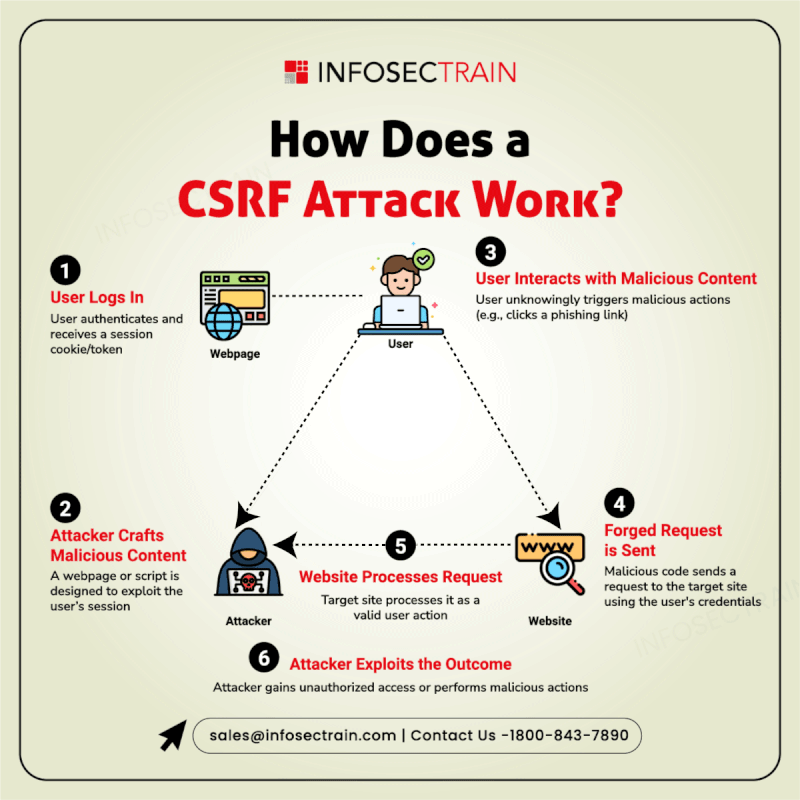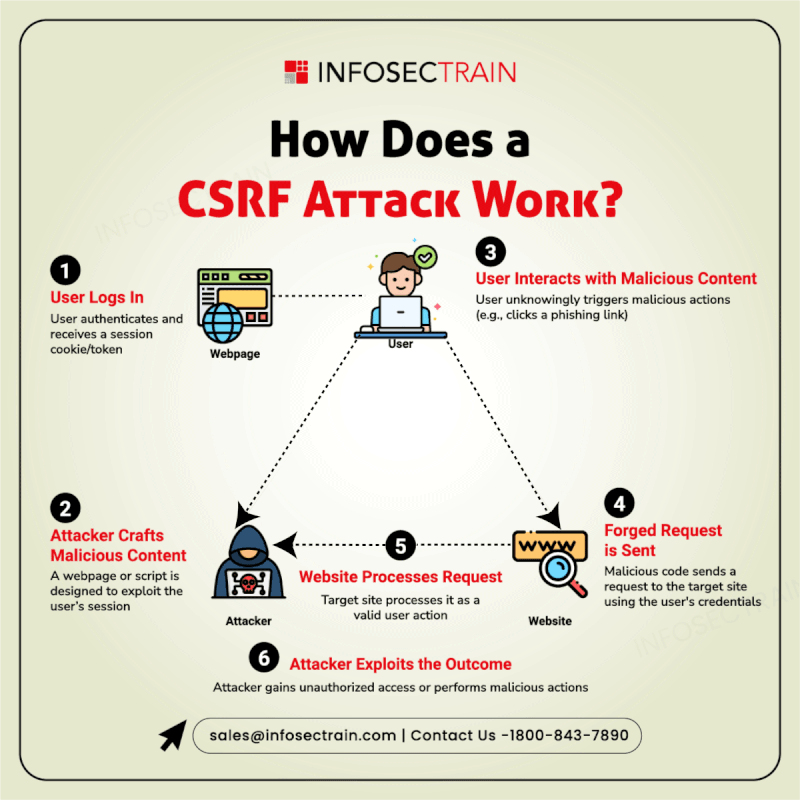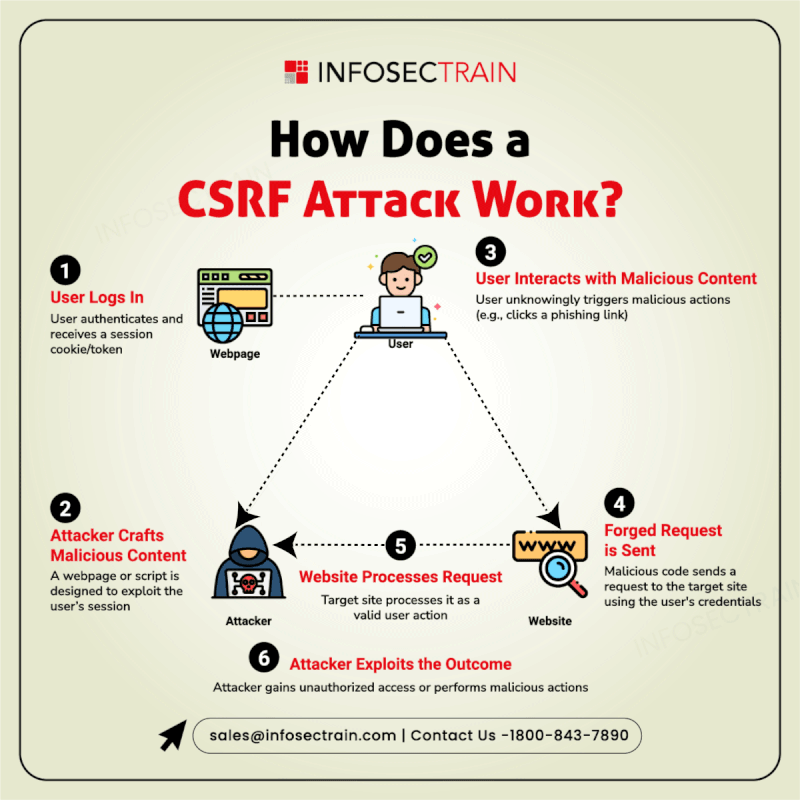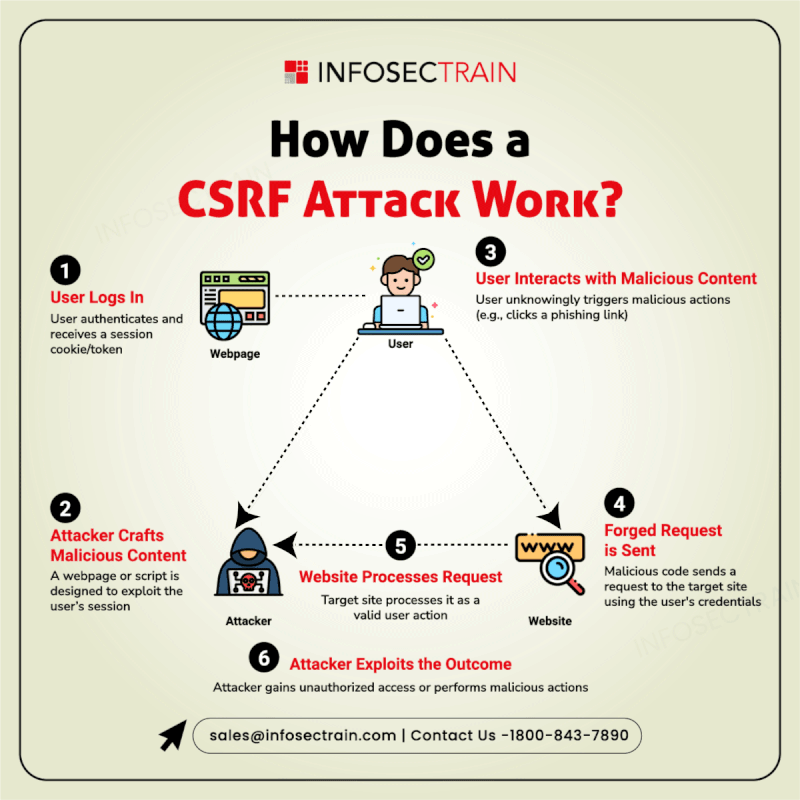
Want to know how a Web Application Firewall (WAF) functions?
Think of a WAF as a security guard for your website that monitors the traffic flowing in and blocks any attacks on your site. It acts as a shield by scrutinizing the information for threats such as SQL injections, cross-site scripting, and other exploits before they affect your site.
Read Here: https://medium.com/@Infosec-Train/how-waf-works-8e4de384d0da
#CyberSecurity #WAF #WebApplicationFirewall #InfoSecTrain #NetworkSecurity #CyberAwareness #DataProtection #SecureWeb #CyberDefense #WebSecurity
Think of a WAF as a security guard for your website that monitors the traffic flowing in and blocks any attacks on your site. It acts as a shield by scrutinizing the information for threats such as SQL injections, cross-site scripting, and other exploits before they affect your site.
Read Here: https://medium.com/@Infosec-Train/how-waf-works-8e4de384d0da
#CyberSecurity #WAF #WebApplicationFirewall #InfoSecTrain #NetworkSecurity #CyberAwareness #DataProtection #SecureWeb #CyberDefense #WebSecurity
Want to know how a Web Application Firewall (WAF) functions?
Think of a WAF as a security guard for your website that monitors the traffic flowing in and blocks any attacks on your site. It acts as a shield by scrutinizing the information for threats such as SQL injections, cross-site scripting, and other exploits before they affect your site.
Read Here: https://medium.com/@Infosec-Train/how-waf-works-8e4de384d0da
#CyberSecurity #WAF #WebApplicationFirewall #InfoSecTrain #NetworkSecurity #CyberAwareness #DataProtection #SecureWeb #CyberDefense #WebSecurity
0 Comments
0 Shares
6126 Views
0 Reviews