NIST CSF 2.0 vs CIS Benchmark
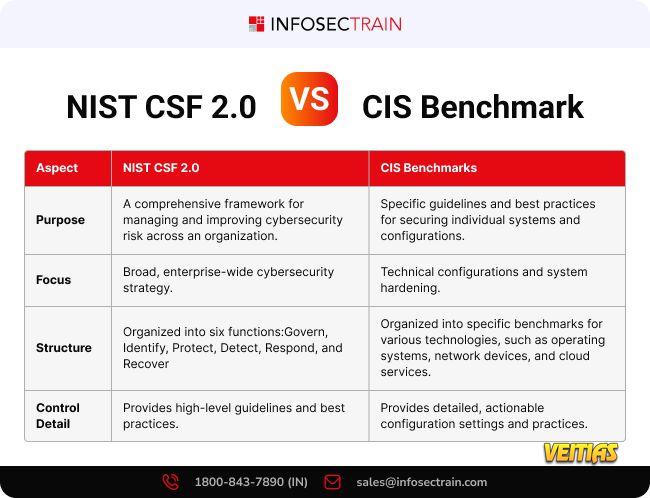
Understanding the difference between NIST CSF 2.0 and CIS Benchmarks is crucial for building a strong cybersecurity architecture! Here's a quick comparison to help you choose the right approach for your organization's needs.
Learn more: www.infosectrain.com
Contact us at 1800-843-7890 or sales@infosectrain.com to learn more!
#NISTCSF #CISBenchmark #CyberSecurity #RiskManagement #SecurityFramework #NISTFramework #SystemHardening #InfosecTrain #CyberBestPractices #TechSecurity #Compliance
Understanding the difference between NIST CSF 2.0 and CIS Benchmarks is crucial for building a strong cybersecurity architecture! Here's a quick comparison to help you choose the right approach for your organization's needs.
Learn more: www.infosectrain.com
Contact us at 1800-843-7890 or sales@infosectrain.com to learn more!
#NISTCSF #CISBenchmark #CyberSecurity #RiskManagement #SecurityFramework #NISTFramework #SystemHardening #InfosecTrain #CyberBestPractices #TechSecurity #Compliance
NIST CSF 2.0 vs CIS Benchmark
Understanding the difference between NIST CSF 2.0 and CIS Benchmarks is crucial for building a strong cybersecurity architecture! Here's a quick comparison to help you choose the right approach for your organization's needs.
🌐 Learn more: www.infosectrain.com
📞 Contact us at 1800-843-7890 or 📧 sales@infosectrain.com to learn more!
#NISTCSF #CISBenchmark #CyberSecurity #RiskManagement #SecurityFramework #NISTFramework #SystemHardening #InfosecTrain #CyberBestPractices #TechSecurity #Compliance
0 Commentarios
0 Acciones
2203 Views
0 Vista previa