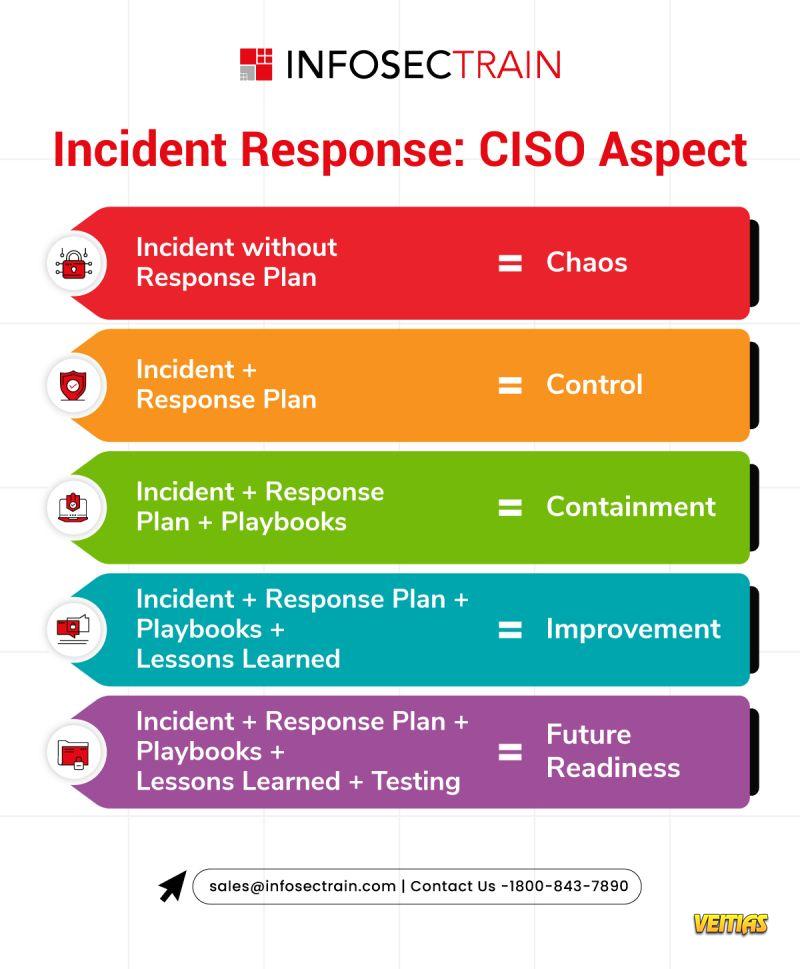
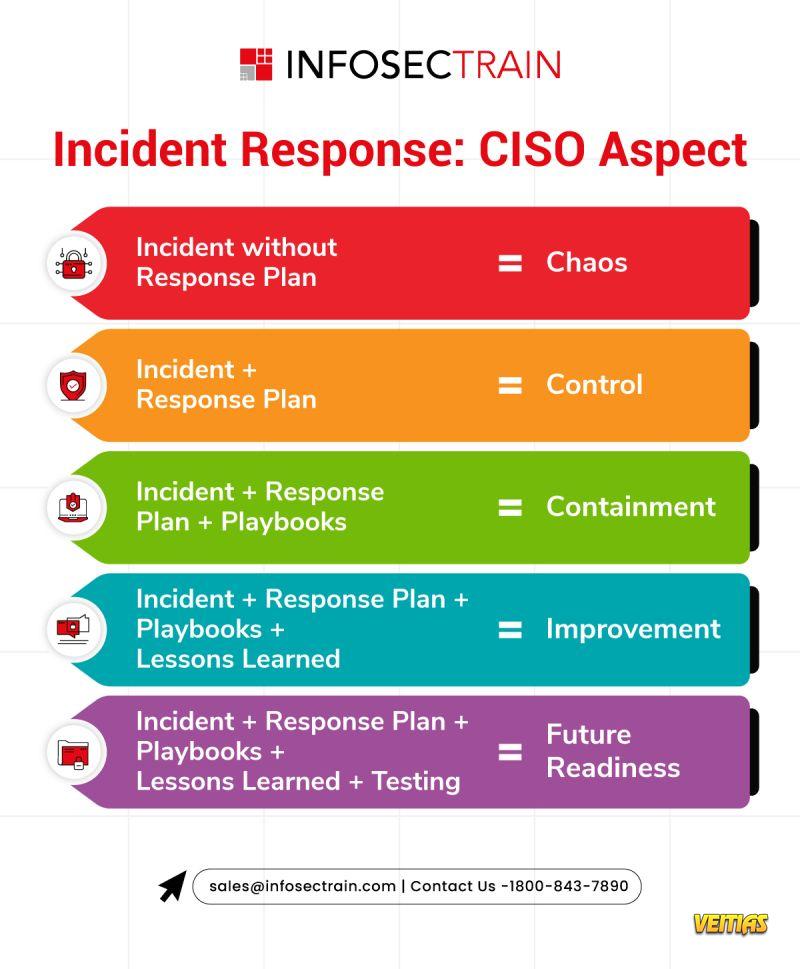
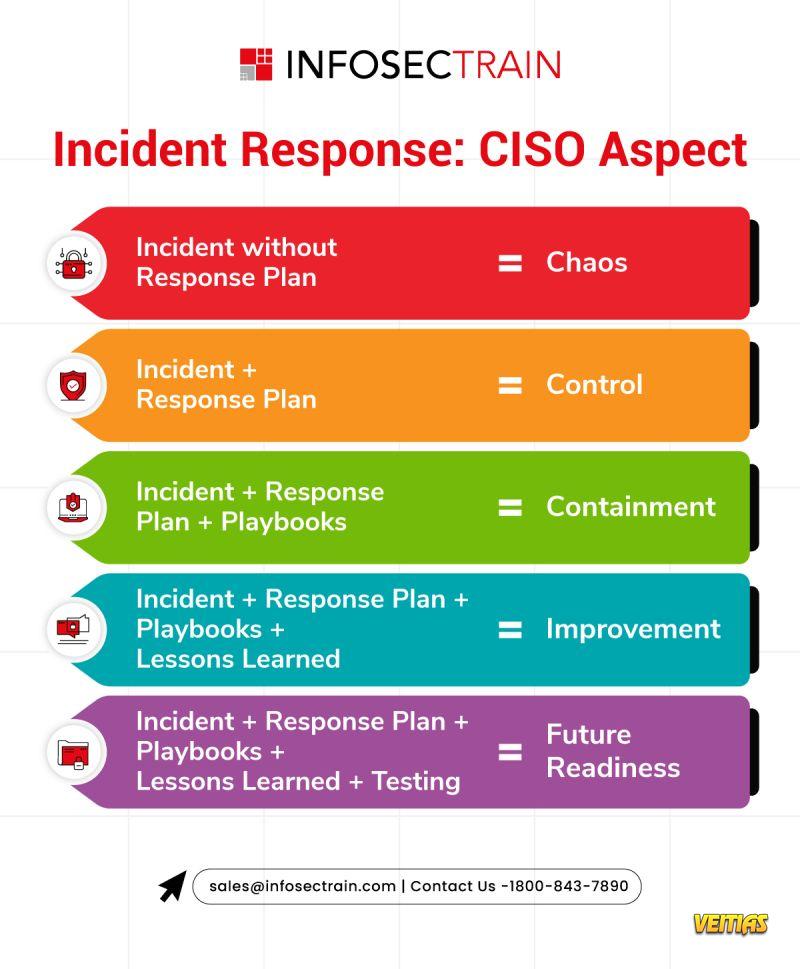
Key Incident Response Strategies for CISOs
Read more: https://www.infosectrain.com/tag/incident-response-tools/
#IncidentResponse #CISO #Cybersecurity #RiskManagement #DataBreach #IncidentManagement #SecurityLeadership #CyberAttack #TechSecurity #CrisisManagement #infosectrain #learntoris
Read more: https://www.infosectrain.com/tag/incident-response-tools/
#IncidentResponse #CISO #Cybersecurity #RiskManagement #DataBreach #IncidentManagement #SecurityLeadership #CyberAttack #TechSecurity #CrisisManagement #infosectrain #learntoris
Key Incident Response Strategies for CISOs
Read more: https://www.infosectrain.com/tag/incident-response-tools/
#IncidentResponse #CISO #Cybersecurity #RiskManagement #DataBreach #IncidentManagement #SecurityLeadership #CyberAttack #TechSecurity #CrisisManagement #infosectrain #learntoris
0 Commentarios
0 Acciones
6870 Views
0 Vista previa