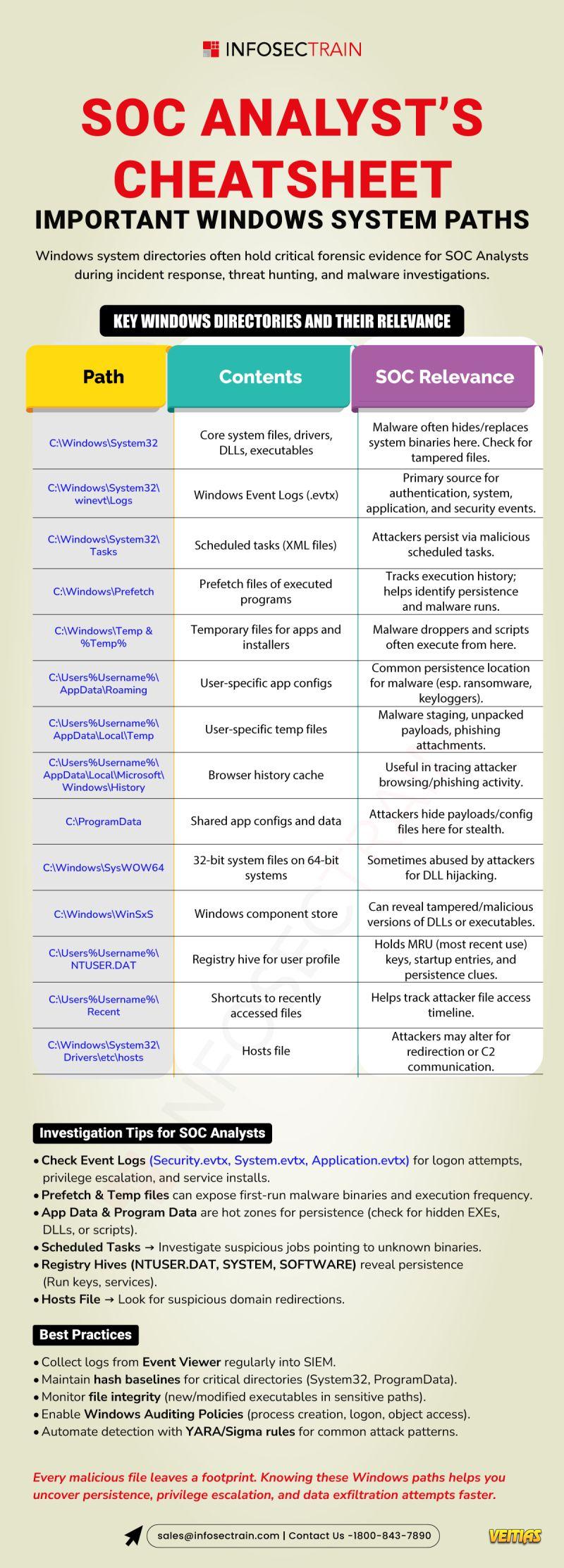
ROOTKIT VS BOOTKIT
Your antivirus wakes up after the attack.
A bootkit already owns the machine before the OS even starts.
That single difference decides everything:
Malware gets detected
Or it’s never seen at all
Rootkits hide inside the system.
Bootkits rewrite trust itself.
If you still believe “endpoint security” starts at login…
you’re already too late.
🛡 Real security begins before the operating system does.
𝐋𝐞𝐚𝐫𝐧 𝐝𝐢𝐫𝐞𝐜𝐭𝐥𝐲 𝐟𝐫𝐨𝐦 𝐢𝐧𝐝𝐮𝐬𝐭𝐫𝐲 𝐞𝐱𝐩𝐞𝐫𝐭𝐬—𝐜𝐡𝐞𝐜𝐤 𝐨𝐮𝐭 𝐈𝐧𝐟𝐨𝐒𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐟𝐨𝐫 𝐚 𝐟𝐫𝐞𝐞 𝐰𝐞𝐛𝐢𝐧𝐚𝐫 𝐡𝐞𝐫𝐞 : https://www.infosectrain.com/events
#CyberSecurity #Malware #Bootkit #Rootkit #EndpointSecurity #ZeroTrust #ThreatLandscape
Your antivirus wakes up after the attack.
A bootkit already owns the machine before the OS even starts.
That single difference decides everything:
Malware gets detected
Or it’s never seen at all
Rootkits hide inside the system.
Bootkits rewrite trust itself.
If you still believe “endpoint security” starts at login…
you’re already too late.
🛡 Real security begins before the operating system does.
𝐋𝐞𝐚𝐫𝐧 𝐝𝐢𝐫𝐞𝐜𝐭𝐥𝐲 𝐟𝐫𝐨𝐦 𝐢𝐧𝐝𝐮𝐬𝐭𝐫𝐲 𝐞𝐱𝐩𝐞𝐫𝐭𝐬—𝐜𝐡𝐞𝐜𝐤 𝐨𝐮𝐭 𝐈𝐧𝐟𝐨𝐒𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐟𝐨𝐫 𝐚 𝐟𝐫𝐞𝐞 𝐰𝐞𝐛𝐢𝐧𝐚𝐫 𝐡𝐞𝐫𝐞 : https://www.infosectrain.com/events
#CyberSecurity #Malware #Bootkit #Rootkit #EndpointSecurity #ZeroTrust #ThreatLandscape
ROOTKIT VS BOOTKIT
Your antivirus wakes up after the attack.
A bootkit already owns the machine before the OS even starts.
That single difference decides everything:
🔹 Malware gets detected
🔹 Or it’s never seen at all
Rootkits hide inside the system.
Bootkits rewrite trust itself.
If you still believe “endpoint security” starts at login…
you’re already too late.
🛡 Real security begins before the operating system does.
𝐋𝐞𝐚𝐫𝐧 𝐝𝐢𝐫𝐞𝐜𝐭𝐥𝐲 𝐟𝐫𝐨𝐦 𝐢𝐧𝐝𝐮𝐬𝐭𝐫𝐲 𝐞𝐱𝐩𝐞𝐫𝐭𝐬—𝐜𝐡𝐞𝐜𝐤 𝐨𝐮𝐭 𝐈𝐧𝐟𝐨𝐒𝐞𝐜𝐓𝐫𝐚𝐢𝐧 𝐟𝐨𝐫 𝐚 𝐟𝐫𝐞𝐞 𝐰𝐞𝐛𝐢𝐧𝐚𝐫 𝐡𝐞𝐫𝐞 : https://www.infosectrain.com/events
#CyberSecurity #Malware #Bootkit #Rootkit #EndpointSecurity #ZeroTrust #ThreatLandscape
0 Comentários
0 Compartilhamentos
4299 Visualizações
0 Anterior