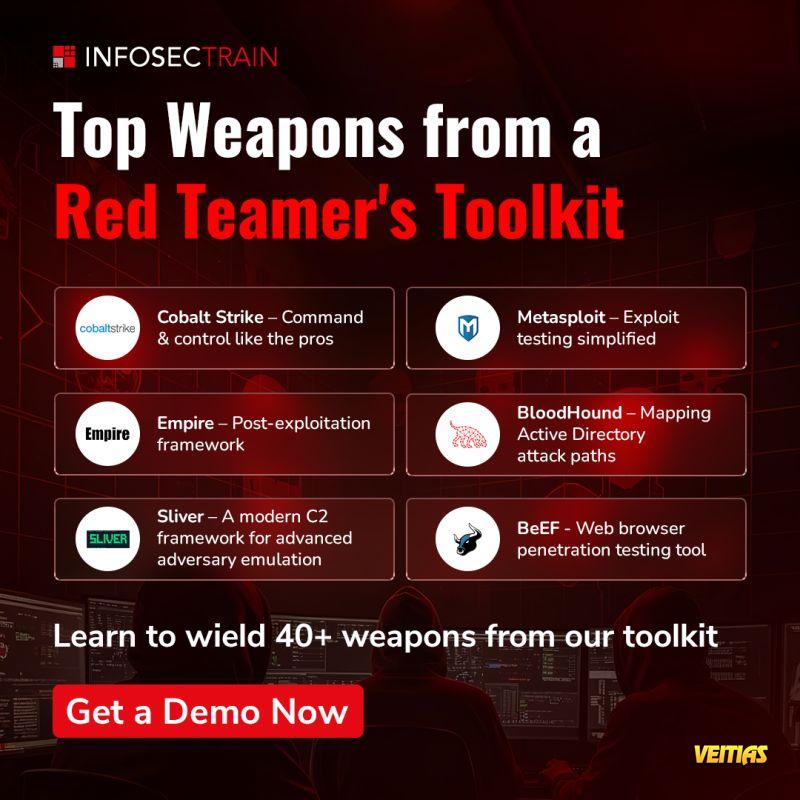
Red Team Masterclass: How Cyber Attacks Are Crafted & Executed [part 1]
What You’ll Learn in This Masterclass: Day - 1
What is Red Teaming?
Red Teaming vs Penetration Testing
Types of Red Team Engagement
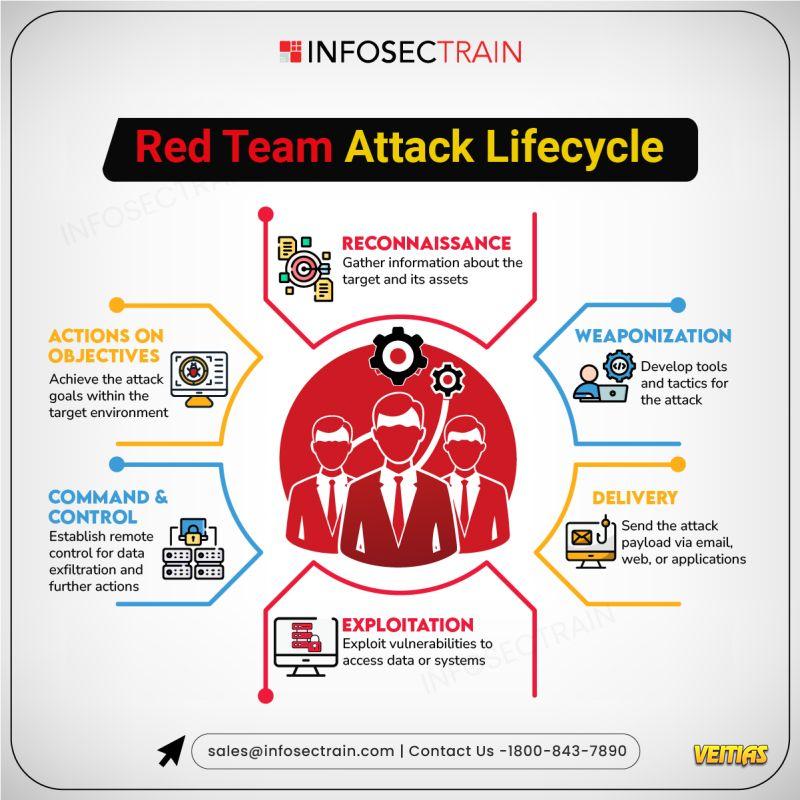
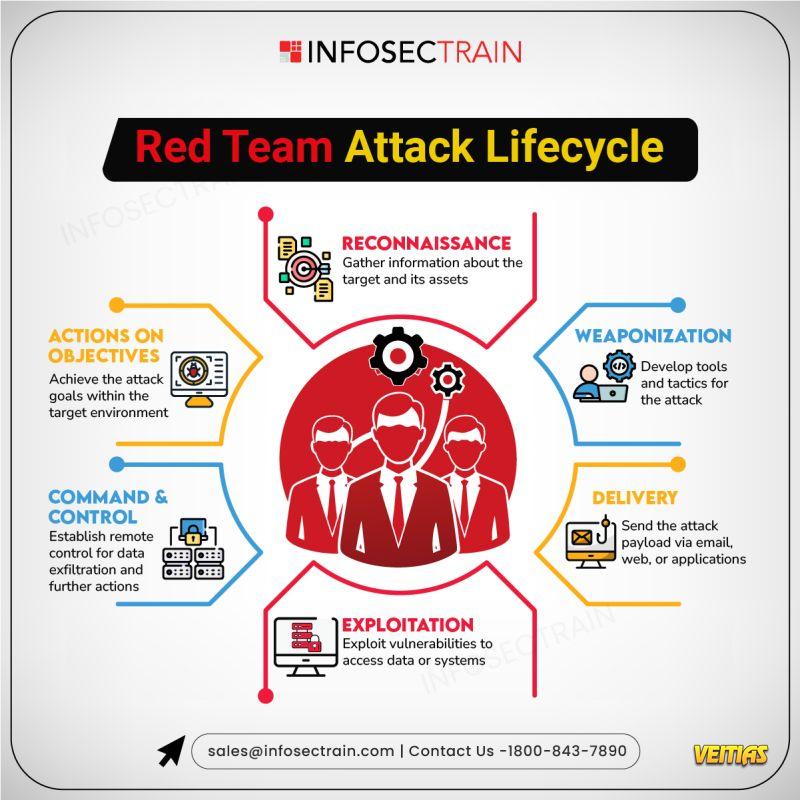
Red Team Attack Life Cycle
Understanding the MITRE ATT&CK Framework
Understanding Reconnaissance and Enumeration in Active Directory Environments.
Watch Here: https://youtu.be/2aFiSpS7kbQ?si=4yH7eleFSUoNS-15
Don’t miss out! Enroll here to join InfosecTrain Free Webinar and unlock expert insights. https://www.infosectrain.com/events/
#RedTeam #CyberSecurity #EthicalHacking #PenetrationTesting #RedTeamTraining #CyberAttacks #RedTeamVsBlueTeam #PurpleTeam #AdvancedRedTeam #CyberThreats #RedTeamTools
What You’ll Learn in This Masterclass: Day - 1
What is Red Teaming?
Red Teaming vs Penetration Testing
Types of Red Team Engagement
Red Team Attack Life Cycle
Understanding the MITRE ATT&CK Framework
Understanding Reconnaissance and Enumeration in Active Directory Environments.
Watch Here: https://youtu.be/2aFiSpS7kbQ?si=4yH7eleFSUoNS-15
Don’t miss out! Enroll here to join InfosecTrain Free Webinar and unlock expert insights. https://www.infosectrain.com/events/
#RedTeam #CyberSecurity #EthicalHacking #PenetrationTesting #RedTeamTraining #CyberAttacks #RedTeamVsBlueTeam #PurpleTeam #AdvancedRedTeam #CyberThreats #RedTeamTools
Red Team Masterclass: How Cyber Attacks Are Crafted & Executed [part 1]
🔑 What You’ll Learn in This Masterclass: Day - 1
✅ What is Red Teaming?
✅ Red Teaming vs Penetration Testing
✅ Types of Red Team Engagement
✅ Red Team Attack Life Cycle
✅ Understanding the MITRE ATT&CK Framework
✅ Understanding Reconnaissance and Enumeration in Active Directory Environments.
Watch Here: https://youtu.be/2aFiSpS7kbQ?si=4yH7eleFSUoNS-15
Don’t miss out! Enroll here to join InfosecTrain Free Webinar and unlock expert insights. 👉 https://www.infosectrain.com/events/
#RedTeam #CyberSecurity #EthicalHacking #PenetrationTesting #RedTeamTraining #CyberAttacks #RedTeamVsBlueTeam #PurpleTeam #AdvancedRedTeam #CyberThreats #RedTeamTools

0 Reacties
0 aandelen
3231 Views
0 voorbeeld