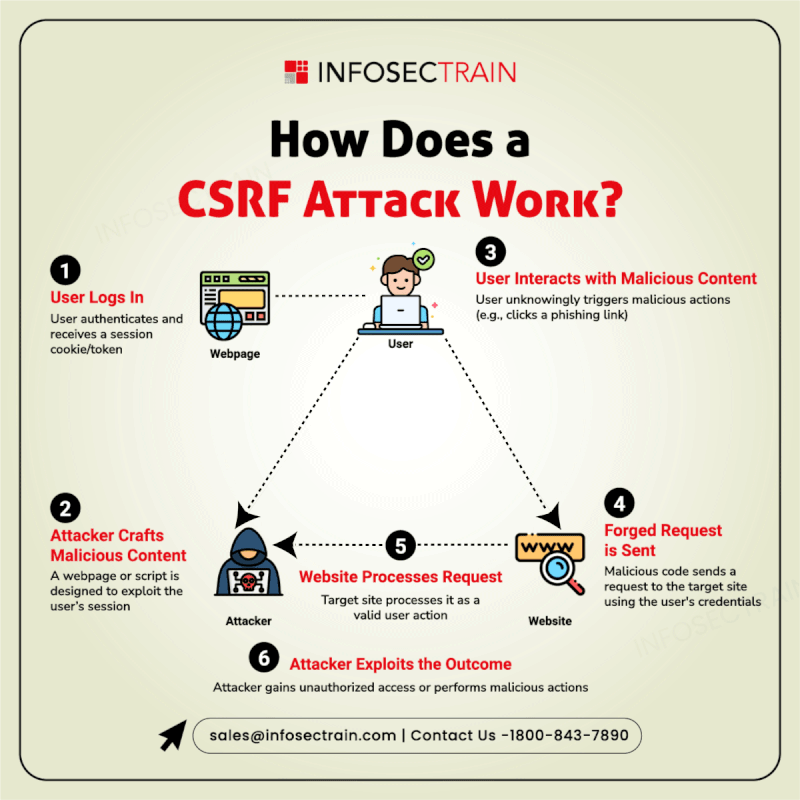
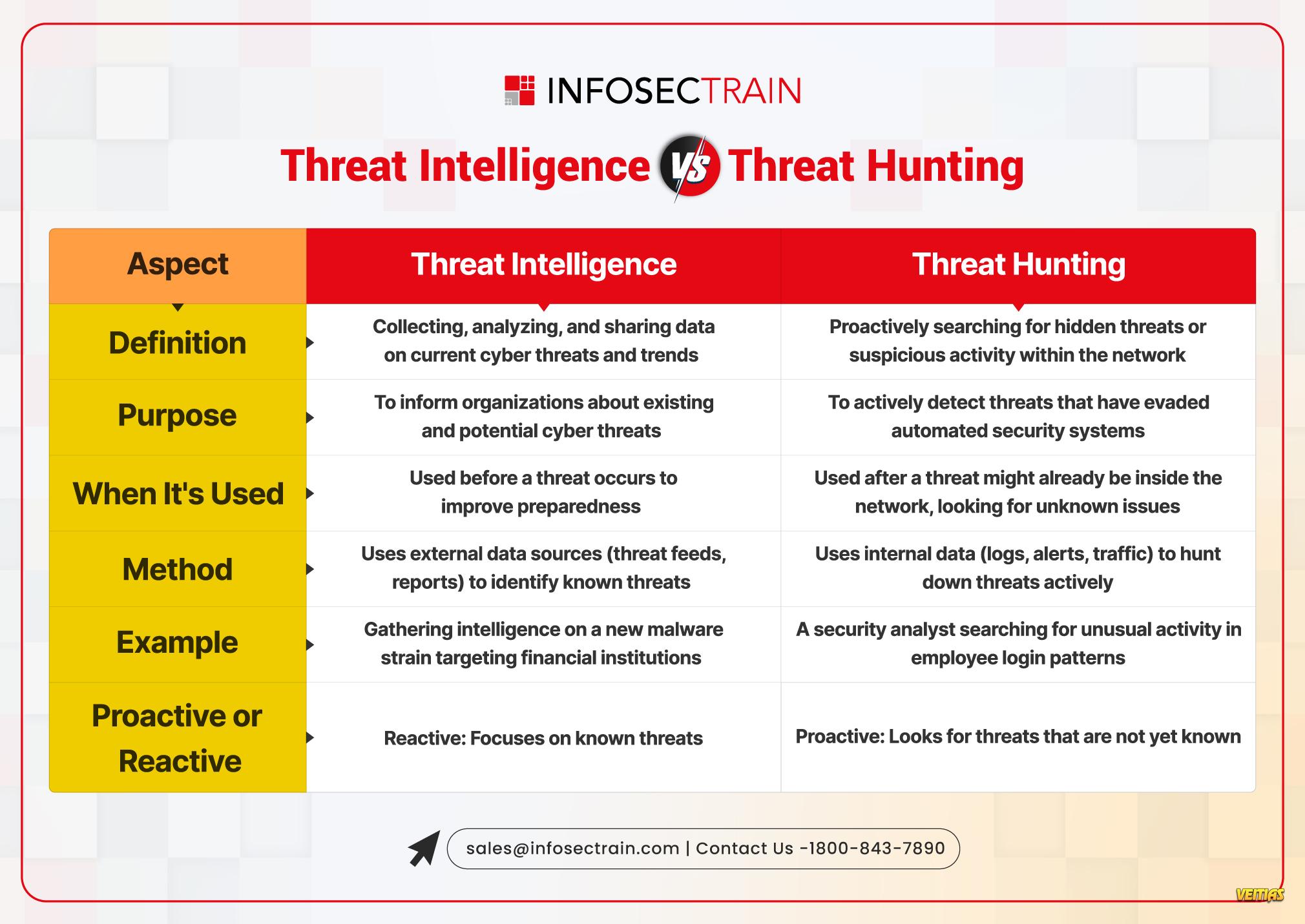
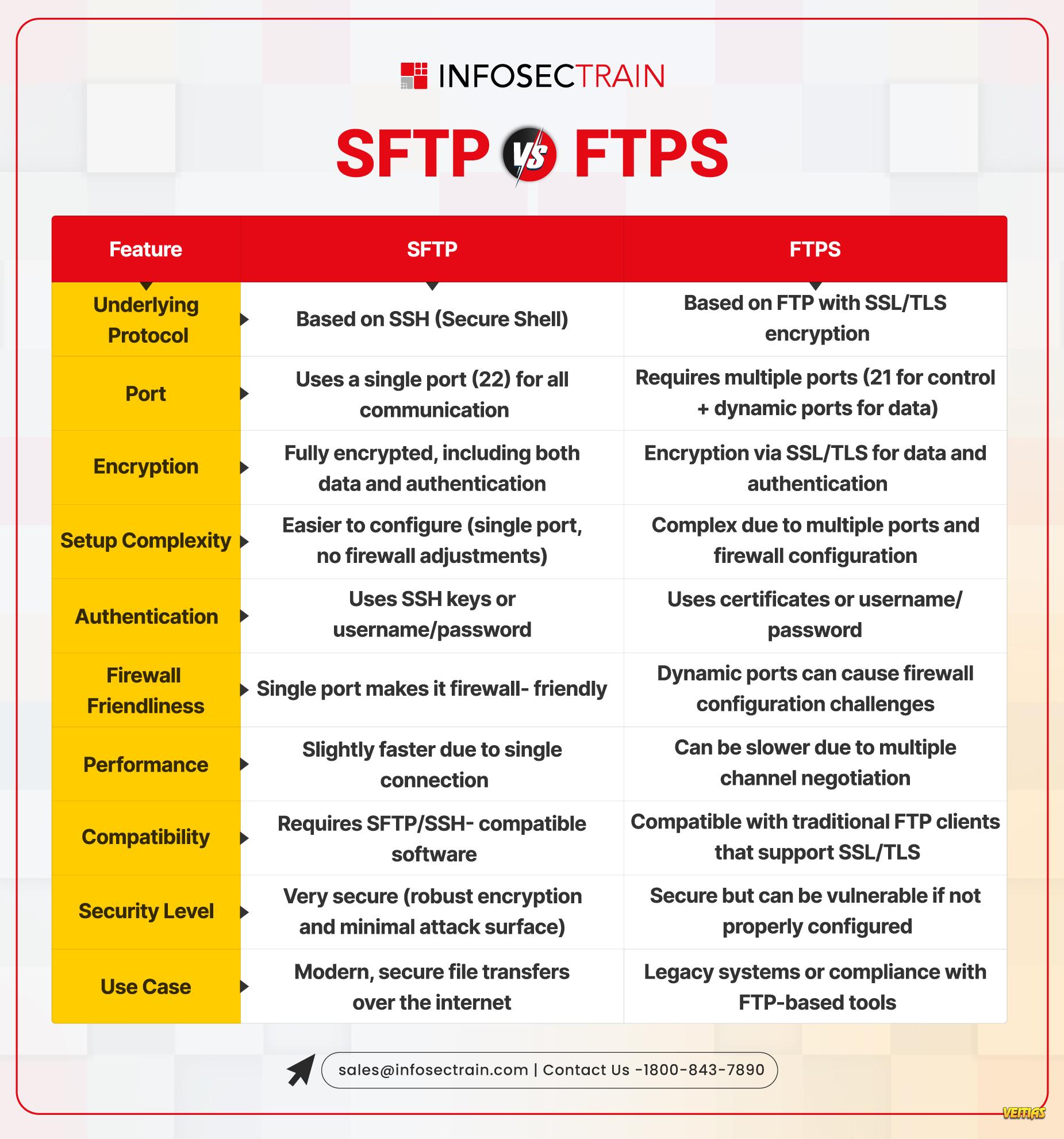
Cybersecurity is a vast and evolving landscape that requires continuous learning and adaptation. InfosecTrain’s latest infographic provides a comprehensive overview of key cybersecurity domains, including:
Top Cybersecurity Trends - https://www.infosectrain.com/blog/top-cybersecurity-trends/
Stay ahead of evolving threats with InfosecTrain’s expert-led cybersecurity training!
#CyberSecurity #InfoSec #NetworkSecurity #CloudSecurity #RiskManagement #EthicalHacking #SecurityTraining #CyberAwareness #ThreatIntelligence #InfosecTrain #CyberDefense #DataProtection
Leia mais Cybersecurity is a vast and evolving landscape that requires continuous learning and adaptation. InfosecTrain’s latest infographic provides a comprehensive overview of key cybersecurity domains, including:
Top Cybersecurity Trends - https://www.infosectrain.com/blog/top-cybersecurity-trends/
Stay ahead of evolving threats with InfosecTrain’s expert-led cybersecurity training!
#CyberSecurity #InfoSec #NetworkSecurity #CloudSecurity #RiskManagement #EthicalHacking #SecurityTraining #CyberAwareness #ThreatIntelligence #InfosecTrain #CyberDefense #DataProtection
Canvas of Cybersecurity: Building a Strong Digital Defense!
Cybersecurity is a vast and evolving landscape that requires continuous learning and adaptation. InfosecTrain’s latest infographic provides a comprehensive overview of key cybersecurity domains, including:
Top Cybersecurity Trends - https://www.infosectrain.com/blog/top-cybersecurity-trends/
Stay ahead of evolving threats with InfosecTrain’s expert-led cybersecurity training!
#CyberSecurity #InfoSec #NetworkSecurity #CloudSecurity #RiskManagement #EthicalHacking #SecurityTraining #CyberAwareness #ThreatIntelligence #InfosecTrain #CyberDefense #DataProtection
0 Comentários
0 Compartilhamentos
1011 Visualizações
0 Anterior