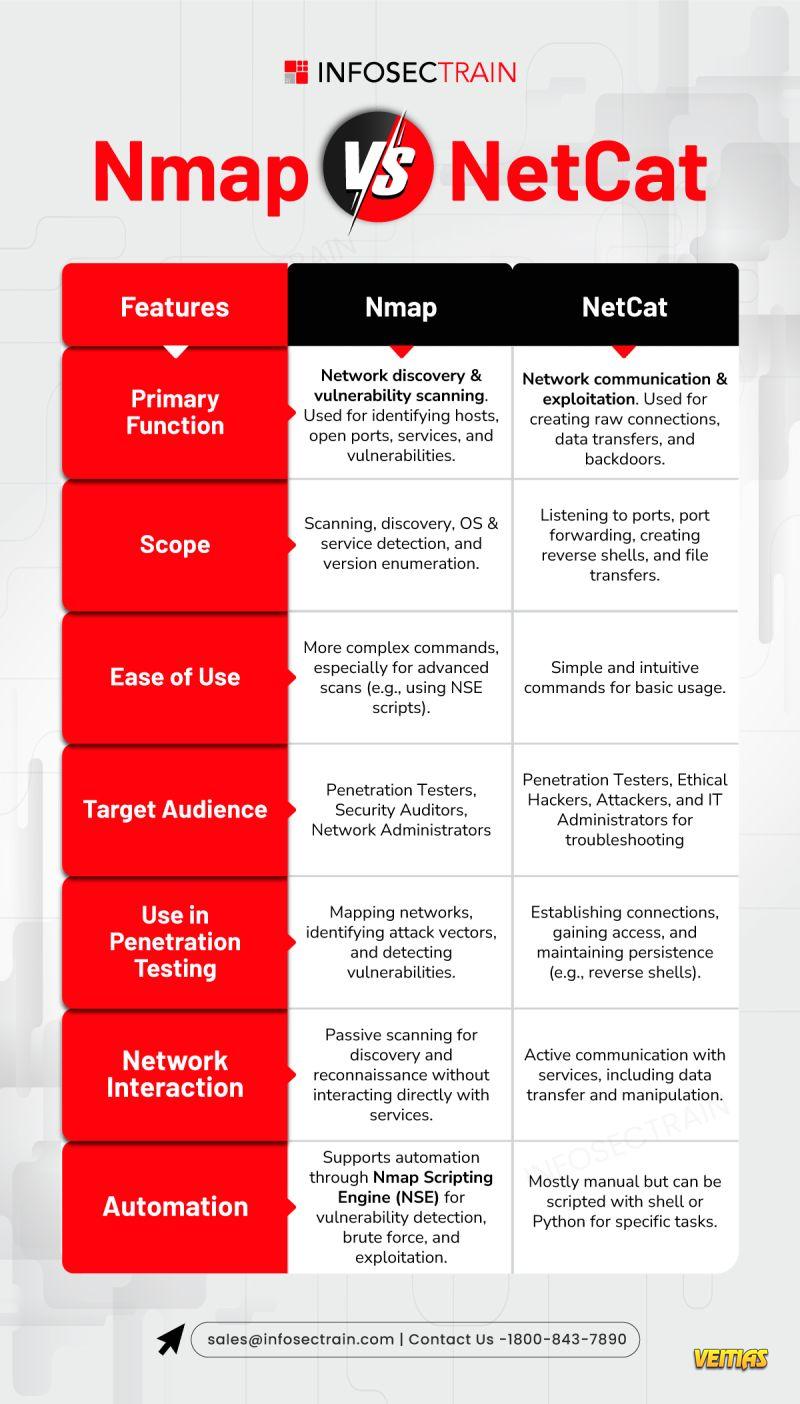
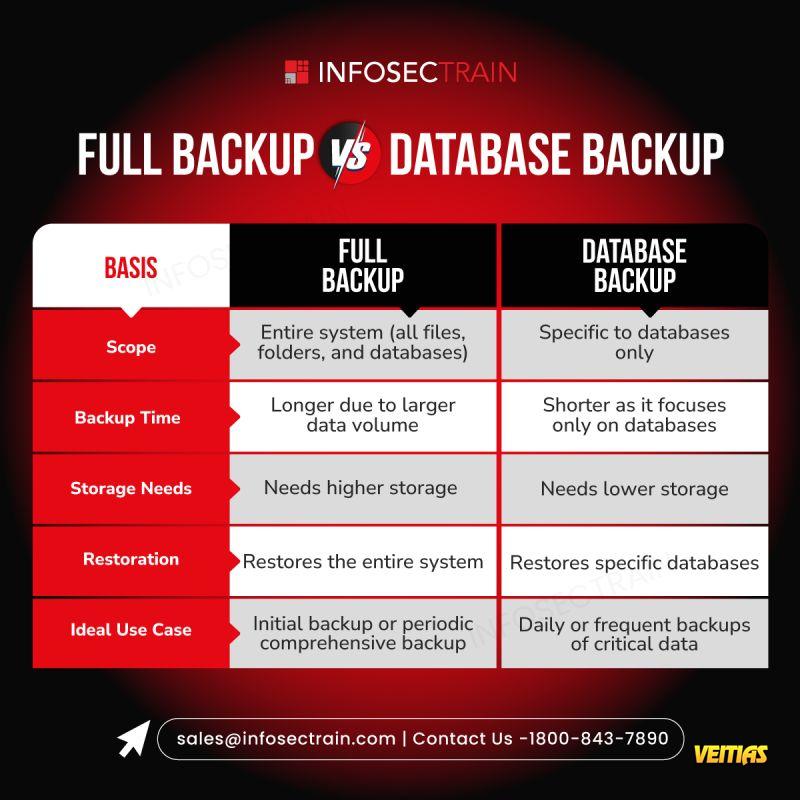
𝐔𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝𝐢𝐧𝐠 𝐆𝐃𝐏𝐑: 𝐏𝐫𝐨𝐭𝐞𝐜𝐭𝐢𝐧𝐠 𝐘𝐨𝐮𝐫 𝐃𝐚𝐭𝐚, 𝐎𝐧𝐞 𝐁𝐢𝐭𝐞 𝐚𝐭 𝐚 𝐓𝐢𝐦𝐞
In a world full of data sharing, businesses must prioritize privacy and transparency. Check out how GDPR principles align with real-world examples like Uber Eats. From consent to data security, see how they manage your info to keep things safe and fair.
Data protection starts with the basics — and a little knowledge goes a long way.
#GDPR #DataProtection #PrivacyFirst #DigitalRights #UberEats #DataSecurity #PrivacyMatters #TechEthics #ConsumerRights #Infosectrain #DataTransparency #TechTrends
In a world full of data sharing, businesses must prioritize privacy and transparency. Check out how GDPR principles align with real-world examples like Uber Eats. From consent to data security, see how they manage your info to keep things safe and fair.
Data protection starts with the basics — and a little knowledge goes a long way.
#GDPR #DataProtection #PrivacyFirst #DigitalRights #UberEats #DataSecurity #PrivacyMatters #TechEthics #ConsumerRights #Infosectrain #DataTransparency #TechTrends
𝐔𝐧𝐝𝐞𝐫𝐬𝐭𝐚𝐧𝐝𝐢𝐧𝐠 𝐆𝐃𝐏𝐑: 𝐏𝐫𝐨𝐭𝐞𝐜𝐭𝐢𝐧𝐠 𝐘𝐨𝐮𝐫 𝐃𝐚𝐭𝐚, 𝐎𝐧𝐞 𝐁𝐢𝐭𝐞 𝐚𝐭 𝐚 𝐓𝐢𝐦𝐞 🍔💻
In a world full of data sharing, businesses must prioritize privacy and transparency. Check out how GDPR principles align with real-world examples like Uber Eats. From consent to data security, see how they manage your info to keep things safe and fair.
🔒 Data protection starts with the basics — and a little knowledge goes a long way.
#GDPR #DataProtection #PrivacyFirst #DigitalRights #UberEats #DataSecurity #PrivacyMatters #TechEthics #ConsumerRights #Infosectrain #DataTransparency #TechTrends
0 Комментарии
0 Поделились
217 Просмотры
0 предпросмотр